New! Introducing Trusted Devices with Session Hijacking Protection in iThemes Security
The latest version of iThemes Security Pro just added another layer of security for your WordPress website. Introducing Trusted Devices, a new way to monitor and identify the devices used to login to WordPress. By adding security measures for unknown devices, along with Session Hijacking protection, you can lock down your WordPress website and protect it from compromises to user logins.

The latest version of iThemes Security Pro just added another layer of security for your WordPress website. Introducing Trusted Devices, a new way to monitor and identify the devices used to login to WordPress.
By adding security measures for unknown devices, along with Session Hijacking protection, you can lock down your WordPress website and protect it from compromises to user logins.
New! Trusted Devices + Login Alerts
iThemes Security’s new Trusted Devices setting works to identify the devices users use to login to your WordPress site and can apply additional restrictions to unknown devices.
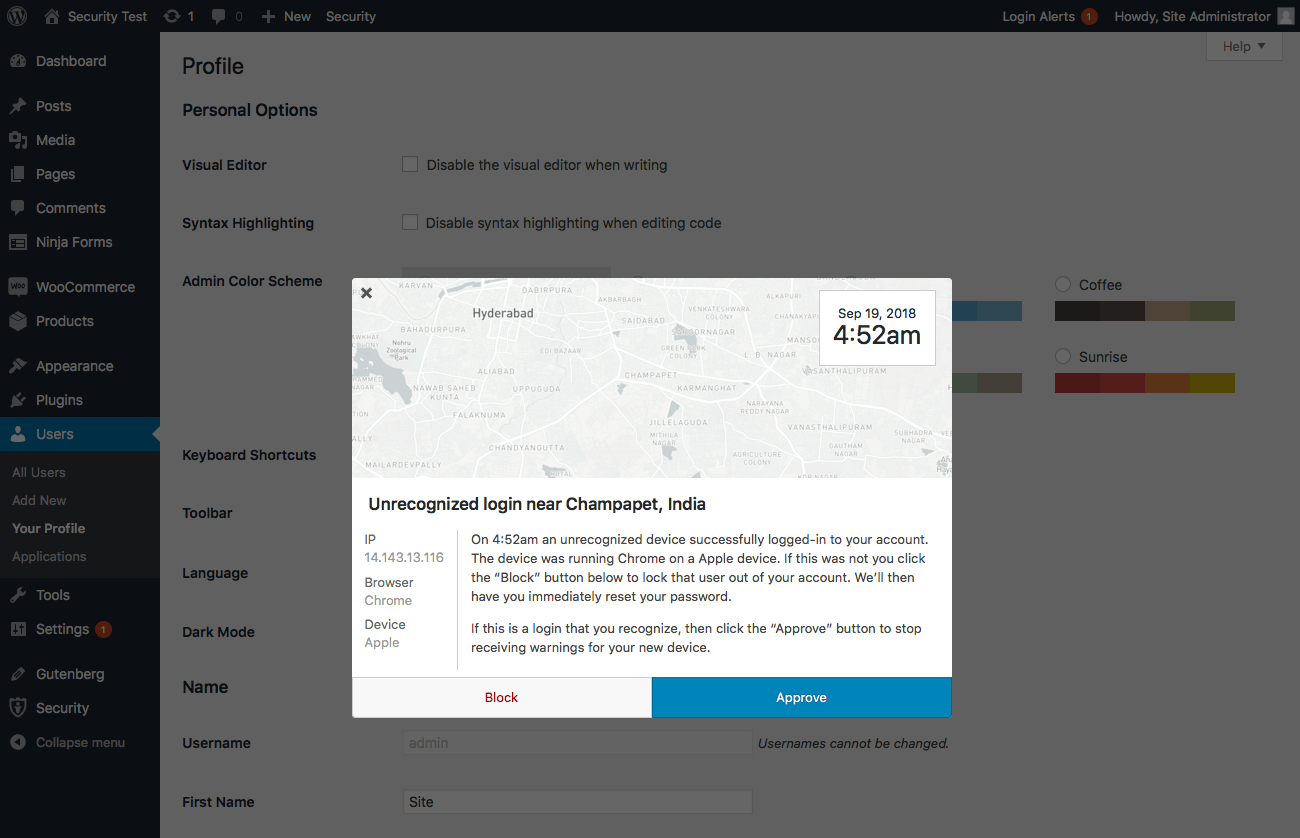
Notice for Unrecognized Devices
After enabling the new Trusted Devices setting, users will receive a notification in the WordPress admin bar about pending unrecognized devices.
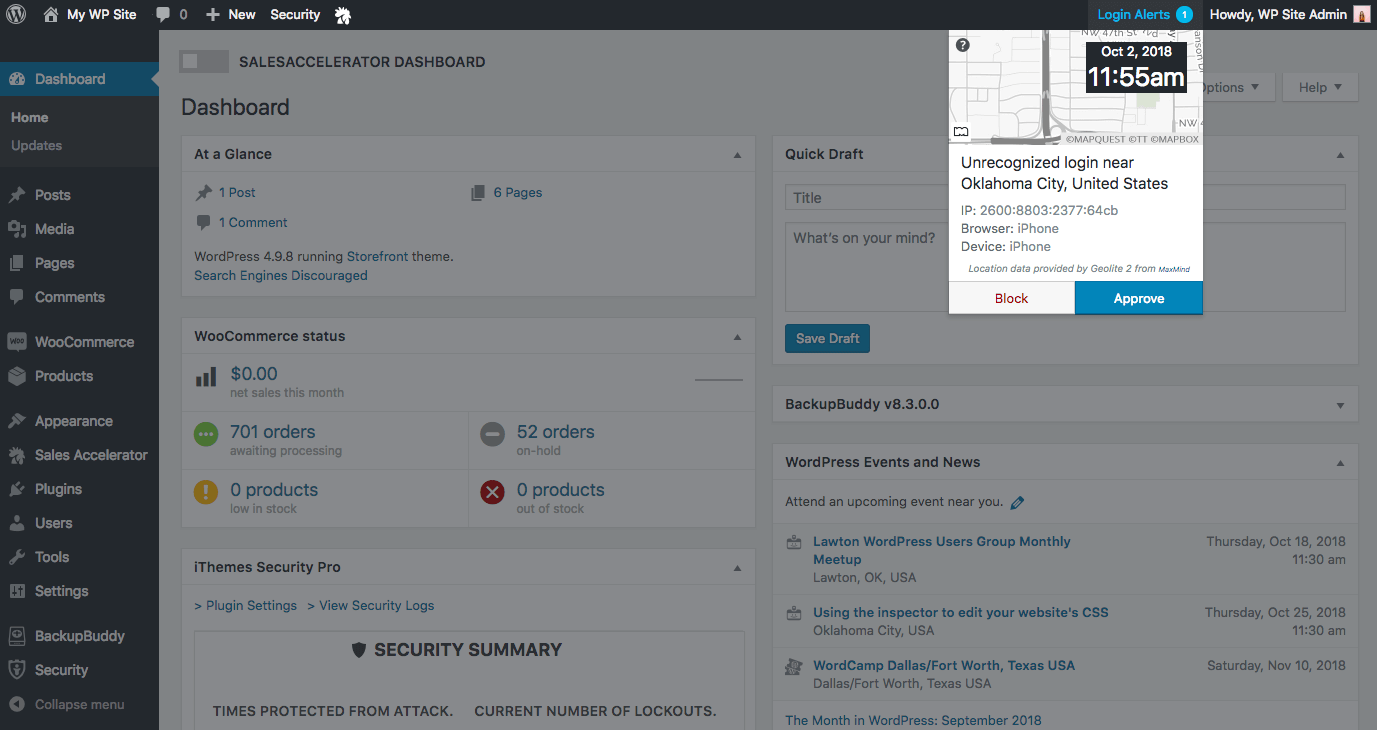
Optional Email Notification
In addition to the WordPress admin login notice, an Unrecognized Login Notification email (optional, but recommended) can also alert you whenever an unrecognized device has been used to log in.
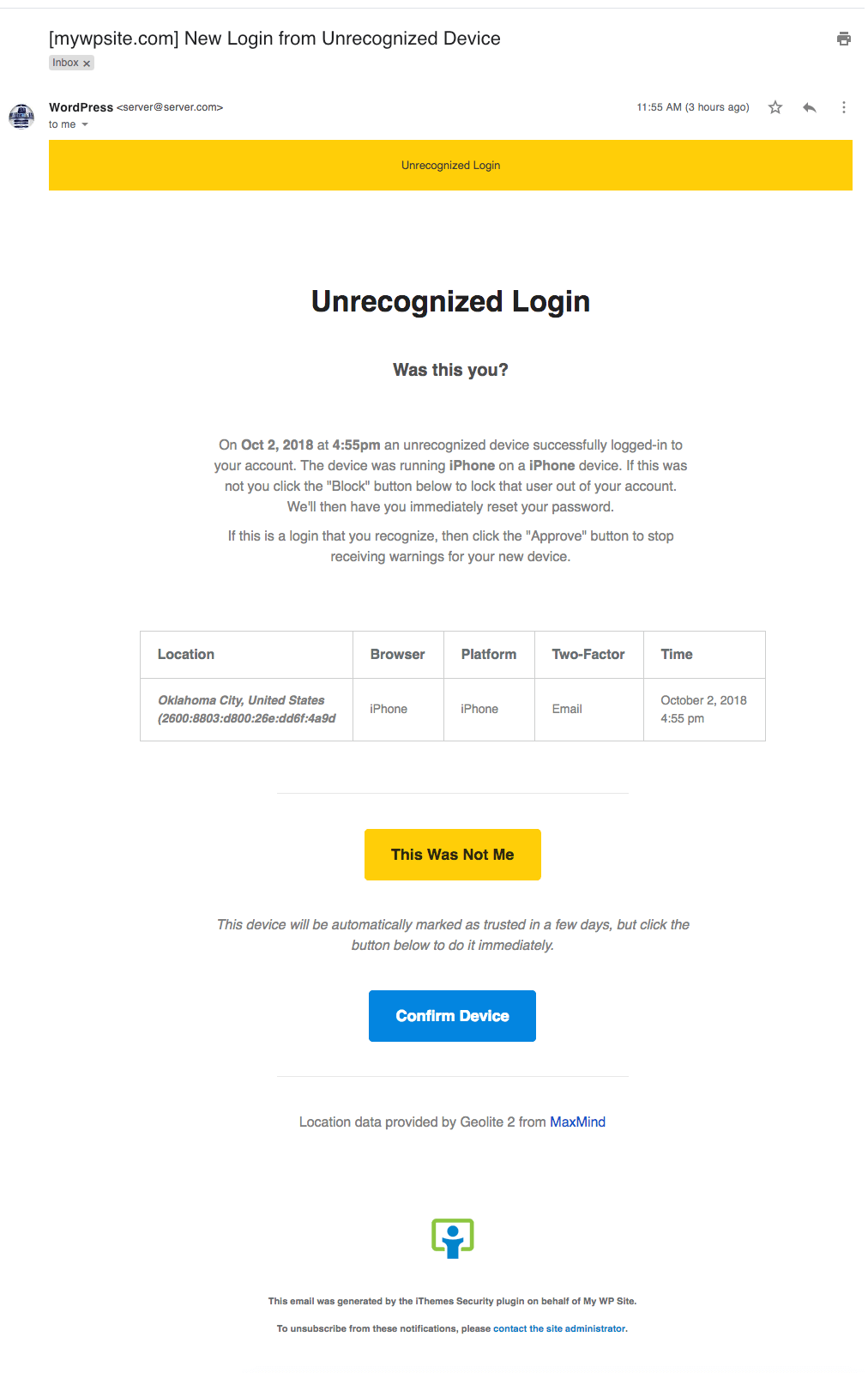
The Unrecognized Login Notification email is customizable from iThemes Security’s Notification Center. From the settings, you can use the default text or add your own. This email notification also supports basic HTML and email tags.
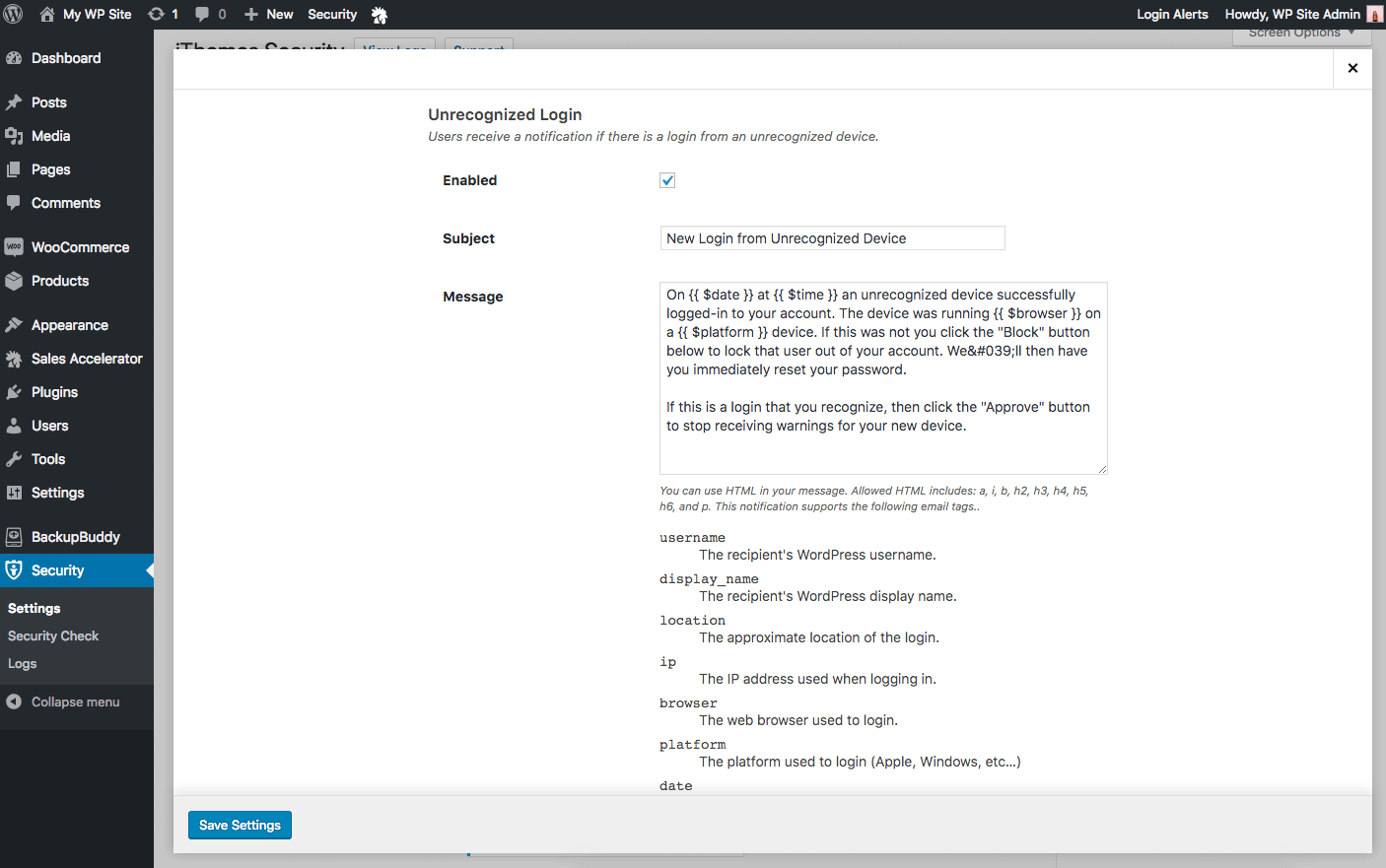
Restrict Capabilities on Unrecognized Sessions
When a user is logged in on an unrecognized device, you can restrict their administrator-level capabilities to prevent them from editing their login details.
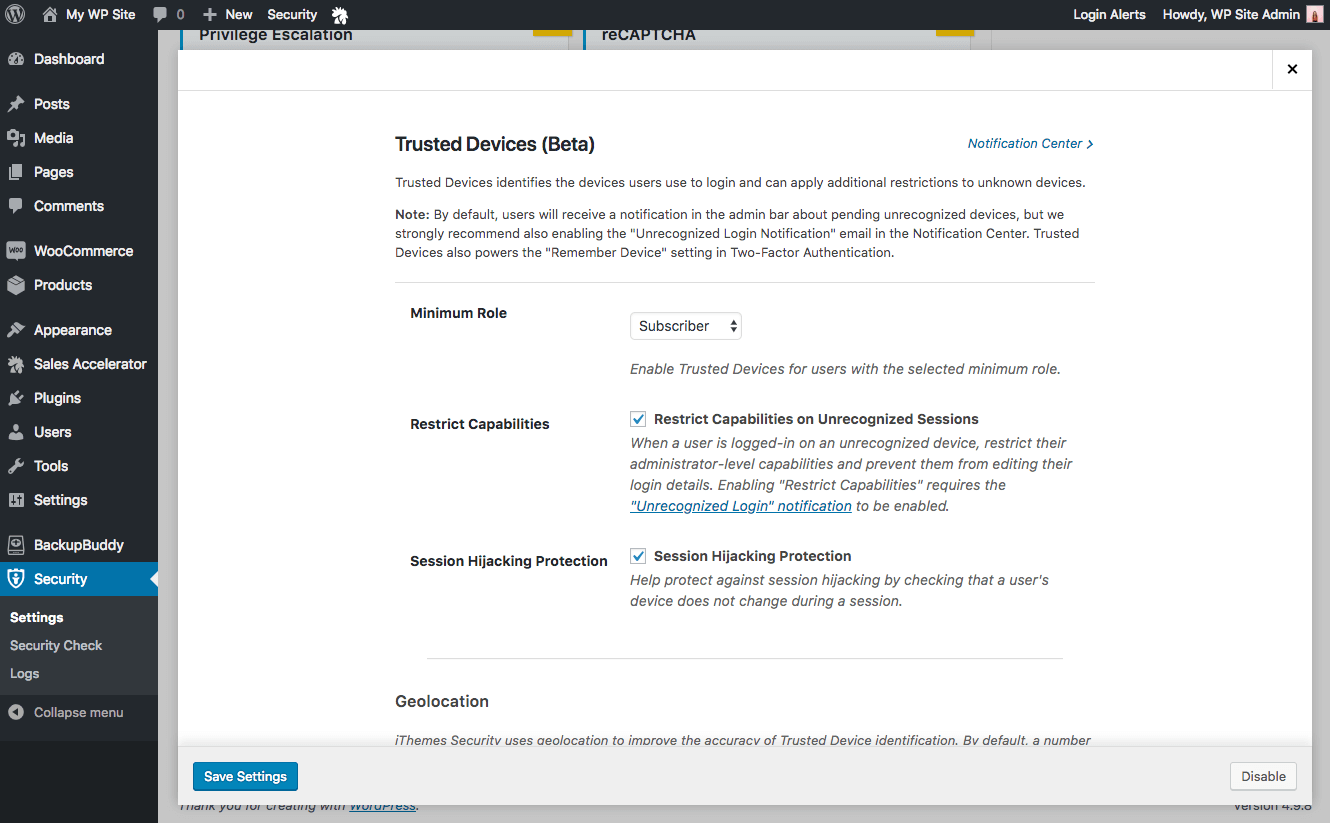
New! Session Hijacking Protection
[pullquote]Session hijacking, sometimes called Cookie hijacking, is a strategy used by hackers to take control of your account while you are using it, effectively becoming the owner.[/pullquote]
By enabling iThemes Security’s new Session Hijacking Protection in the Trusted Devices setting, you can prevent session hijacking by checking that a user’s device does not change during a session.
If a user’s device changes during a session, iThemes Security will automatically log the user out to prevent any unauthorized activity on the user’s account, such as changing the user’s email address or uploading malicious plugins.

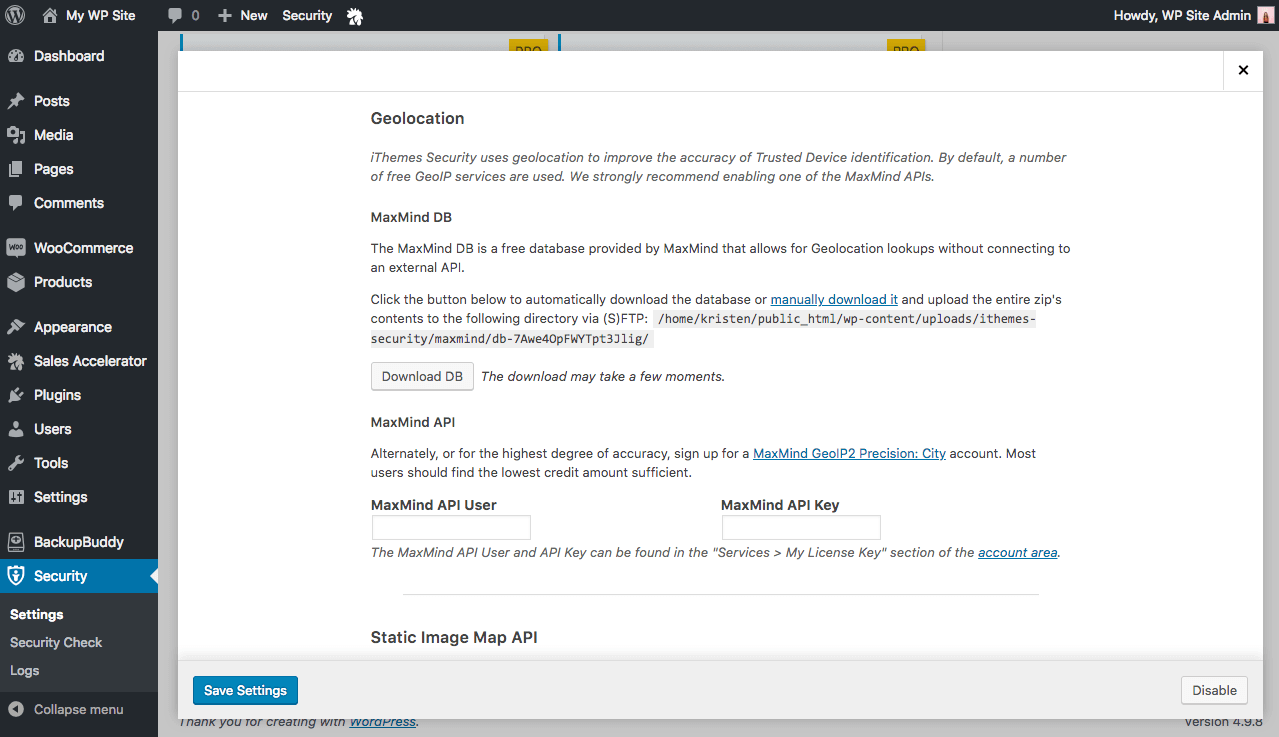
New! Geolocation Accuracy & Static Image Maps
iThemes Security uses geolocation to improve the accuracy of Trusted Device identification. You can use either the free MaxMind database that allows for Geolocation lookups without connecting to an external API or, for the highest degree of accuracy, you can sign up for a MaxMind GeoIP2 Precision: City account. Most users should find the lowest credit amount sufficient.
iThemes Security also utilizes static image maps to display the approximate location of an unrecognized login. We recommend using either the Mapbox or MapQuest APIs. The free plan for both services should be sufficient for most users.
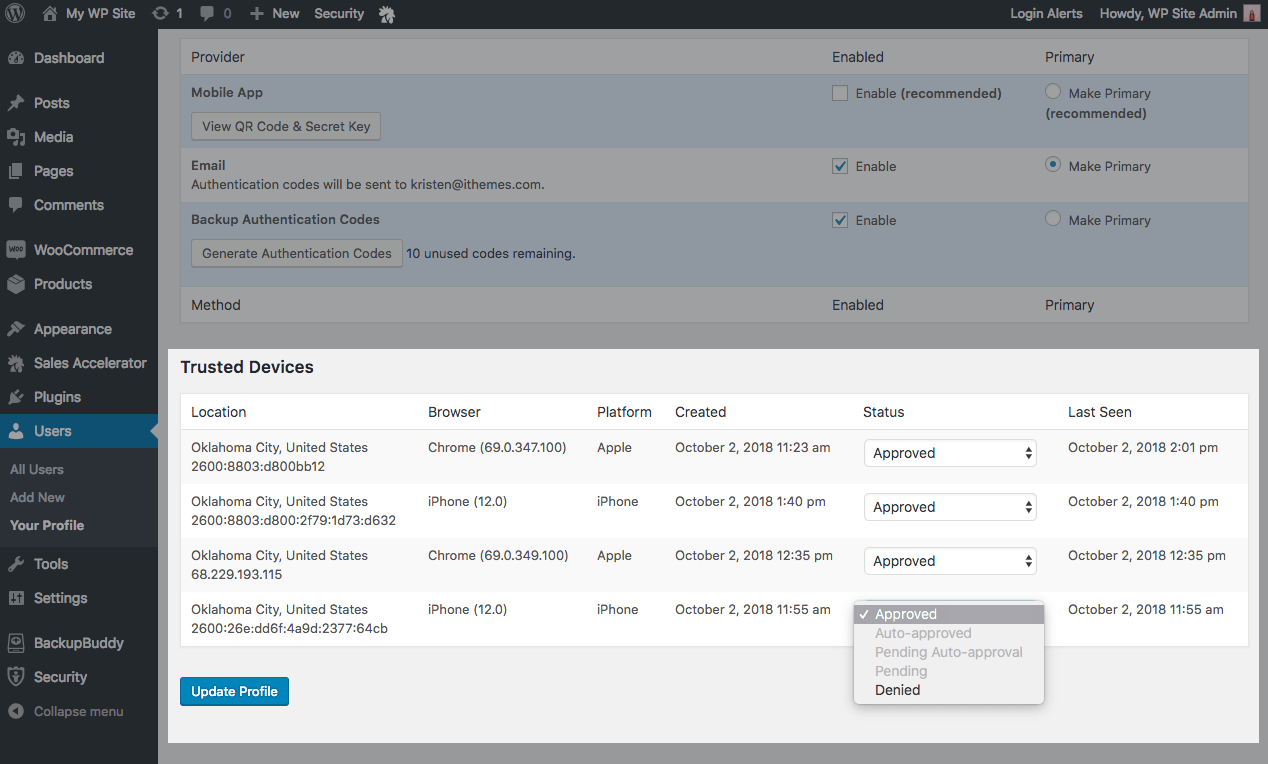
WordPress User Profile with Trusted Devices Info
Once Trusted Devices is enabled within iThemes Security, site admins can manage devices from the WordPress User Profile page. From this screen, site admins can approve or deny devices from the Trusted Devices list.
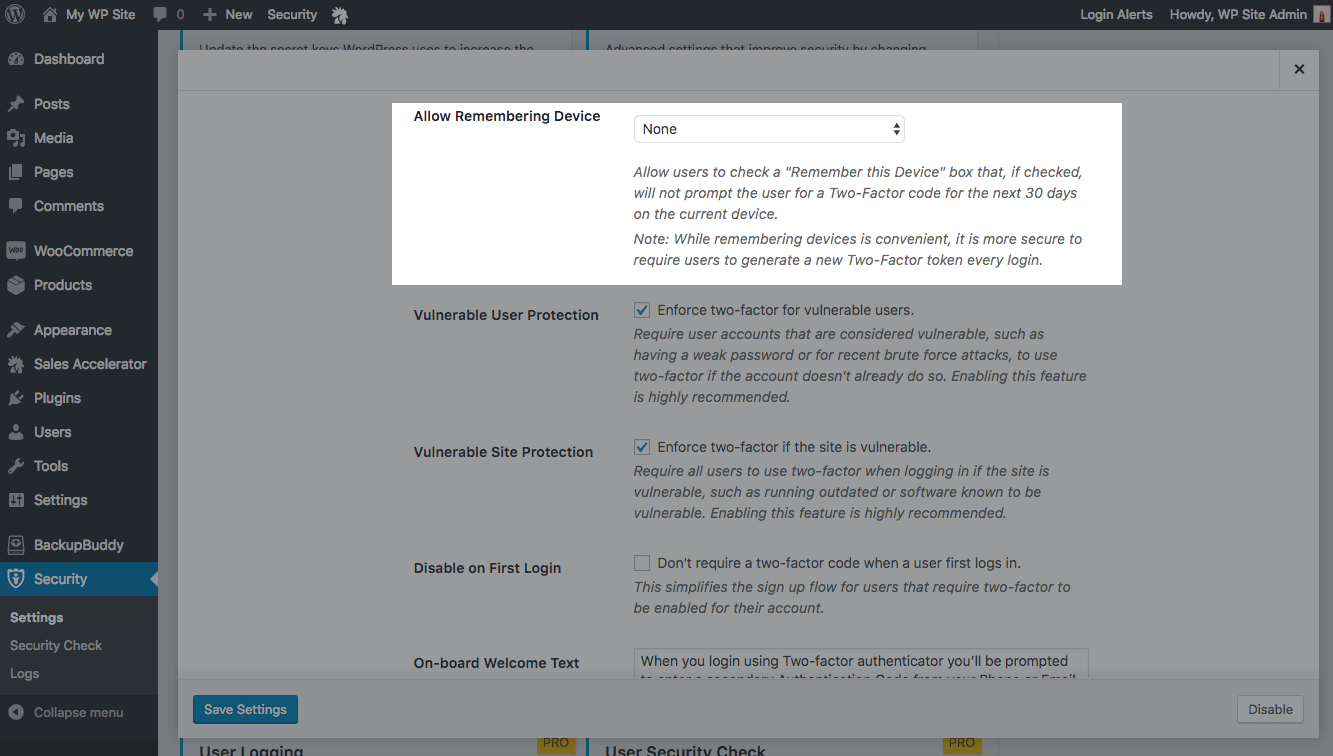
Integration with Two-Factor Authentication
Trusted Devices powers iThemes Security’s “Remember Me” setting in Two-Factor Authentication. If the device doesn’t look the same, users are forced to re-enter their two-factor code instead of bypassing it.
Secure & Protect Your WordPress with Solid Security Pro
The new Trusted Devices with Session Hijacking Protection is just another way you can secure and protect your WordPress website. Along with other Pro features such as WordPress two-factor authentication, WordPress malware scan, WordPress brute force protection and more, you can rest a little easier, knowing your website is protected by Solid Security Pro.
Solid Security is part of Solid Suite — The best foundation for WordPress websites.
Every WordPress site needs security, backups, and management tools. That’s Solid Suite — an integrated bundle of three plugins: Solid Security, Solid Backups, and Solid Central. You also get access to Solid Academy’s learning resources for WordPress professionals. Build your next WordPress website on a solid foundation with Solid Suite!
Get Release Notes for SolidWP products delivered right to your inbox.
Sign up
Sign up now — Get SolidWP updates and valuable content straight to your inbox
Sign up
Get started with confidence — risk free, guaranteed