What is a File Inclusion Attack?
Any tool can be used with good or bad intentions, and file inclusion is no different. File inclusion is a programming method that makes it easier to maintain code and extend functions throughout a site. A file inclusion attack abuses the way PHP uses file inclusion as a valid method of uniting and executing code from many separate files to create a single web page.

Any tool can be used with good or bad intentions, and file inclusion is no different. File inclusion is a programming method that makes it easier to maintain code and extend functions throughout a site. A file inclusion attack abuses the way PHP uses file inclusion as a valid method of uniting and executing code from many separate files to create a single web page. Since PHP is a language WordPress uses, WordPress and other PHP applications are prone to file inclusion vulnerabilities when appropriate security measures are broken, incomplete, or absent.
In this complete guide to file inclusion attacks, we will explore ways hackers exploit poor user input sanitization and validation to inject malware and send bad instructions to break into WordPress sites.
You will learn how WordPress file inclusion attacks happen and what you can do to protect your website from falling victim to them.

What is File Inclusion?
File inclusion is a development technique for including many files into one script or web page to add functionality, reuse a design template, or share a piece of content on multiple pages.
File inclusions are absolutely necessary. Developers commonly use them for the following purposes:
- Including header and footer files common to all pages of a website to ensure consistency in design and function.
- Including scripts and libraries for key functionality throughout a website or web application.
- Including configuration files containing settings for the application, such as database connection information and API keys.
- Including content such as images, video, text, or other content on web pages.
- Including functionality for generating dynamic content based on user input passed as a URL parameter. For example, a user might submit a form to generate certain output.
Types of File Inclusion
Using the file inclusion technique, developers can add files and scripts to a web page either statically or dynamically.
Using static file inclusion, a developer can reuse the same text or code on multiple pages by referring to a Uniform Resource Locator (URL) or a path to a file stored locally, that is, on the same server. Static file inclusions allow themes to use the same header, footer, or navigation menu code on many web pages.
Dynamic file inclusions accept user input at runtime. The user indicates the desired output by passing the path to a specific file. Typically the user input will be passed as a parameter in a URL or a form submission. For example, a user might select “English” from a dropdown selection list of languages, which takes them to an English-language version of the page they’re on by changing the URL like this: /page.php?language=english. If someone replaced “english” with a remote file’s URL, they might be able to inject a web shell as a backdoor and/or other malware into the targeted site if there aren’t checks in place to prevent this.
How is File Inclusion Implemented in WordPress?
All dynamic web applications written in PHP — like WordPress — can use file inclusion safely. In applications written in PHP, developers perform file inclusion by using the include and require statements. Developers use both statements to insert the contents of one PHP script into another. This happens before the code is executed on the server.
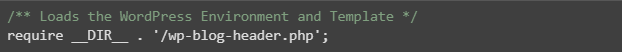
If you look at some of the WordPress core files, many of them refer to other core scripts. When they’re all loaded together they build your site’s structure and generate the individual web pages requested by a visitor. The main index.php references wp-blog-header.php, which loads the WordPress environment and theme template — wp-load.php and template-loader.php, respectively.
Along with WordPress core, plugins and themes also use file inclusion to perform necessary tasks. However, with tens of thousands of WordPress plugins available, not all of them are as well-tested as WordPress core is.
File inclusions introduce serious security risks when developers don’t secure them properly. If the code you’re using doesn’t validate and sanitize user input, hackers can exploit it. They can use it to install malware and steal sensitive information — possibly yours or your customers!
What is a File Inclusion Attack?
Two types of file inclusion attacks are possible: local file inclusion (LFI) or remote file inclusion (RFI).
File inclusion attacks are part of the broader injection attack class. This include SQL injections (SQLi), cross-site scripting (XSS), and command inclusion attacks. Hackers can exploit input vulnerabilities to make other types of attacks, like buffer overflow attacks.
Local and Remote File Inclusion Attacks
Websites and web applications that rely on dynamic file inclusions to enable certain features may be exposed to both remote file inclusion attacks and local file inclusion attacks.
Local File Inclusions (LFI)
A local file inclusion attack may inject a file located on the same server as the targeted website or web application. LFI attacks can often gain access to normally restricted files. In an LFI attack, the included file must already be present on the local application server that is being targeted. In an LFI attack, a bad actor can read important files, access more sensitive information, or run arbitrary commands.
Local file inclusion attacks can also allow someone to access sensitive data outside of the targeted website. This includes server configuration files such as /etc/passwd or another website’s configuration files such as wp-config.php. It is important to note, however, that the targeted files need to be readable to unprivileged users — for example, the /etc/passwd file on Linux systems is owned by root, but with its file permissions set to 644, all other system users can view it.
To navigate through the file system, attackers employ directory traversal, a technique to access files outside the current working directory by manipulating directory path traversal sequences such as ../../../.
Remote File Inclusions (RFI)
Remote file inclusion attacks target websites and applications that call on files hosted on another server. By exploiting remote file inclusion, an attacker can draw on malicious code hosted elsewhere. A vulnerability must exist on the targetted server, but the attacker will use it to execute malicious code hosted elsewhere.
In Remote File Inclusion attacks, hackers take advantage of the “dynamic file include” command in web applications. Hackers can exploit web applications that accept user input, such as URLs and parameter values, and pass them to the “file include” mechanisms without proper sanitization. In this type of vulnerability, attackers can exploit the web application to include remote files with malicious scripts.
Why Do WordPress File Inclusion Attacks Occur?
WordPress sites make up 43% of the internet, so they are a large target for attackers. Our 2022 WordPress Vulnerability Annual Report shows that over 90% of all WordPress vulnerabilities discovered last year were in plugins and themes. Typically, we saw at least one new security flaw reported weekly in 20 to 50 plugins.
Recently, security researchers discovered a file inclusion vulnerability in the popular OceanWP theme. OceanWP has over half a million active users. (We reported this in our weekly WordPress vulnerability report.) Even though OceanWP quickly patched the vulnerability, hackers had time to exploit it while millions of WordPress sites were still using the outdated code.
Get SolidWP tips direct in your inbox
Sign up
Get started with confidence — risk free, guaranteed
How to Detect a WordPress File Inclusion Attack
Unlike denial-of-service attacks that can significantly slow down your website or malicious redirects that drive people away from your website to fraudulent resources, file inclusion attacks are hard to detect. The reason for this is simple. Hackers use file inclusion as an entry point to upload malware and carry out further attacks. The file inclusion is a quiet path to the more visible damage. So, when a hacker injects malicious code into a website or accesses sensitive information, there is a big chance that you would hardly notice it.
This brings us to an important conclusion. Website security should start by making the attack surface small and hardening it. This will help prevent hackers from exploiting input vulnerabilities that injection attacks stem from, such as file inclusion attacks, SQL and command injections, and cross-site scripting (XSS).
How to Defend Against WordPress File Inclusion Attacks?
With the growing number of cyber attacks targeting WordPress, WordPress website security matters more than ever before. Defending against WordPress file inclusion attacks requires a multifaceted approach that limits the possibility of exploiting input vulnerabilities and arbitrary code execution. You can do this if you adopt a combination of proactive and reactive security measures.
Here are the top three WordPress security recommendations to protect your website against file inclusion attacks.
Keep All Software Updated
Keeping all your software updated — including WordPress core, themes, plugins, and extensions — is critical when it comes to reducing the attack surface of your site. As new vulnerabilities emerge every day, don’t give hackers a chance to exploit them. Install security patches and make updates as soon as they are available.
Get in the habit of making regular updates yourself or activate automatic updates to ensure your website never runs any vulnerable code. Solid Security Pro can take care of WordPress core, plugin, and theme updates for you.
Solid Security Pro automatically scans for new versions of the software your website is using. Its Version Management system ensures that you have all the security patches and updates installed as soon as they are available. On top of that, Solid Security will also alert you if you are running any outdated software in your server infrastructure. For example, if you are using a PHP version past its end-of-life date or a vulnerable MySQL server, Solid Security Pro will warn you.
If you have multiple WordPress sites under your control, Solid Central gives you a single interface to manage them all. Central also offers advanced uptime monitoring and SEO feedback.
Disable Remote File Inclusion in PHP
It’s possible for a website to reference remote files from an external URL if the allow_url_fopen option is enabled in the PHP environment. This can increase the risk of remote file inclusion attacks. Disabling allow_url_fopen effectively eliminates the possibility for someone to run malicious code loaded from a remote location on your WordPress website.
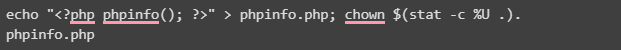
You can disable allow_url_fopen in the PHP global configuration or by setting allow_url_fopen to 0 in a local .user.ini or php.ini file created for an individual web folder. You can check whether the option is disabled in your PHP environment by creating a simple PHP information page using the phpinfo() function, as shown below.
Implement WordPress Security Headers
HTTP response headers such as Content Security Policy (CSP) and Set-Cookie can add a layer of defense against file inclusion and other injection attacks to your WordPress website.
WordPress security headers make it possible to reduce or block the vectors by which remote file inclusion and cross-site scripting (XSS) attacks can occur by making a list of trusted sources, scripts, and other content that can be loaded. All other sources will be denied. On top of that, HTTP response headers can help you add protection against cross-site request forgery (CSRF) and clickjacking.
Protect Your WordPress Site Against Injection Attacks with Solid Security Pro
Along with SQL and command injections, file inclusion attacks make the most common attack vectors targeting the security of WordPress sites. Although WordPress proves a high level of application security, highly customized sites combined with poor security practices can expose a WordPress website to injection attacks exploiting input vulnerabilities.
Every day, new vulnerabilities are found in the growing population of WordPress plugins and themes. And while they are usually patched rapidly, a lack of timely updates and reliance on old software can make your WordPress website an easy target for hackers. Today, website security is more critical than ever before. The increasing number of cyberattacks means that even the most vigilant website owners can fall victim to hackers if they don’t take proactive measures to protect their sites.
Solid Security Pro is a powerful WordPress security solution that allows you to adopt the best WordPress security practices to protect your website against the most sophisticated cyberattacks. With advanced file integrity monitoring, vulnerability scanning, and automatic attack mitigation, Solid Security Pro makes an excellent choice if you are looking for an effective and reliable way to protect your WordPress site.
Solid Security is part of Solid Suite — The best foundation for WordPress websites.
Every WordPress site needs security, backups, and management tools. That’s Solid Suite — an integrated bundle of three plugins: Solid Security, Solid Backups, and Solid Central. You also get access to Solid Academy’s learning resources for WordPress professionals. Build your next WordPress website on a solid foundation with Solid Suite!
Sign up now — Get SolidWP updates and valuable content straight to your inbox
Sign up
Get started with confidence — risk free, guaranteed