Unpatched Vulnerability in WordPress Core: What It Really Means
In this week's iThemes Vulnerability Report, you’ll note that there is an unpatched vulnerability in WordPress core. This vulnerability was reported by Thomas Chauchefoin, and at this time, it affects all versions of WordPress. However, probable exploitation of this vulnerability is very low, and to fully protect yourself, all you’ll need to do is turn off XML-RPC or pingbacks on your WordPress site.

In this week’s iThemes Vulnerability Report, you’ll note that there is an unpatched vulnerability in WordPress core. This vulnerability was reported by Thomas Chauchefoin, and at this time, it affects all versions of WordPress. However, probable exploitation of this vulnerability is very low, and to fully protect yourself, all you’ll need to do is turn off XML-RPC or pingbacks on your WordPress site.
What this vulnerability means for your site
While a full Proof of Concept has not yet been released by WPScan, we can make some educated guesses as to how this vulnerability can be exploited. They state:
“WordPress is affected by an unauthenticated blind SSRF in the pingback feature. Because of a TOCTOU race condition between the validation checks and the HTTP request, attackers can reach internal hosts that are explicitly forbidden.”
To exploit this vulnerability, an attacker would utilize WordPress pingbacks but would be forced to do so in combination with other vulnerabilities.
In order to exploit a vulnerability like this to do any kind of damage to a WordPress site, this vulnerability would only be useful if used with other more serious vulnerabilities on an unpatched or insecure WordPress site.
Officially, the WordPress.org security team has stated that this is a low-priority vulnerability. Specifically, they told the Daily Swig:
“…this is a low-impact issue and exploiting it requires ‘[chaining] it to additional vulnerabilities in third-party software’. As such, the Security Team considers the issue a low priority.”
They added: “Because of its low severity, the team is discussing whether this issue could be fixed in public as a general hardening measure.”
This underscores the difficulty of adding security fixes to so many older versions of WordPress. For years, the core team has been backporting patches to versions that were many years old and only used by a few straggler sites that had not yet been updated. The recent decision by the core team to no longer backport older versions will make fixing these types of issues easier and faster for the WordPress core team.
How to protect your site
With pingbacks being the obvious weak point being discussed, turning off pingbacks and/or XML-RPC is a great first step.
If you’re keeping your WordPress site updated and you’re on reliable hosting with a strong and secure infrastructure, the probability of exploitation using this vulnerability is extremely low.
If you’re looking to keep your site as secure as possible, the best option is to turn off pingbacks or XML-RPC. Luckily, iThemes Security gives you options to do both.
How to turn off XML-RPC using iThemes Security
Turning off XML-RPC using iThemes Security is incredibly easy. Head to Security > Settings > Advanced > WordPress Tweaks and then use the dropdown to turn off XML-RPC.
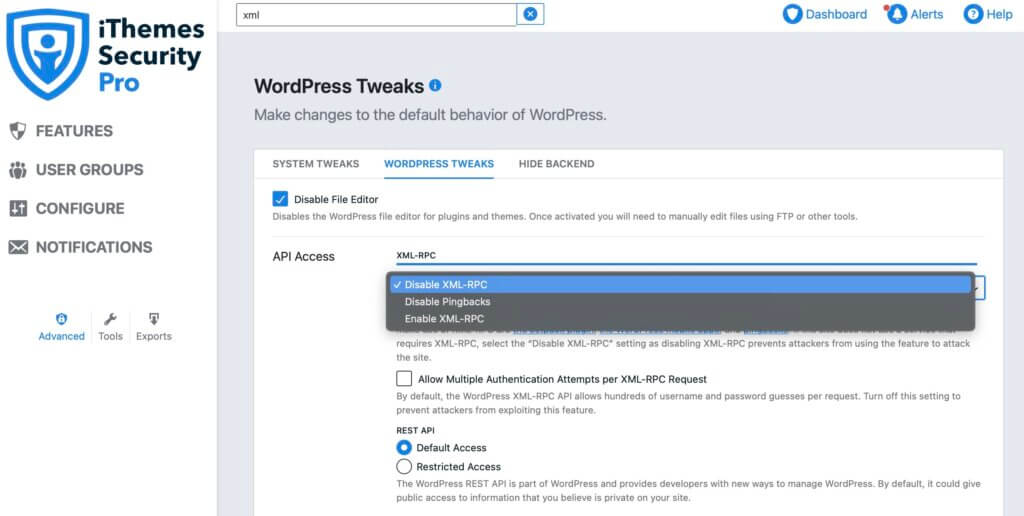
There might be some cases where you need XML-RPC. These include:
- If you have an old website that you can’t update to version 4.4 or higher, you don’t have access to the REST API and you may be using services that require XML-RPC.
- You’re using a program that can’t access the REST API to communicate with your website.
- Integration with some 3rd party apps that can only use XML-RPC.
Turning off XML-RPC is a simple process with iThemes Security. You can toggle this off and test your site’s functionality and if anything seems like it isn’t working correctly, you can toggle it back on.
These are the types of situations where it makes sense to have a staging server set up so that you can test for changes before applying them to your production site.
Muting the vulnerability in your iThemes Site Scan
Of course, iThemes Security’s site scanner is going to notify you about this vulnerability. Since it won’t be fixed by the core team in the immediate future, it might make sense to prevent alert fatigue by muting this vulnerability in the site scanner. Refer to our help documentation on muting vulnerability alerts.
Conclusion
This vulnerability, while unpatched, poses a very slight risk to WordPress site owners. If your site already has XML-RPC turned off, you’re already protected. Pingbacks are one of the legacy features of WordPress that can be useful in some cases, however, it is not a feature used by many modern websites. This is one of the cases where it is helpful to have a security plugin like iThemes Security installed so that you can quickly take action when you can to harden your site against attackers, even if the vulnerability in question is of low severity.
Solid Security is part of Solid Suite — The best foundation for WordPress websites.
Every WordPress site needs security, backups, and management tools. That’s Solid Suite — an integrated bundle of three plugins: Solid Security, Solid Backups, and Solid Central. You also get access to Solid Academy’s learning resources for WordPress professionals. Build your next WordPress website on a solid foundation with Solid Suite!
Sign up now — Get SolidWP updates and valuable content straight to your inbox
Sign up
Get started with confidence — risk free, guaranteed