Solid Security Pro Feature Spotlight – User Logging
Logging is an essential part of your WordPress security strategy. Insufficient logging and monitoring can lead to a long delay in detecting a security risk or breach. The Open Web Application Security Project (OWASP) says the average time to detect a breach is over 200 days! That long period of time allows an attacker to compromise other systems, modify, steal, or destroy more data. For these reasons, "Insufficient Logging" landed on the OWASP Top 10 of web application security risks.
In Feature Spotlight posts, we highlight a feature in the Solid Security Pro plugin and share a bit about why we developed the feature, who the feature is for, and how to use the feature.
Today, we’re covering the User Logging feature in Solid Security Pro.
Why You Need User Logging for Your WordPress Website
Logging is an essential part of your WordPress security strategy. Insufficient logging and monitoring can lead to a long delay in detecting a security risk or breach. The Open Web Application Security Project (OWASP) says the average time to detect a breach is over 200 days! That long period of time allows an attacker to compromise other systems, modify, steal, or destroy more data. For these reasons, “Insufficient Logging” landed on the OWASP Top 10 of web application security risks.
Most breach studies show that the time to detect a breach is over 200 days! That amount of time allows an attacker to breach other systems, modify, steal, or destroy more data.
You should monitor and record several types of security events in your WordPress security logs, including brute force attacks, file changes, plugin vulnerabilities, and suspicious user activity. In this post, we are going to focus on user activity.
What is User Logging?
The User Logging feature automatically monitors and records specific user actions in the Solid Security Pro security logs.
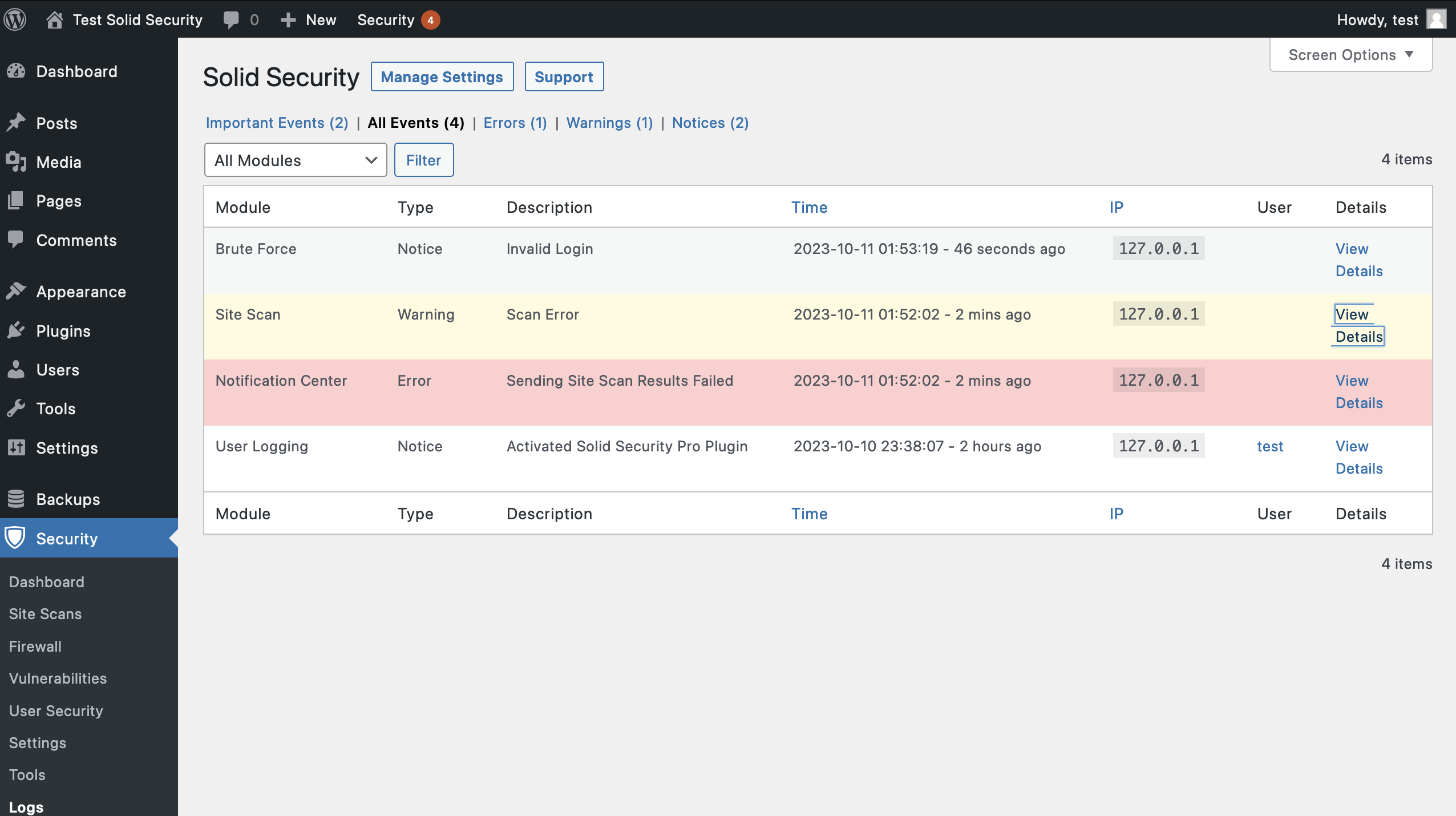
5 User Actions Recorded by Solid Security Pro
1. Log In / Log Out
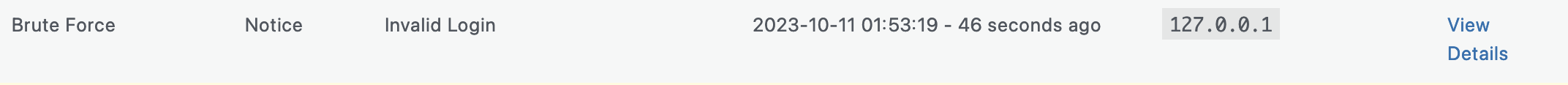
When users log in and out of your website, Solid Security Pro logs their activity and their IP addresses. Monitoring the time and location of user logins can help you spot a compromised user account. Did that user log in at an unusual time or from a new place? If so, you may want to investigate further, especially if they’re an editor or admin on your team.
2. User Creation / Registration

76.198.193.138 has registered a new user account username “hacker.”The next activity you should keep a record of is user creation, especially the creation of Administrator users. If a hacker can compromise a legitimate user account, they may be able to escalate its privileges or create a new admin user. Some vulnerabilities allow hackers to change the default new user role from a Subscriber to an Administrator.
This is why monitoring new user registrations is important!
If you have User Logging set only to monitor the activity of Administrator users, only new Admin user registrations will be recorded in the security logs. So, if you ever see a newly registered user in your security logs and you didn’t approve it, you know something has gone wrong.
3. Adding and Removing Plugins

mmoore deleted a plugin.It is vital to make a record of who adds and removes plugins. Once your site has been hacked, it will be easy for the attacker to add their custom plugin to inject malicious code into the website.
Even if a hacker doesn’t have access to your server or database, they may still be able to change them from your WordPress dashboard. Using a plugin, they can add redirects to your site to use in their next spamvertizement campaign or inject malware into your database. After their malicious code is executed, they can delete the plugin to remove evidence of their crime. Lucky for us, we won’t miss any of it because it was all documented in our WordPress security logs.
4. Switching Themes

mmoore switched the active theme.Another user activity monitored by Solid Security Pro User Logging is when someone switches the website’s theme. If you ever find that your theme has unexpectedly changed, you can look in your WordPress security logs to find out who made the change.
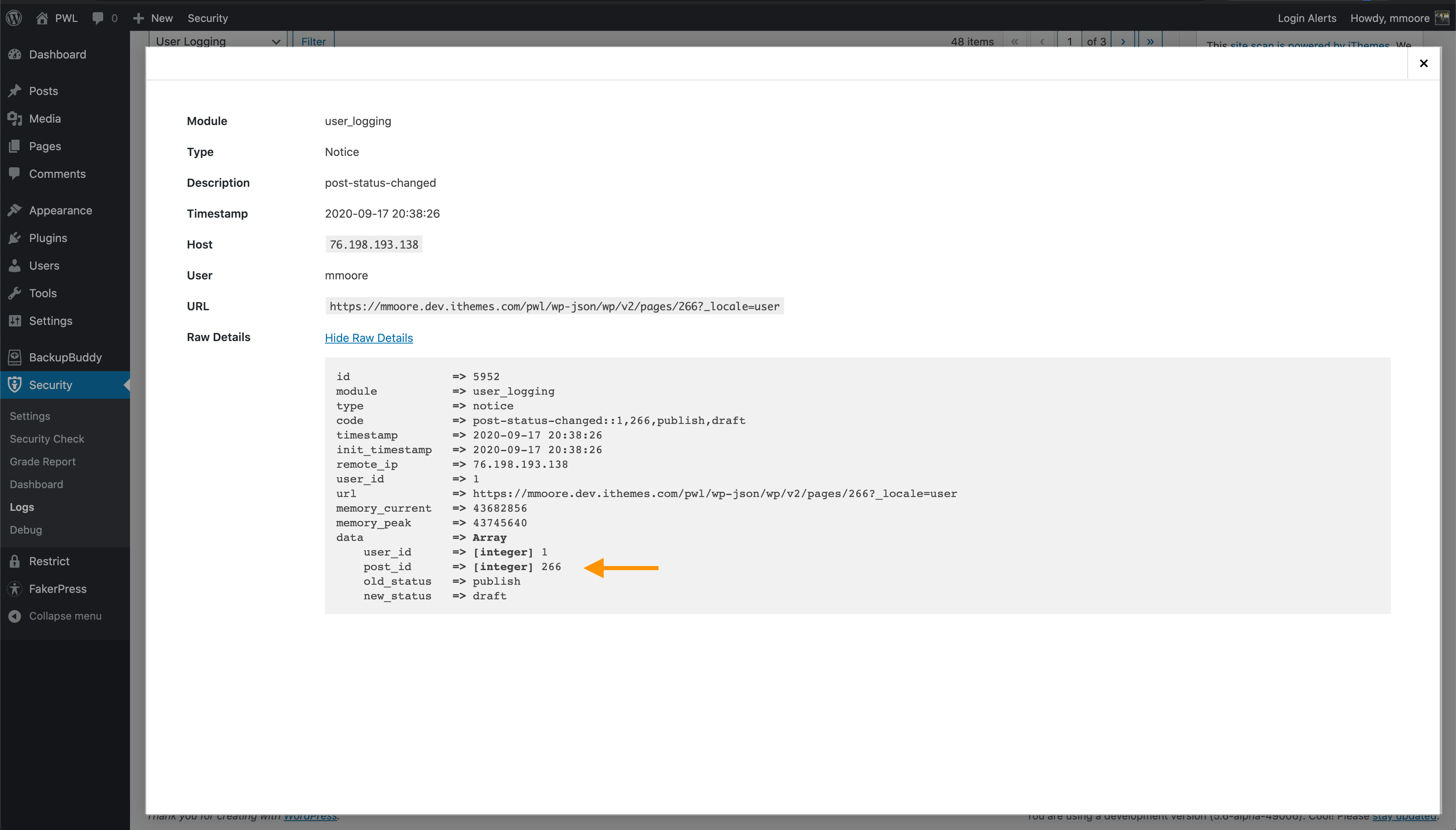
5. Changes to Posts & Pages

Finally, you want to monitor any changes to your posts and pages. Have any links been added to send your traffic to other sites? Monitoring posts and pages can help you find any embarrassing pages or malicious links added to your website after a breach.
To find out which post was modified, click the View Details links to find the post ID.
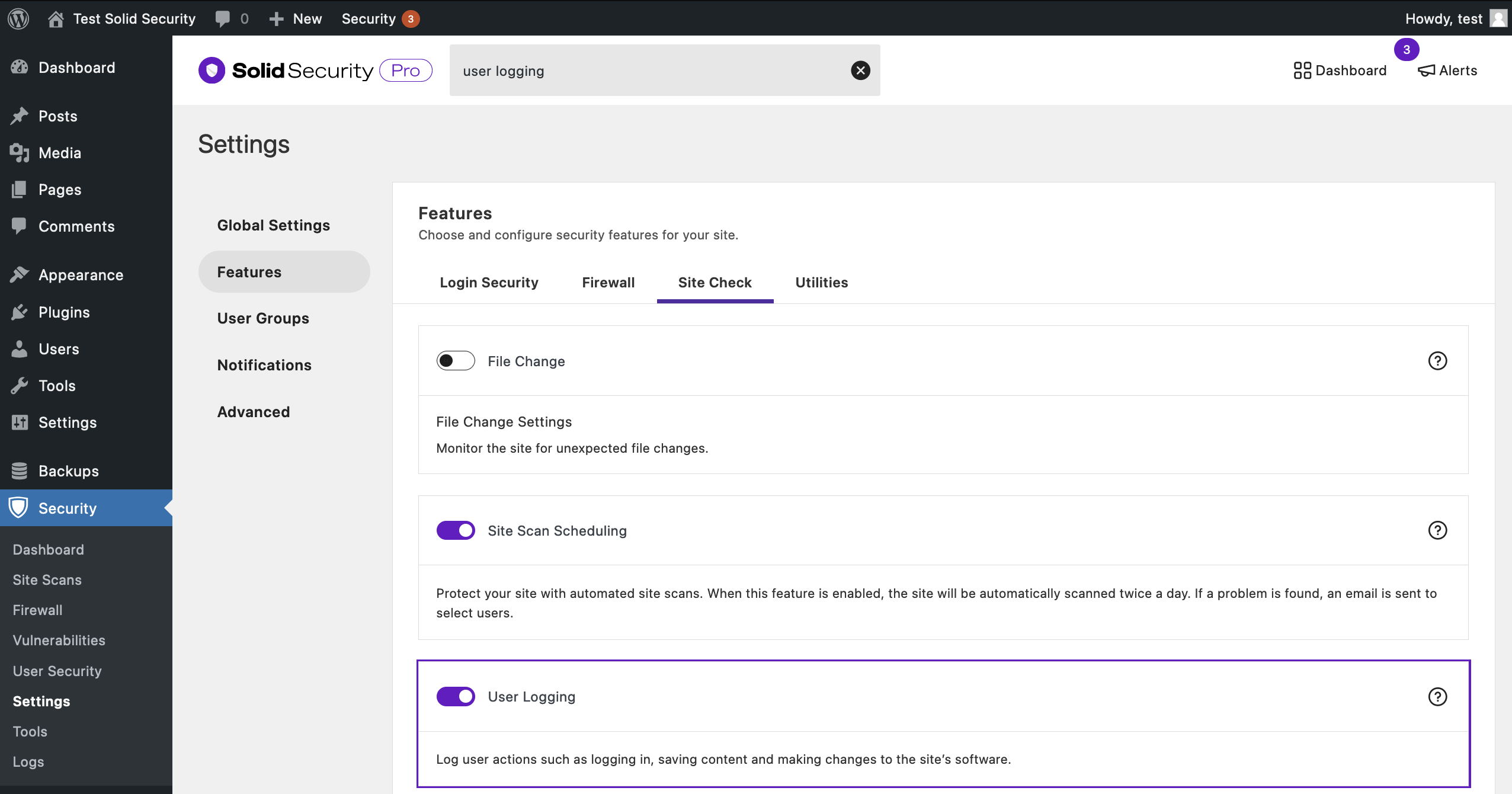
How to Use User Logging in Solid Security Pro
To start logging user actions in Solid Security Pro, navigate to the Security Settings’ Features menu and enable User Logging.
After enabling User Logging, click the User Groups link to decide whose activity you want to monitor.
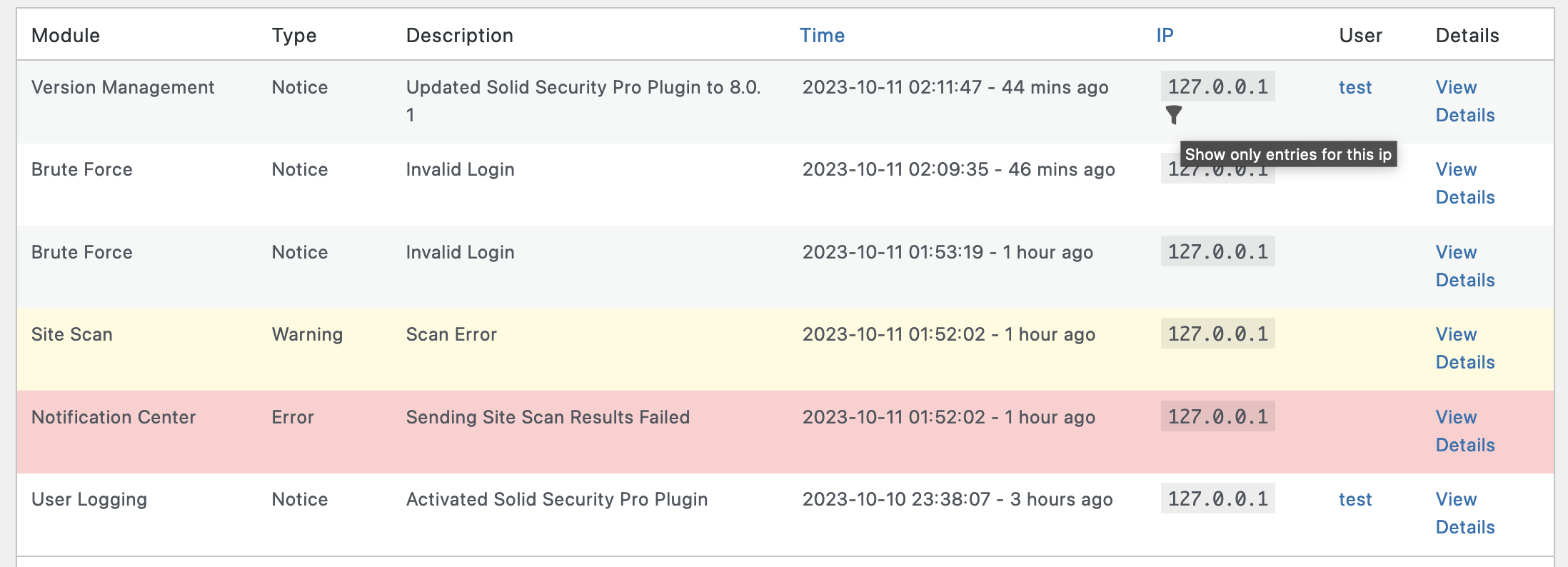
To view the recorded user activity, navigate to the security logs, and click the All Events link. Next, select User Logging from the dropdown menu and click the Filter button.
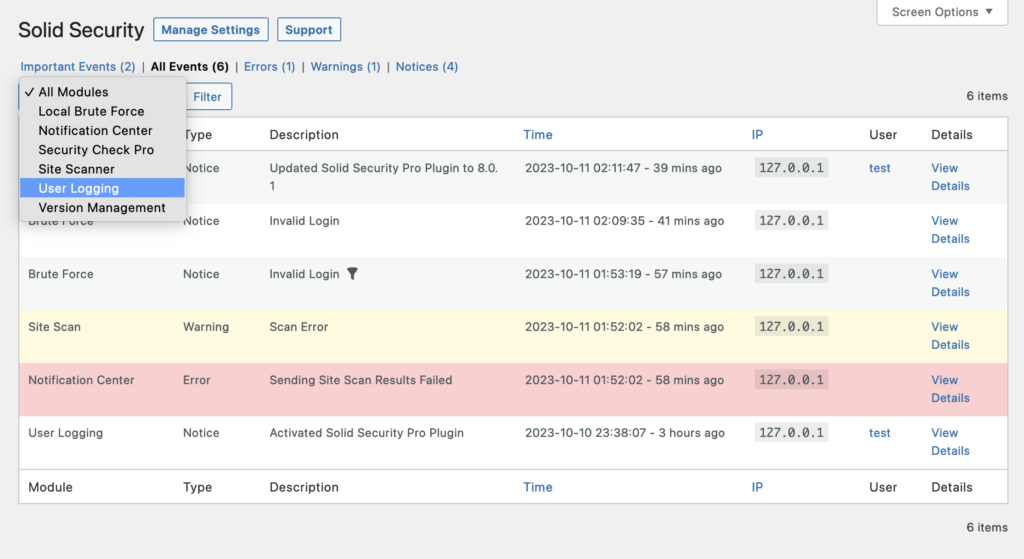
Hover over the IP address or Username and click the Filter icon to view only activity from that IP or username.
Wrapping Up
Unfortunately, even if you follow 100% of the WordPress security best practices and ensure your users do as well, there is still a small chance that attackers may compromise your website one day. Keeping a record of user activity in your WordPress security logs can alert you to this happening so you can shut down the compromised accounts quickly, possibly before they can do much harm, and then reverse any actions they took since these will be in your logs, too.
Sign up now — Get SolidWP updates and valuable content straight to your inbox
Sign up
Get started with confidence — risk free, guaranteed
