iThemes Security Pro Feature Spotlight – File Change Detection
In the Feature Spotlight posts, we will highlight a feature in the iThemes Security Pro plugin and share a bit about why we developed the feature, who the feature is for, and how to use the feature. Today we are going to cover File Change Detection, a great way to keep track of changes made on your WordPress website.

In the Feature Spotlight posts, we will highlight a feature in the iThemes Security Pro plugin and share a bit about why we developed the feature, who the feature is for, and how to use the feature.
Today we are going to cover File Change Detection, a great way to keep track of changes made on your WordPress website.
3 Reasons You Need File Change Detection For Your WordPress Site
Even if you follow the WordPress security best practices, there is still a chance for your site to become compromised. A compromise means that a hacker breached your website and infected it with malware.
1. A security breach can happen to even the most vigilant site owners.
A security breach is when a cybercriminal is able to gain unauthorized access to your website or server. Security breaches can happen in lots of different ways, as hackers exploit some of the most common WordPress security issues. From running outdated versions of plugins and themes to more complicated SQL injections, a security breach can happen to even the most vigilant site owners.
2. The time it takes to detect a security breach is a key factor in cleaning an infected website.
Did you know that the average time it takes to discover a website breach is 200 days? Unfortunately, the longer it takes you to notice a breach, the more damage a hacker can do to your website, your customers, and you. A piece of malware can cause a staggering amount of damage in 200 days. That’s why it’s so important to reduce the time it takes to spot a security breach.
The average time it takes to discover a breach is 200 days! The longer it takes you to notice a breach, the more damage a hacker can do to your website. And a piece of malware can cause a staggering amount of damage in 200 days.
Why? The cleanup and downtime you will need to clean your website after 200 days worth of damage is also staggering. The time to investigate everything the malware touched and which customer’s data was stolen only increases while the breach remains undetected. Not to mention the time you will have to spend informing customers that they need to cancel their credit cards because a hacker logged all of their keystrokes while they visited your website.
The cost of getting hacked is great. You have to pay someone to investigate the breach and clean your website. The hack repair specialist will have to take your website down while they work, and people won’t be able to make new purchases while your website is down. After losing your customer’s trust, you will likely lose any future purchases they would have given you.
The cost of a hack is why it is crucial to notice a breach as soon as possible. The faster you discover the breach, the quicker you can stop any further damage being done, and the faster you can get your website and business back online.
3. Malware scanners aren’t simply aren’t enough.
Malware scanners provide a way to scan your site for known malicious files and scripts. But are malware scanners enough to spot a security breach?
In a word, no. Don’t think that you can rely solely on a malware scanner to check if your website is infected. No malware scanner can identify every piece of malware that exists. If you come across a malware scanner that claims it is 100% accurate, you should run because scans that make claims like this are often the least accurate out there.
Malware Signatures
The majority of malware scans and antivirus software use malware signatures to detect malware. More advanced malware scans will use a combination of signature detection and behavioral analysis.
A malware signature is a series of bytes that are used to identify known pieces of malware. Some malware scanners are powered by a database filled with the malware signatures of millions of known viruses.
Signature-based malware scanning is fast, simple, and will detect 100% of known and well-understood pieces of malware. All of that is great and will catch malware added by low-level hackers.
However, skilled hackers know that malware scanners check for signatures of known malware. These hackers have the ability to obfuscate malware signatures to remain undetected by your average scanner.
New malware is released at a rate that malware scanners can’t keep their database updated with all of the latest signatures. So a signature-based scanner won’t be able to tell the difference between a new bit of malware and a plugin’s readme.txt file.
Behavioral Analysis
Behavioral analysis checks a software’s actions to determine if it is malicious. There is a ton of different types of behaviors that can be deemed suspicious or malicious. For example, the iThemes Security Pro Site Scan leverages the Google Safe Browsing API to help keep websites safe. Google Safe Browsing will check to see if a piece of software is redirecting traffic to a known malicious site.
Again, there is no foolproof method of malware detection. But a combination of behavioral and signature checks will significantly increase your chances of being alerted to evidence of a security breach.
3 Types of Common Behavior All Malware Shares
We know how crucial it is to detect a security breach as soon as possible, and that relying solely on malware detection isn’t enough. So we wondered how iThemes Security Pro could reduce the time it takes for people to detect security breaches on their websites?
While the type of damage malware causes on your website varies greatly, what it does can be boiled down to one or a combination of the following three things.
- Adds Files – Malware in the form of spyware could add a malicious file that will record your customer’s keystrokes as they enter their credit card information.
- Removes Files – Some malware will remove a legitimate file and replace it with a malicious file of the same name.
- Modifies Files – Malware will try to hide its malicious code by hiding it in an existing file that it modifies.
Wouldn’t it be nice to be alerted to unexpected changes to your website so you can inspect them for signs of a security breach?
How File Change Detection Helps You Reduce the Time it Takes to Detect a Security Breach
The key to quickly spotting a security breach is monitoring file changes on your website.
The File Change Detection feature in iThemes Security Pro will scan your website’s files and alert you when changes occur on your website.
There are several legitimate reasons you would see new file change activity in your logs, but if the changes made were unexpected, you should take the time to ensure the changes were not malicious. For example, if you see a change made to a plugin on the same date and time you updated the plugin, there would be no reason to investigate.
How to Enable File Change Detection in iThemes Security Pro
To start monitoring file changes, navigate to the security settings’ Features menu and enable File Change Detection.
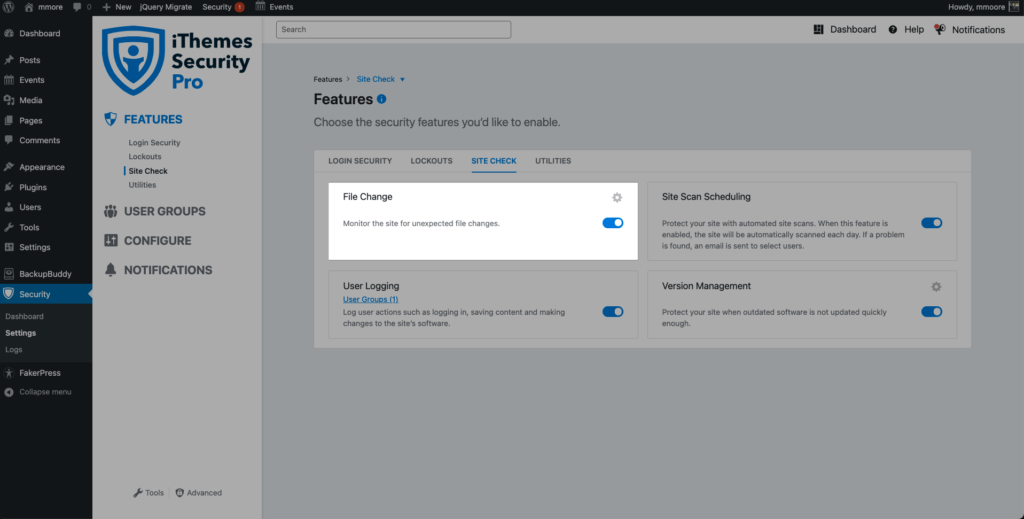
Once File Change Detection is enabled, iThemes Security Pro will start scanning all of your website’s files in chunks. Scanning your files in chunks will help to reduce the resources required to monitor file changes.
The initial file change scan will create an index of your website’s files and their file hashes. A file hash is a shortened, nonhuman readable version of the content of the file.
After the initial scan completes, iThemes Security Pro will continue to scan your file in chunks. If a file hash changes on one of the subsequent scans, that means the contents of the file have changed.
Activating File Change Notification Emails
File changes happen all the time, and getting an email alert for every change would quickly become overwhelming. And before you know it, it becomes a boy who cried wolf situation, and you start ignoring the file change alerts altogether.
Let’s take a look at how iThemes Security Pro intelligently identifies legitimated changes to reduce notifications and how you can mute notifications for files that are expected to update frequently.
To manage File Change notifications, navigate to the security settings’ Noftification menu and select File Change.
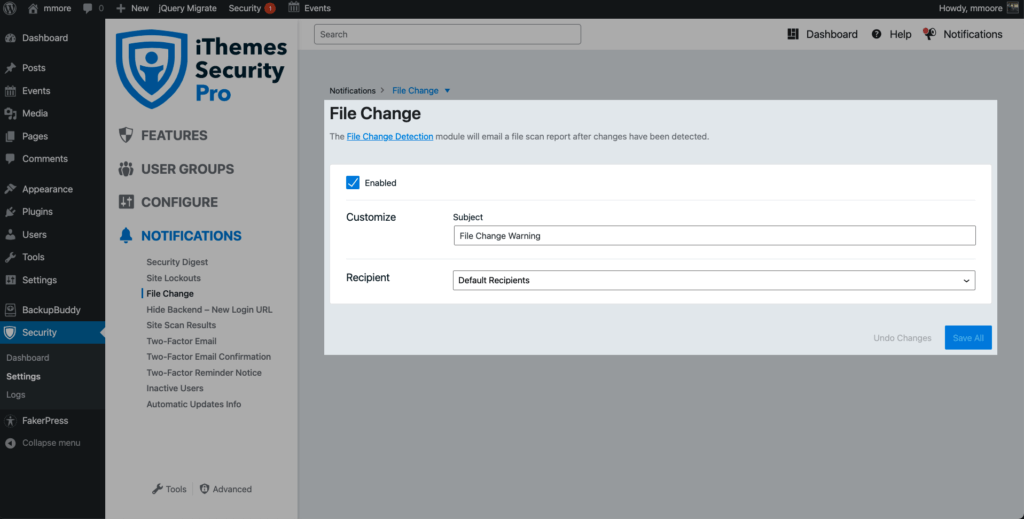
How iThemes Security Pro Identifies Legitimate File Changes
There are a couple of ways that iThemes Security Pro can detect if a change made to a file was legitimate and not a cause for concern. iThemes Security Pro will not create a File Change notification for changes it can verify.
1. Plugin/Theme Updates Completed By Version Management
The Version Management feature in iThemes Security Pro allows you to auto-update WordPress, plugins, and themes.
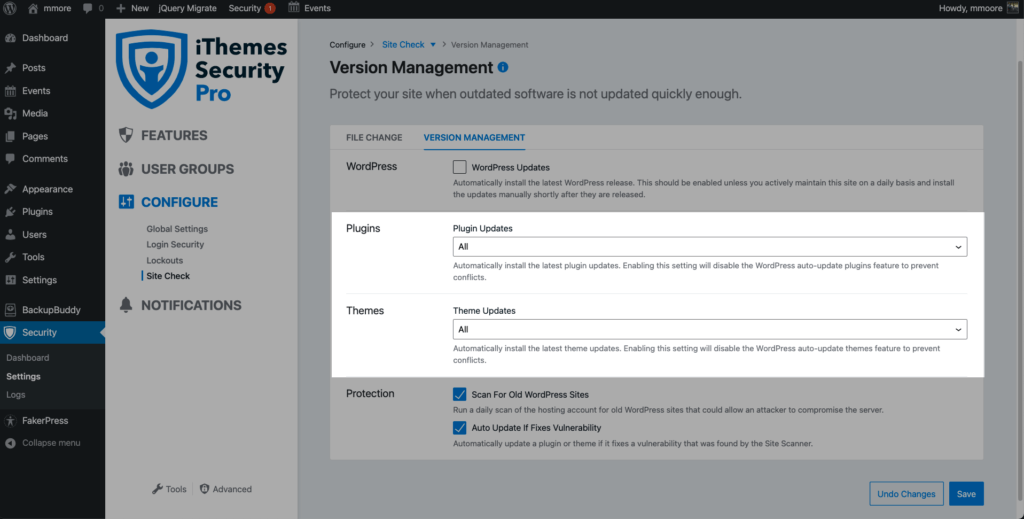
If an update is completed by Version Management, iThemes Security Pro will know the source of the update and won’t trigger an alert.
2. File Comparison for iThemes Plugins & Themes
Check the Compare Files Online box in the File Change Detection settings to enable online file comparison.
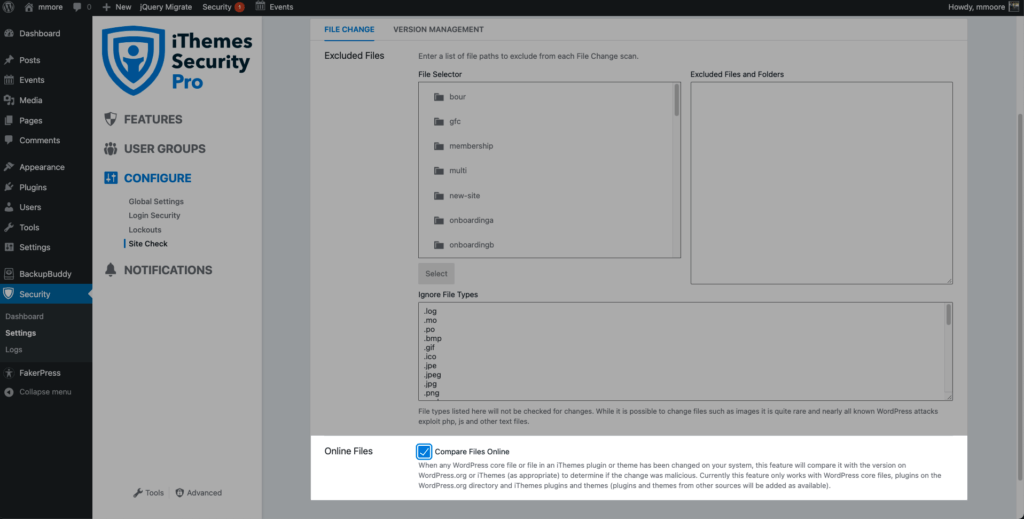
Any time a file on your website belonging to an iThemes plugin or theme is changed, it will get compared to a file on the iThemes server. If the hash to the version of the file on your website matches the hash to version on the iThemes server, it will be a legitimate change, and you will not receive an alert.
3. WordPress.org Online File Comparison
If a WordPress core file or a plugin installed from the WordPress.org repository is changed, the file will be compared with the version on WordPress.org. If the hashes match, the changes are not malicious, and you won’t receive an alert.
4. Manual Exclusions
You can exclude files, directories, and file types from File Change Detection in the File Change Detection settings.
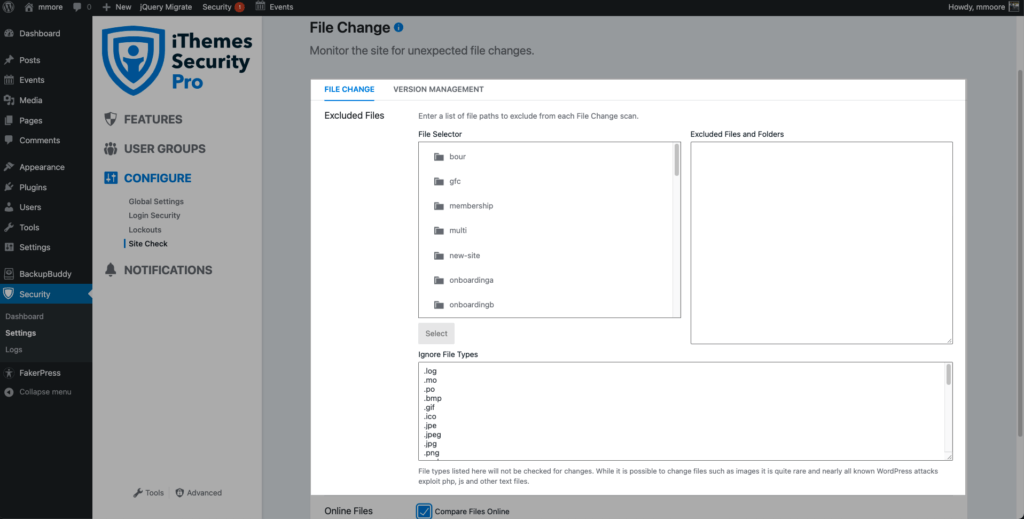
The general rule is it’s okay to exclude files that you know are going to be regularly updating. Backup and cache files are a perfect example of this. Excluding these types of files will calm a lot of the extra noise.
What To Do If You Spot a Security Breach or Hack
If you get a notification from iThemes Security that a suspicious file change has occurred and you suspect a breach has happened, there are a few quick steps you can take to mitigate the damage.
Restore to a Previous/Clean Backup of Your Site
The most sure-fire way to undo a security breach is to restore your site back to a previous version, prior to the attack. That’s why having a comprehensive WordPress backup solution in place is so important. We recommend using BackupBuddy to schedule backups to run automatically so you always have a backup.
Just note that restoring a previous backup may still leave your site vulnerable to the same breach, so it’s important to also follow these steps.
Update All Out-Dated Plugins & Themes Immediately
A vulnerable plugin or theme may still be the culprit, so it’s important to IMMEDIATELY update all outdated plugins or themes. Even if you restore to a previous clean version of your website, the same vulnerabilities will still exist and can be hacked again.
You may also want to check that you aren’t running a vulnerable plugin or theme that is still without a patch from the developer. You will need to remove this plugin immediately.
Enable Two-Factor Authentication
If you aren’t using two-factor authentication to secure admin logins, activate it immediately. This added layer of security will help make sure unauthorized users can’t hack any admin accounts.
Seek Help For Professional Malware Removal
Often security breaches occur at the server-level (deeper than your WordPress installation), so you may need to contact a professional malware removal service. We recommend WeWatchYourWebsite for professional malware removal.
Wrapping Up
It’s crucial to detect a security breach as soon as possible. Relying solely on malware scanners to alert to security breaches isn’t enough. You need to also be on the lookout for suspicious behavior like malicious file changes.
File Change Detection can help you detect breaches sooner and greatly reduce the damage done by a successful hack.
A WordPress Security Plugin Can Help Secure Your Website
iThemes Security Pro, our WordPress security plugin, offers 50+ ways to secure and protect your website from common WordPress security vulnerabilities. With WordPress, two-factor authentication, brute force protection, strong password enforcement, and more, you can add an extra layer of security to your website.
Get iThemes Security Pro Now
Sign up now — Get SolidWP updates and valuable content straight to your inbox
Sign up
Get started with confidence — risk free, guaranteed