If you’re serious about your website’s security, then it’s time to learn about the dangers of remote code execution vulnerabilities and how you can combat them.
Remote code execution (RCE) refers to several different hacking techniques and cyberattacks, but they all have one major thing in common. RCE, sometimes called code injection, is an increasingly common way for hackers to compromise websites of all kinds, including sites that run WordPress as their content management system.
In this guide, we’ll explain in detail what a remote code execution attack looks like, and the steps you need to take to avoid one. Let’s take a look.
What Are Remote Code Execution (RCE) Attacks?
Remote Code Execution (RCE) is a type of vulnerability that allows a hacker to access and change a computer or database owned by someone else.
During an RCE attack, a hacker overtakes the server or computer through malware (arbitrary malicious software).
A remote code execution attack is carried out without the authority of the hardware owner, and it doesn’t matter where the data is stored in the world.
RCE Attacks Explained
It may be helpful to think of remote code execution attacks like termite infections:
- A termite digs in under a house.
- The homeowner doesn’t know it and definitely wouldn’t have invited the termite in if they had known about the damage they intended to do.
- The termite eats the foundation of the house until the house no longer stands.
While the metaphor isn’t exactly the same as how an RCE attack works, an RCE attack is actually worse. Unlike the termite that has to be at your house (or in it), a hacker can access your website from anywhere.
The fact is, RCE attacks are incredibly dangerous because hackers can execute any malicious code on a vulnerable server.
There’s really no limit to the damage a skilled RCE hacker can do to your WordPress site if they gain access to it.
Remote Code Execution Example
In 2018, Microsoft disclosed a remote code execution vulnerability found in the software program, Excel. An attacker could exploit the vulnerability to run arbitrary code in the current user’s context.
If the current user was logged on with administrative user rights, an attacker could take control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts were configured to have fewer user rights on the system could be less impacted than those with administrative user rights.

What Are the Different Types of Remote Code Execution?
To better understand RCE hacks, you need to be aware of the different types of remote code execution:
SQL Injections
Your WordPress website uses a MySQL database to operate. SQL injections occur when an attacker gains access to your WordPress database and your website data.
With an SQL injection, an attacker may be able to create a new admin-level user account which can then be used to log in and get full access to your WordPress website. SQL injections can also insert new data into your database, including links to malicious or spam websites.
Many RCE vulnerabilities attack the way that WordPress SQL statements are constructed. As an example, if an application needs to read database usernames, a developer might make the mistake of using code such as the below for a username search:
SELECT * FROM users WHERE name = 'username'
But what is the problem with a query like this related to RCE? Any visitor to your WordPress site, even hackers with bad intent, can enter a username. As an example, the hacker might enter ‘1”1’= –, OR ‘, which would result in an SQL statement like this:
SELECT * FROM users WHERE name = '1'='1' --' OR ''
Assuming that the application proceeds to search through the entire database for site usernames, and then selects each field where there is a blank name, when 1 is equal to 1, the latter is always true. What ends up happening is that the hackers are provided with every username within the SQL database.
However, A data leak like this isn’t the only danger with SQL injections. An attacker could also send many commands into the SQL database, which could overwrite or delete crucial WordPress site data.
Cross-Site Scripting
Cross-site scripting is yet another RCE vulnerability. It directly impacts site visitors, rather than your servers. Cross-site scripting (XSS) is a malware attack executed by exploiting cross-site vulnerabilities on any WordPress site. In fact, it’s the most common way for WordPress sites to be hacked because so many WordPress plugins have XSS vulnerabilities.
Within each webpage, code, and content are rendered in identical ways. However, a web browser can set code apart from content because it’s always wrapped in script tags. What this means is that, without a proper filter, attackers can stuff malicious code into any place on a webpage that allows text to be entered.
Without a proper filter, attackers are able to stuff malicious code into any place on a webpage that allows text to be entered. Are you protected?
This includes vulnerable fields such as search bars (often on every page of your WordPress site), comment sections, or even display names.
When this attack is executed, your website’s browser will run the malicious code.
Cross-site scripting wouldn’t be as big of a security issue if only executed on the attacker’s browser. However, when the malicious code is viewable to the public, such as in comment sections of your blog posts, it’ll also impact any visitor who views the content.
With this dangerous ability to execute any code remotely, an attacker can easily steal passwords and pretend to be legitimate users.
They can also potentially view that user’s personal information, such as credit card details or PayPal account info.
Directory Traversal
This attack isn’t targeted at an application or your WordPress site visitors. Instead, the main target is your actual website.
The RCE vulnerability exploits how site files are stored in the file system of your website server.
Normally, data is stored within a standard directory, like /home/user/public_html. The scripts within the directory access files by using a relative path, like wp-admin/index.php that directly refer to /home/user/public_html/wp-admin/index.php.
When a script is configured to access a file that’s outside of the current directory, it accomplishes this simply by including a “../”. This refers to the directory that’s one step above the current directory.
As an example, the directory pattern /home/user/public_html/../ is directed to /home/user/.
If a script is allowed to read or upload from any custom filenames, an attacker will direct the application toward traversing directories, with a name such as ../../../../../../../../../etc/passwd.
If you haven’t implemented important security features such as input filtering, the hacker can gain direct access to your server’s core files, which is bad news for your site security.
What Can You Do To Prevent Remote Code Execution (RCE) Attacks?
The detailed information in this guide isn’t meant to intimidate or cause you any fear. Rather, it’s intended to highlight the increasing importance of having the most robust WordPress site security measures running at all times.
It also serves as a reminder to keep your plugins updated to ensure they are not open to new RCE vulnerabilities.
The vast majority of RCE attacks can be mitigated or stopped completely just by being aware and prepared before they happen. As WordPress site owners, it’s important to anticipate and understand how our site servers process the information that our users provide.
How to Prevent Remote Code Execution (RCE) Attacks: 5 Steps
The number one way to ensure your site is secure from RCE vulnerabilities is to employ a multi-faceted defense system. In other words, even if one line of defense fails you, you’ll still remain protected from potential attack.
With that said, let’s look at some of the most important steps you should take to prevent these malicious and often dangerous attacks. Several factors can make your WordPress site more vulnerable to successful attacks.
1. Download and Install the Solid Security Pro Plugin
To get started securing and protecting your site, download and install the Solid Security Pro plugin.
2. Activate Version Management to Keep WordPress Core, Plugins and Themes Updated
Simply put: You’re putting yourself at risk for an attack if you are running outdated versions of WordPress, plugins, and themes on your website. Version updates often include patches for security issues in the code, including remote code execution (RCE) vulnerabilities, so it’s important always to run the latest version of all software installed on your WordPress website.
Updates will appear in your WordPress dashboard as soon as they’re available. Practice running a backup and running all available updates every time you log in to your WordPress site. While running updates may seem inconvenient or tiresome, it’s an important WordPress security best practice.
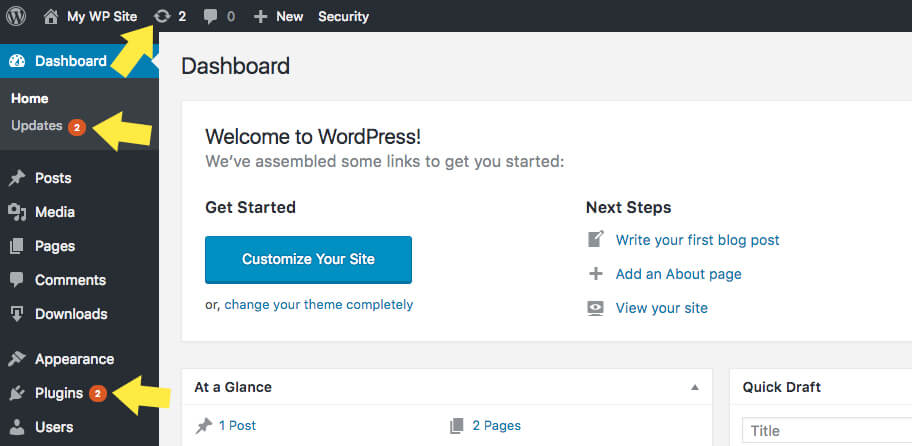
It is hard to keep track of every disclosed WordPress vulnerability—we keep track and share them in our WordPress Vulnerability Roundups—and compare that list to the versions of plugins and themes you have installed on your website. However, this doesn’t stop WordPress hackers from targeting plugins and themes with known vulnerabilities. Having software with known vulnerabilities installed on your site gives hackers the blueprints they need to take over your website.
The Version Management feature in the Solid Security Pro plugin allows you to auto-update WordPress, plugins, and themes. Beyond that, Version Management also has options to harden your website when you are running outdated software and scan for old websites.
To get started using Version Management, enable the module on the main page of the security settings.
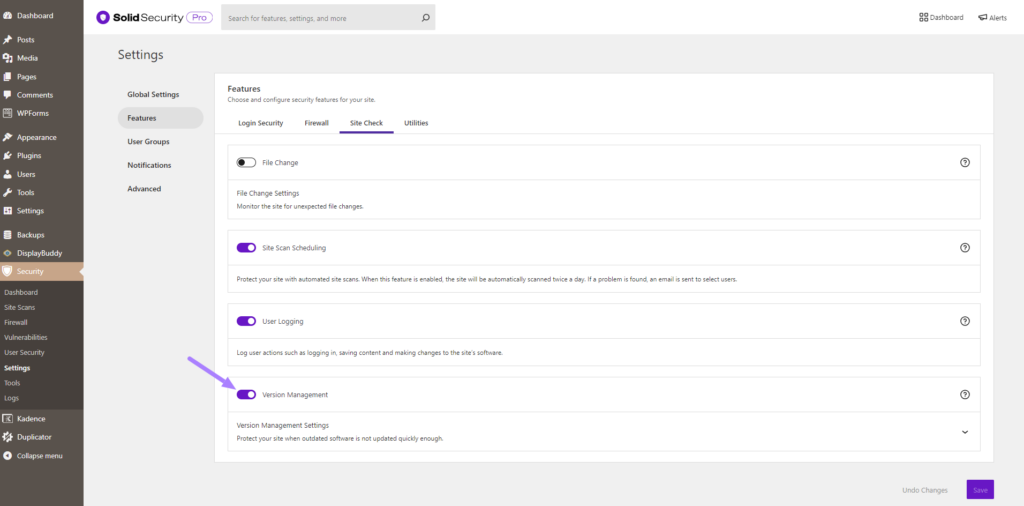
Now click the Down Arrow to take a closer look at the settings, all designed to protect your site.
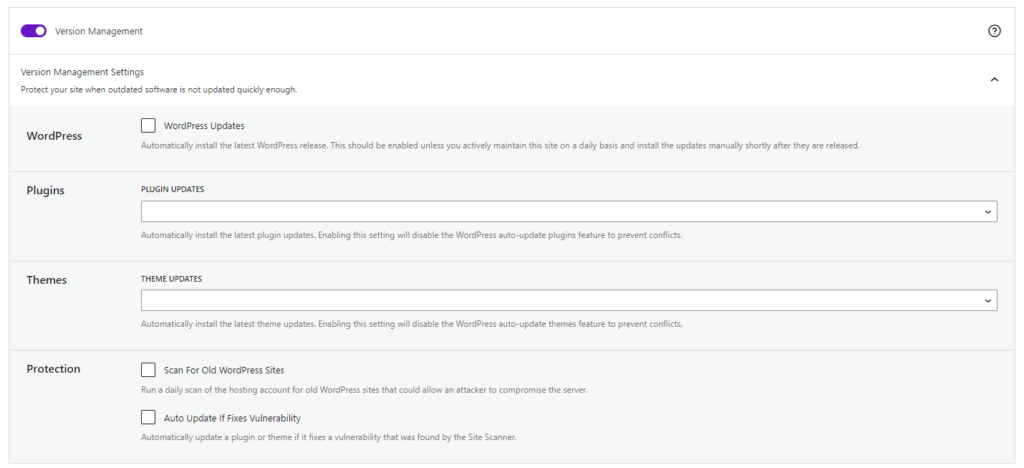
- WordPress Updates – Automatically install the latest WordPress release.
- Plugin Updates – Automatically install the latest plugin updates. Enabling this setting will disable the WordPress auto-update plugins feature to prevent conflicts.
- Theme Updates – Automatically install the latest theme updates. Enabling this setting will disable the WordPress auto-update theme feature to prevent conflicts.
- Scan For Old WordPress Sites – Run a daily scan of the hosting account for old WordPress sites that could allow an attacker to compromise the server. A single outdated WordPress site with a vulnerability could allow attackers to compromise all the other sites on the same hosting account.
- Auto Update If Fixes Vulnerability – This option works with the Solid Security Pro Site Scan to check your website for known WordPress, plugin, and theme vulnerabilities and apply a patch when one is available.
Plugin & Theme Updates
Now, let’s, take a closer look at configuring plugin and theme updates. Before we get started, just a quick reminder that enabling the plugin and theme update settings will disable the WordPress auto-update feature to prevent conflicts.
Both the Plugin and Theme Update Settings have three choices.
- Blank/None – Leaving the setting blank will allow WordPress to manage the plugin and theme updates.
- Custom – The Custom option allows you to customize the updates precisely to your liking. We will cover this more in just a bit.
- All – All will update all your plugins or themes as soon as an update is available.
Now let’s take a closer look at the Custom option.
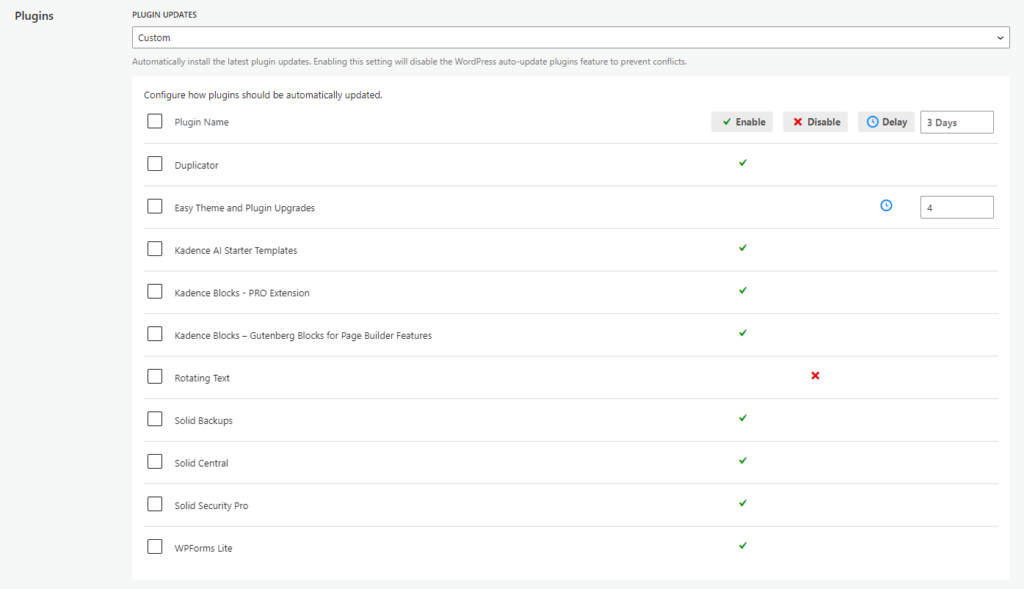
Selecting the Custom option provides three different choices for your plugin and theme updates. As we can see, the Custom auto-updates setting offers a lot more flexibility than WordPress’s on or off auto-update option.
3. Scan Your Site For Vulnerable Plugins and Themes
The Solid Security Pro Site Scanner is another way to secure and protect your WordPress website from the number one cause of all software hacks: outdated plugins and themes with known vulnerabilities. The Site Scanner checks your site for known vulnerabilities and automatically apply a patch if one is available.
The 3 Types of Vulnerabilities Checked
- WordPress Vulnerabilities
- Plugin Vulnerabilities
- Theme Vulnerabilities
To enable the Site Scan on new installs, navigate to the Solid Security Pro settings, select Features, and click the Enable toggle on the Site Check settings module.
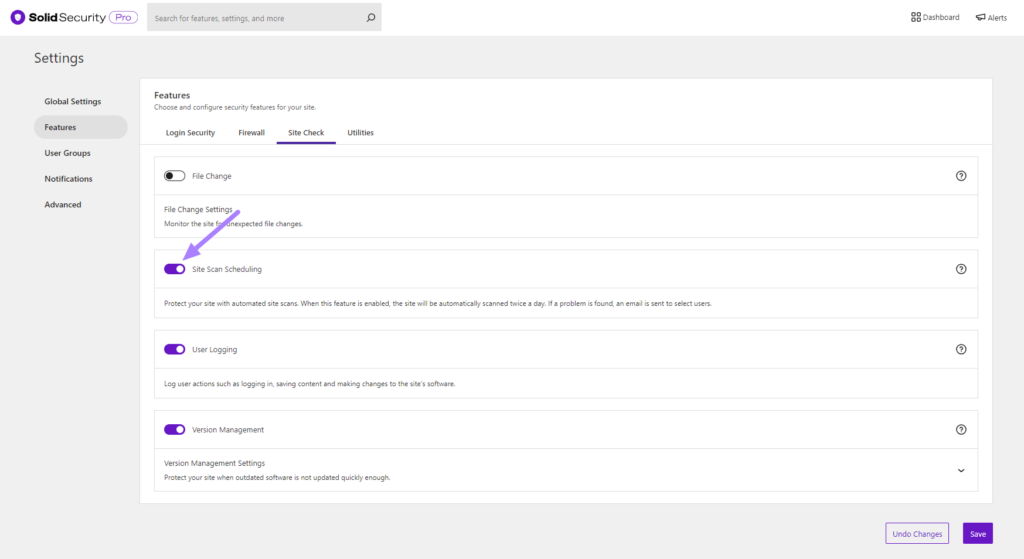
To trigger a manual Site Scan, click on Site Scans and then the Start Site Scan button located at the top right of the screen.
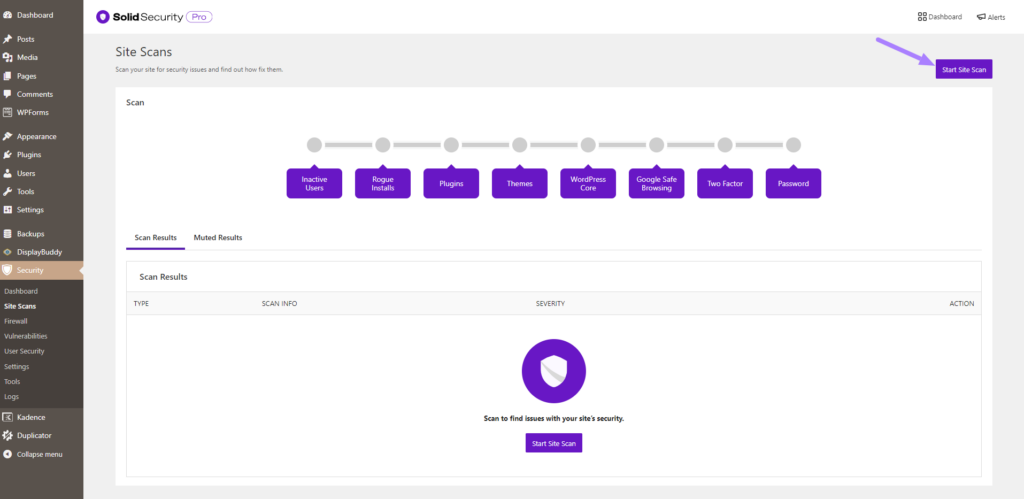
The Site Scan results will display.
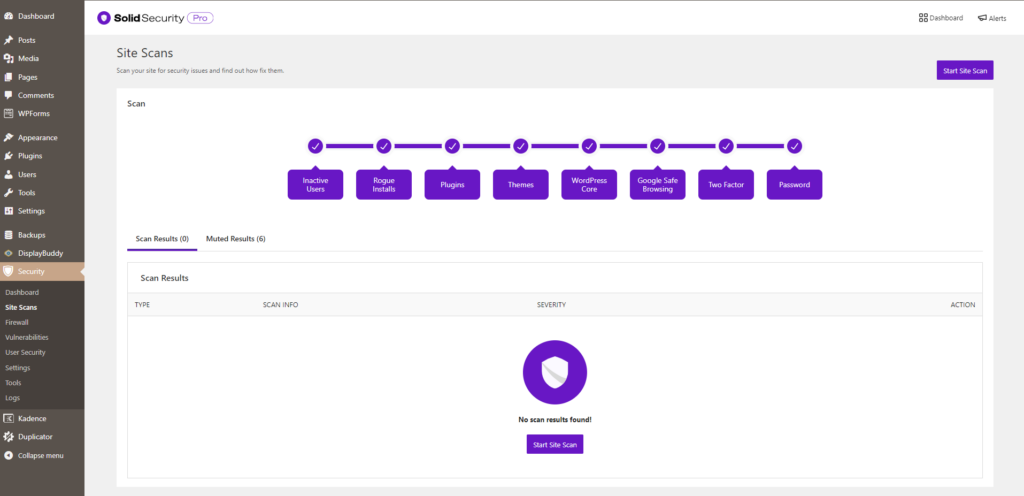
If the Site Scan detects a vulnerability, click the vulnerability link to view the details page.
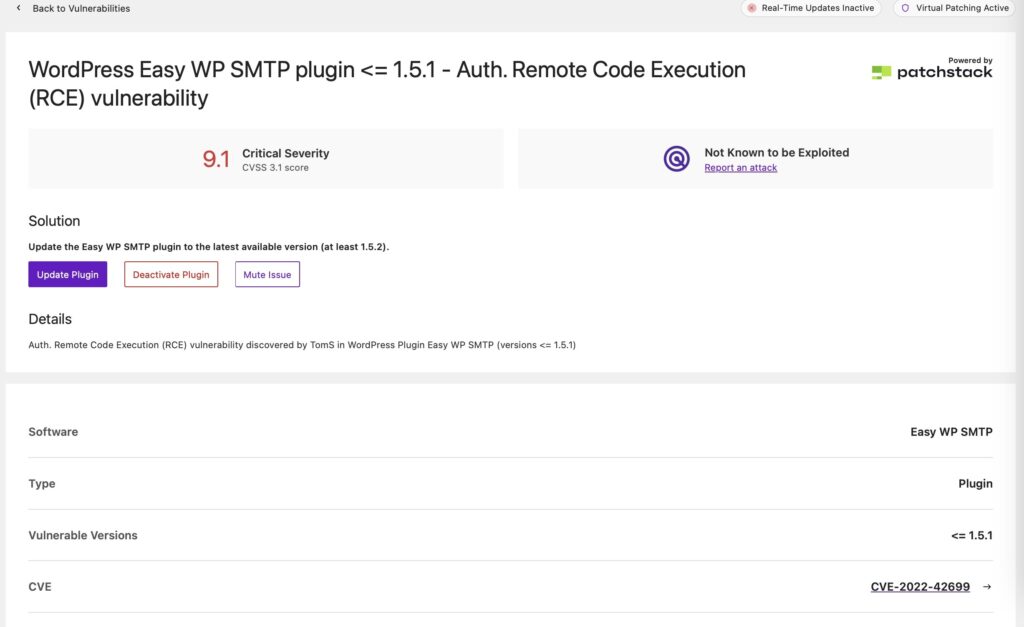
On the Site Scan vulnerability page, you will see if there is a fix available for the vulnerability. If there is a patch available, you can click the Update Plugin button to apply the fix on your website.
There can be a delay between when a patch is available and the Solid Security Vulnerability Database getting updated to reflect the fix. In this case, you can mute the notification to not receive any more alerts related to the vulnerability.
4. Prevent Session Hijacking
You should have session hijacking protection in place for your Admins and Editors on your WordPress website to protect yourself from remote code execution vulnerabilities.
The Solid Security Pro Trusted Devices feature makes Session Hijacking a thing of the past. If a user’s device changes during a session, Solid Security will automatically log the user out to prevent any unauthorized activity on the user’s account, such as changing the user’s email address or uploading malicious plugins.
The Trusted Devices feature in Solid Security Pro works to identify the devices that you and other users use to login to your WordPress site. After your devices are identified, we can stop session hijackers and other bad actors from doing any damage on your website.
When a user has logged in on an unrecognized device, Trusted Devices can restrict their administrator-level capabilities. This means that if an attacker were able to break into the backend of your WordPress site, they wouldn’t have the ability to make any malicious changes to your website.
To start using Trusted Devices, enable them on the main page of the security settings, and then click the Configure Settings button.
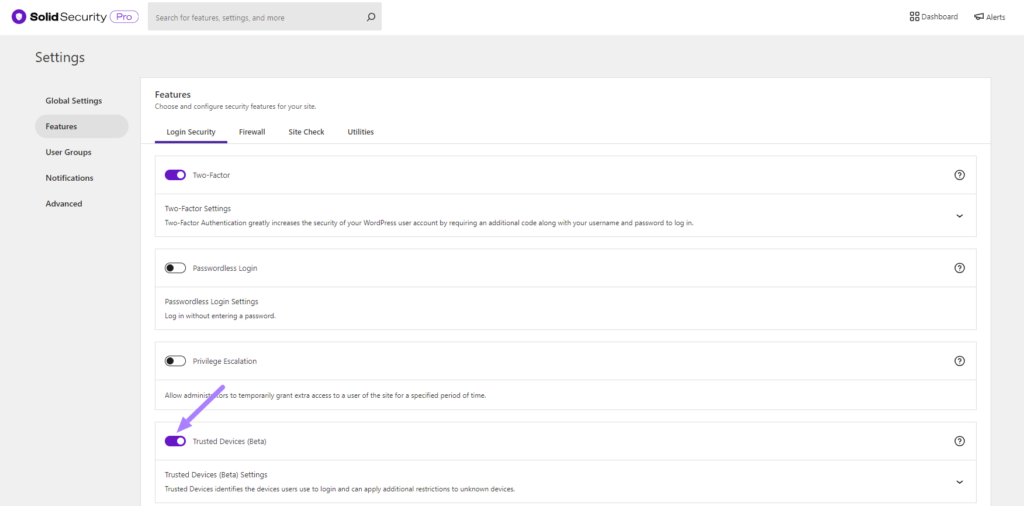
In the Trusted Devices settings, decide which users you want to use the feature, and enable then Restrict Capabilities and Session Hijacking Protection features.
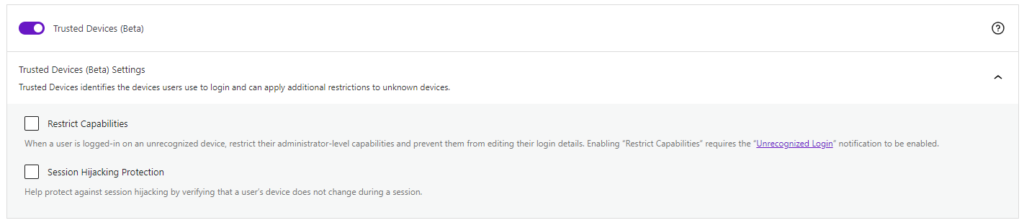
After enabling the new Trusted Devices setting, users will receive a notification in the WordPress admin bar about pending unrecognized devices. If your current device hasn’t been added to the trusted devices list, click the Confirm This Device link to send the authorization email.
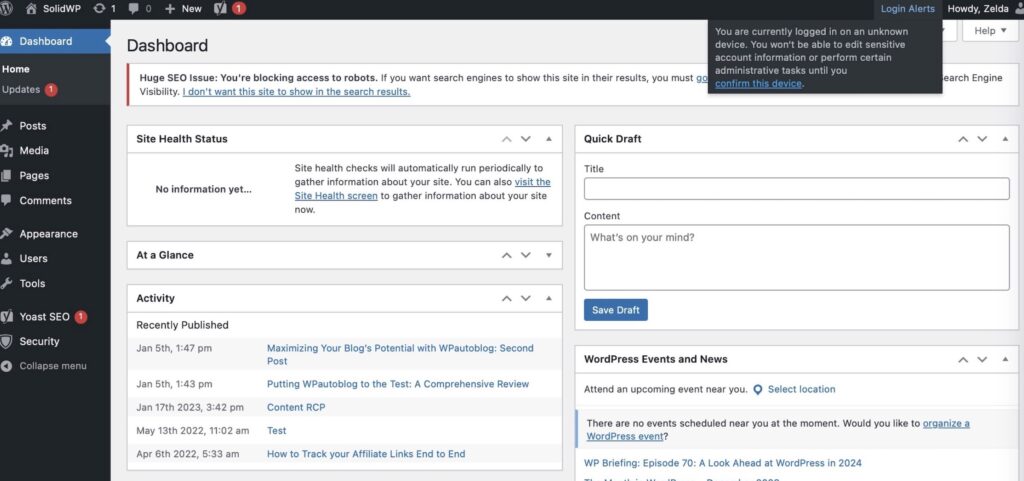
Click the Confirm Device button in the Unrecognized Login email to add your current devices to the Trusted Devices list.
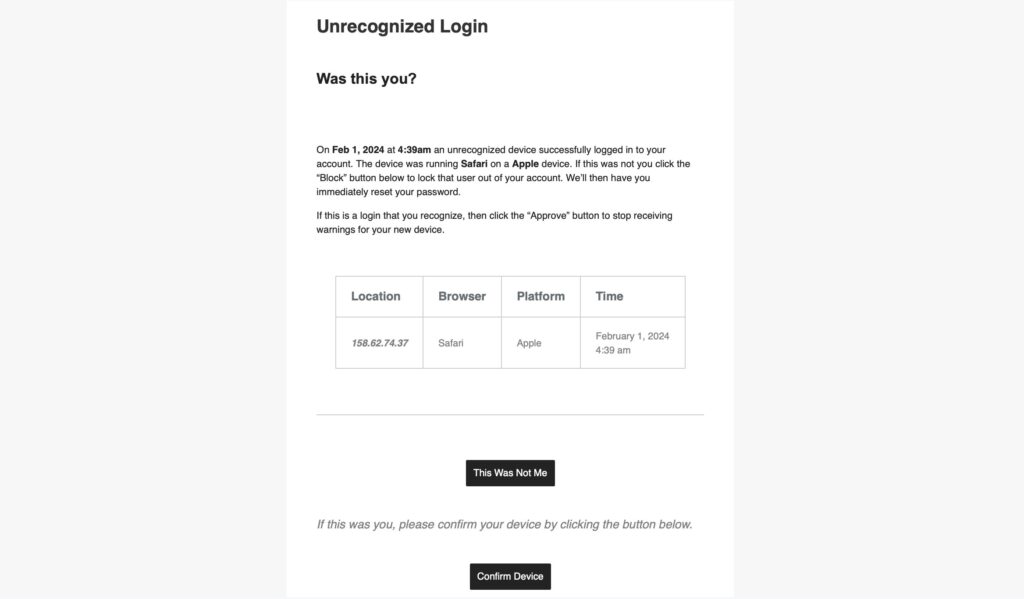
Once Trusted Devices is enabled, users can manage devices from their WordPress User Profile page. From this screen, you can approve or deny devices from the Trusted Devices list.
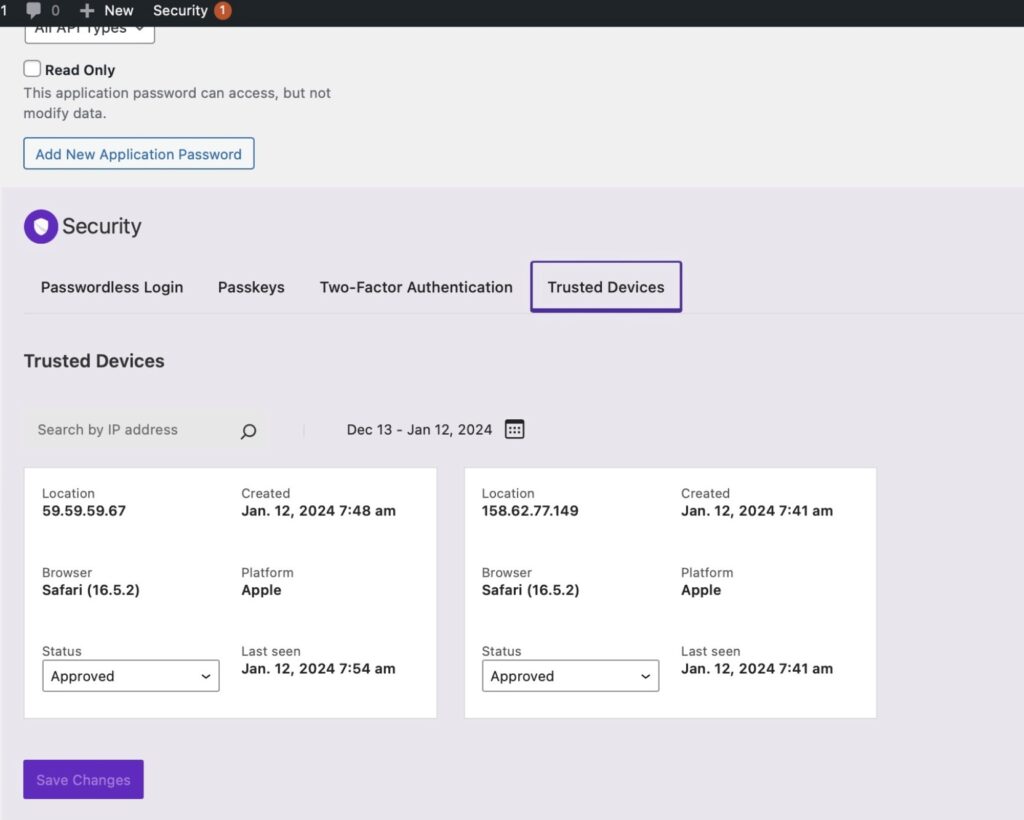
Additionally, you have the option to sign up for some third-party APIs to improve the accuracy of the Trusted Devices identification and to use static image maps to display the approximate location of an unrecognized login. Check out the Trusted Devices setting to see what integrations are available.
5. Turn on Two-Factor Authentication for All Admin Users
Two-factor authentication is a process of verifying a person’s identity by requiring two separate methods of verification. Google shared on its blog that using two-factor authentication can stop 100% of automated bot attacks. Not bad odds!
The Solid Security plugin allows you to activate two-factor authentication for your WordPress site so users must enter a secondary code to log in.
The three two-factor authentication methods provided by Solid Security Pro include:
- Mobile App – The mobile app method is the most secure method of two-factor authentication provided by Solid Security Pro. This method requires you to use a free two-factor mobile app like Authy or Google Authenticator.
- Email – The email method of two-factor will send time-sensitive codes to your user’s email address.
- Backup Codes – A set of one-time use codes that can be used to login in the event the primary two-factor method is lost.
To start using Two-Factor Authentication on your website, enable the feature on the main page of the Solid Security Pro settings.
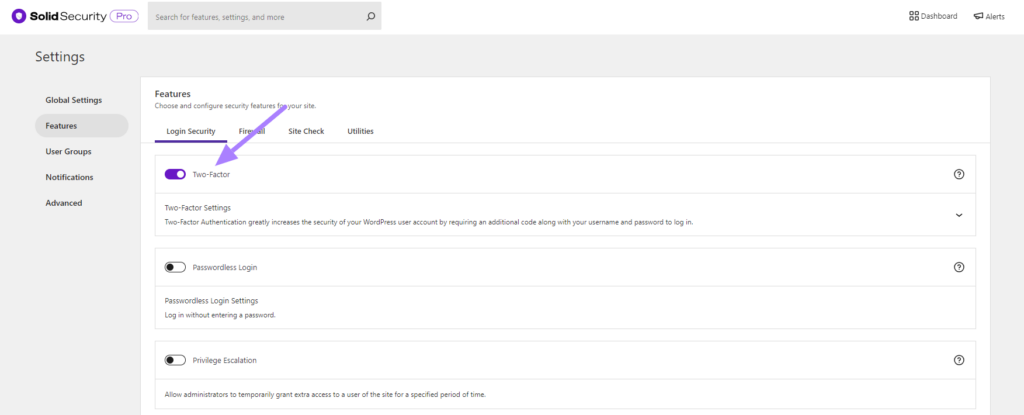
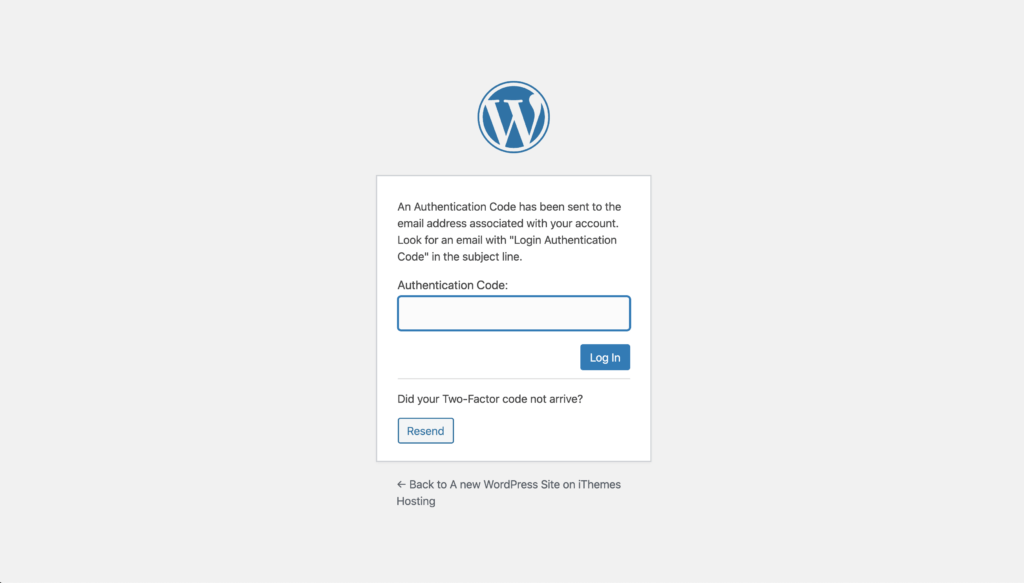
Follow the steps here to continue setting up two-factor authentication for your WordPress site. If you followed our recommendations and enabled the force requirements for privileged users, the next thing you will see is the place to enter the two-factor token.
RCE Prevention: Additional Tips
1. Only Use Well-Established Software Applications and Plugins
The process of “escaping,” works great as your first line of defense against RCE vulnerabilities. However, there are some additional ways that code can be interpreted by servers and browsers, beyond the script tags.
If your goal is to keep track of each and every one of them on your own, it would be very complicated and require a ton of your time and resources.
Fortunately, application developers have put a lot of thought into the issue of RCE vulnerabilities.
It’s best to use a trusted and reputable CMS (content management system) like WordPress because there are solutions built right into the platform and the themes and plugins that you run on it.
It’s always essential you keep all software applications and plugins up-to-date when new versions are released. When vulnerabilities are uncovered, software developers will work around the clock to stay ahead of the weaknesses they discover.
This is true for both plugin and theme authors.
If you’re using a custom CMS instead of WordPress, you can keep your site safe from potential SQL injections by utilizing parameterized queries. This query type will inform an application, in advance, the exact type of query you’re going to run. It’ll then recognize and remove added commands which a hacker might attempt to insert. Instead of successful insertion, it’ll send the original query and exclude the string that was added.
In the above example, a parameterized query would look like this:
$query=”SELECT * FROM users WHERE name = ?” $results=$query.execute(“ ' OR '1'='1' --”)
In this scenario, your database is handling ‘ OR ‘1’=’1′ in the correct manner. It looks at this query as a string of only text and understands that there isn’t a user associated with the name provided.
2. Validate the Input of Users
The best place to begin preventing RCE vulnerabilities is where your site users interact with your application.
The simplest method is to remove and filter out any characters that are undesired.
Yet another option is preserving content by escaping it.
If you’re not familiar with what escaping means, it’s the process in which you instruct your computer to look at something which appears to be code as regular text. For example, you’d replace a script tag with “<script>”.
By doing this, a web browser understands to display the less-than “< and greater than “> symbols at the specified location. But it won’t treat the entire string of text as code.
To the user, the result is invisible.
3. The Least Privilege Principle
There may be rare instances where a zero-day RCE vulnerability could arise. This means that neither you nor the CMS and application developers are aware of a specific new type of attack.
Even in a case such as this, we’re still able to limit the damage that an attacker can do by setting up some simple rules about what an application is able to do.
For example, imagine you’re designing an application that reads from a database. It really wouldn’t be necessary to give the new application the ability or permission to delete or write database records.
In this case, even if attackers try to compromise the script, they’ll encounter an error and fail at their attempt.
The least privilege principle is also useful as it relates to PHP functions.
PHP functions are a standard target for online attackers of all kinds. Robust functions that might not be needed for your app, such as ini_set() (this allows you to update your PHP settings from within script) or exec() (which runs code passed as text), should be disabled.
This prevents hackers and attackers from using them for malicious purposes.
This idea applies to securing the public-facing areas of your website and the server-side code.
4. Content-Security-Policy
Content-Security-Policy is a header used in HTTP by most modern web browsers. It determines what types of content the browser is supposed to load on your website. When you send headers from your application or web server, you’ll be able to specify the types of scripts that are allowed to run, and to which locations.
Using the strategy helps prevent hackers from injecting their malicious scripts.
5. Stop Script From Reading Cookies
Yet another option is to prevent scripts from reading cookies. This stops requests from being sent to other sites.
This is done by setting them with the SameSite=Strict or HttpOnly attributes. Even when a hacker’s code gets run on your WordPress site, you’ll prevent them from gaining access to your site user’s authentication cookies.
This will significantly reduce the potential damage during a WordPress remote code execution attack.
Wrapping UP: WordPress Remote Code Execution
Don’t worry if you’re feeling a bit overwhelmed when you discover the potential security threats seeking out your WordPress site. The truth is that the threats are many, but the solutions can be simple.
We hope this guide helped you understand the risk of RCE attacks on your WordPress site. By implementing a few WordPress security best practices, along with the 5 steps above, you’ll have a better line of defense.
Get SolidWP tips direct in your inbox
Sign up
Get started with confidence — risk free, guaranteed
Sign up now — Get SolidWP updates and valuable content straight to your inbox
Sign up
Get started with confidence — risk free, guaranteed
