WordPress Vulnerability Report: October 2021, Part 1
Vulnerable plugins and themes are the #1 reason WordPress websites get hacked. The weekly WordPress Vulnerability Report powered by WPScan covers recent WordPress plugin, theme, and core vulnerabilities, and what to do if you run one of the vulnerable plugins or themes on your website. Each vulnerability will have a severity rating of Low, Medium, High, or Critical.

Vulnerable plugins and themes are the #1 reason WordPress websites get hacked. The weekly WordPress Vulnerability Report powered by WPScan covers recent WordPress plugin, theme, and core vulnerabilities, and what to do if you run one of the vulnerable plugins or themes on your website.
Each vulnerability will have a severity rating of Low, Medium, High, or Critical. Responsible disclosure and reporting of vulnerabilities is an integral part of keeping the WordPress community safe.
Please share this post with your friends to help get the word out and make WordPress safer for everyone.
Get SolidWP tips direct in your inbox
Sign up
Get started with confidence — risk free, guaranteed
WordPress Core Vulnerabilities
The lastest version of WordPress core is 5.8.1 was released as a security and maintenance release. As a best practice, always be sure to run the latest version of WordPress core!
WordPress Plugin Vulnerabilities
In this section, the latest WordPress plugin vulnerabilities have been disclosed. Each plugin listing includes the type of vulnerability, the version number if patched, and the severity rating.
1. WP DSGVO Tools

Plugin: WP DSGVO Tools
Vulnerability: Unauthenticated Plugin’s Settings Update to Stored Cross-Site Scripting
Patched in Version: 3.1.24 – plugin closed
Severity Score: High
2. Great Quotes
Plugin: Great Quotes
Vulnerability: Admin+ Stored Cross-Site Scripting
Patched in Version: No known fix – plugin closed
Severity Score: Low
3. WP Debugging
Plugin: WP Debugging
Vulnerability: Unauthenticated Plugin’s Settings Update
Patched in Version: 2.11.0
Severity Score: Medium
4. Check & Log Email
Plugin: Check & Log Email
Vulnerability: Admin+ SQL Injections
Patched in Version: 1.0.3
Severity Score: Medium
5. Permalink Manager Lite
Plugin: Permalink Manager Lite
Vulnerability: Admin+ SQL Injection
Patched in Version: 2.2.13.1
Severity Score: Medium
6. WooCommerce Product Table Lite

Plugin: WooCommerce Product Table Lite
Vulnerability: Reflected Cross-Site Scripting
Patched in Version: 2.4.0
Severity Score: Medium
7. WP Table Builder
Plugin: WP Table Builder
Vulnerability: Reflected Cross-Site Scripting
Patched in Version: 1.3.10
Severity Score: High
8. Visual Form Builder

Plugin: Visual Form Builder
Vulnerability: Admin+ Stored Cross-Site Scripting
Patched in Version: 3.0.4
Severity Score: Low
9. NinjaForms
Plugin: NinjaForms
Vulnerability: Admin+ Stored Cross-Site Scripting
Patched in Version: 3.5.8.2
Severity Score: Low
10. Wappointment

Plugin: Wappointment
Vulnerability: Unauthenticated Stored Cross-Site Scripting
Patched in Version: 2.2.5
Severity Score: High
11. Countdown and CountUp, WooCommerce Sales Timers

Plugin: Countdown and CountUp, WooCommerce Sales Timers
Vulnerability: CSRF to Stored Cross-Site Scripting
Patched in Version: 1.5.8
Severity Score: High
11. uListing

Plugin: uListing
Vulnerability: Settings Update via CSRF
Patched in Version: 2.0.6
Severity Score: Medium
Plugin: uListing
Vulnerability: Unauthenticated SQL Injection
Patched in Version: 2.0.4
Severity Score: High
Plugin: uListing
Vulnerability: Unauthenticated Privilege Escalation
Patched in Version: 2.0.6
Severity Score: Medium
Plugin: uListing
Vulnerability: Modify User Roles via CSRF
Patched in Version: 2.0.6
Severity Score: Medium
Plugin: uListing
Vulnerability: Multiple CSRF
Patched in Version: 2.0.6
Severity Score: Medium
Plugin: uListing
Vulnerability: Reflected Cross-Site Scripting
Patched in Version: 2.0.6
Severity Score: Medium
Plugin: uListing
Vulnerability: Authenticated IDOR
Patched in Version: 2.0.6
Severity Score: Medium
12. YITH Maintenance Mode
Plugin: YITH Maintenance Mode
Vulnerability: Multiple Admin+ Stored Cross-Site Scripting
Patched in Version: 1.4.0
Severity Score: Low
Plugin: YITH Maintenance Mode
Vulnerability: Admin+ Stored Cross-Site Scripting
Patched in Version: 1.3.8
Severity Score: Low
13. WordPress Contact Forms by Cimatti

Plugin: WordPress Contact Forms by Cimatti
Vulnerability: Admin+ Stored Cross-Site Scripting
Patched in Version: 1.4.12
Severity Score: Low
14. OG Tags
Plugin: OG Tags
Vulnerability: Plugin’s Settings Update via CSRF
Patched in Version: 2.0.2
Severity Score: Medium
15. Connections Business Directory

Plugin: Connections Business Directory
Vulnerability: Admin+ Stored Cross-Site Scripting
Patched in Version: 10.4.3
Severity Score: Low
16. Flat Preloader
Plugin: Flat Preloader
Vulnerability: Admin+ Stored Cross-Site Scripting
Patched in Version: 1.5.5
Severity Score: Medium
Plugin: Flat Preloader
Vulnerability: CSRF to Stored Cross-Site Scripting
Patched in Version: 1.54
Severity Score: High
17. Cool Tag Cloud
Plugin: Cool Tag Cloud
Vulnerability: Contributor+ Stored Cross-Site Scripting
Patched in Version: 2.26
Severity Score: Medium
18. underConstruction

Plugin: underConstruction
Vulnerability: Reflected Cross-Site Scripting
Patched in Version: 1.19
Severity Score: High
19. Restaurant Menu by MotoPress
Plugin: Restaurant Menu by MotoPress
Vulnerability: Authenticated Stored Cross Site Scripting
Patched in Version: No known fix – plugin closed
Severity Score: Low
20. AutomatorWP
Plugin: AutomatorWP
Vulnerability: Missing Authorization and Privilege Escalation
Patched in Version: 1.7.6
Severity Score: Medium
21. WP Reactions Lite
Plugin: WP Reactions Lite
Vulnerability: Authenticated Stored Cross Site Scripting
Patched in Version: 1.3.6
Severity Score: Low
22. Stylish Price List
Plugin: Stylish Price List
Vulnerability: Subscriber+ Arbitrary Image Upload
Patched in Version: 6.9.1
Severity Score: Medium
Plugin: Stylish Price List
Vulnerability: Unauthenticated Arbitrary Image Upload
Patched in Version: 6.9.0
Severity Score: Medium
23 Easy Social Icons
Plugin: Easy Social Icons
Vulnerability: Reflected Cross-Site Scripting
Patched in Version: 3.0.9
Severity Score: High
Plugin: Easy Social Icons
Vulnerability: Reflected Cross-Site Scripting
Patched in Version: 3.1.3
Severity Score: High
24. WPeMatico RSS Feed Fetcher
Plugin: WPeMatico RSS Feed Fetcher
Vulnerability: Admin+ Stored Cross-Site Scripting
Patched in Version: 2.6.12
Severity Score: Low
25. WordPress Download Manager

Plugin: WordPress Download Manager
Vulnerability: Admin+ Stored Cross-Site Scripting
Patched in Version: 3.2.16
Severity Score: Low
26. Modern Events Calendar Lite
Plugin: Modern Events Calendar Lite
Vulnerability: Authenticated Stored Cross Site Scripting
Patched in Version: 5.22.3
Severity Score: Low
27. Credova_Financial

Plugin: Credova_Financial
Vulnerability: Sensitive Information Disclosure
Patched in Version: 1.4.9
Severity Score: Medium
28. JS Job Manager
Plugin: JS Job Manager
Vulnerability: Unauthenticated Arbitrary Plugin Installation/Activation
Patched in Version: No known fix – plugin closed
Severity Score: Critical
29. Events Made Easy

Plugin: Events Made Easy
Vulnerability: Multi CSRF to Stored Cross-Site Scripting & Event Deletion
Patched in Version: 1.5.50
Severity Score: High
30. Stripe For WooCommerce

Plugin: Stripe For WooCommerce
Vulnerability: Missing Authorization Controls to Financial Account Hijacking
Patched in Version: 3.3.10
Severity Score: Medium
How to Protect Your WordPress Website From Vulnerable Plugins and Themes
As you can see from this report, lots of new WordPress plugin and theme vulnerabilities are disclosed each week. We know it can be difficult to stay on top of every reported vulnerability disclosure, so the iThemes Security Pro plugin makes it easy to make sure your site isn’t running a theme, plugin or WordPress core version with a known vulnerability.
1. Turn on the iThemes Security Pro Site Scanner
The iThemes Security Pro plugin’s Site Scanner scans for the #1 reason WordPress sites get hacked: outdated plugins and themes with known vulnerabilities. The Site Scanner checks your site for known vulnerabilities and automatically applies a patch if one is available.
To enable the Site Scan on new installs, navigate to the Site Check tab on the Features menu inside the plugin and click the toggle to enable the Site Scan.
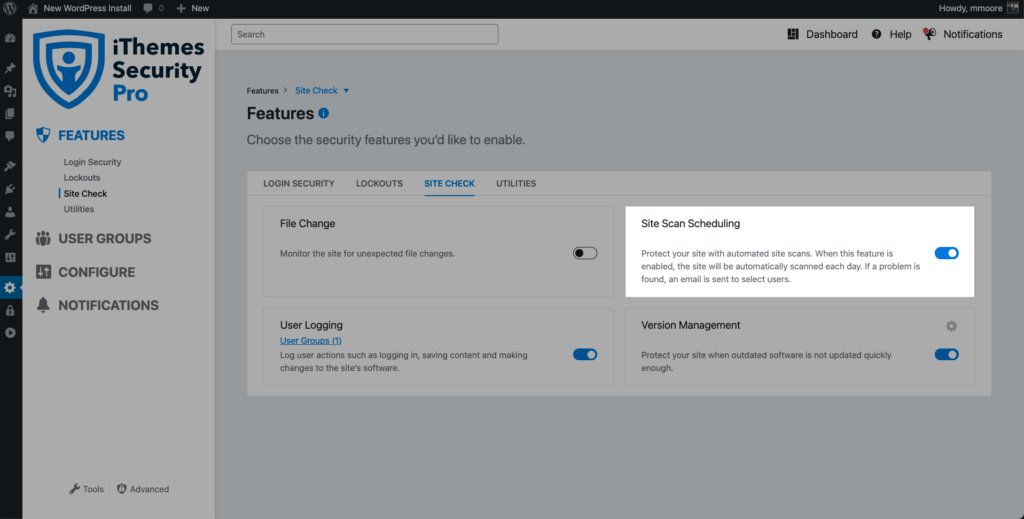
To trigger a manual Site Scan, click the Scan Now button on the Site Scan Security Dashboard card.
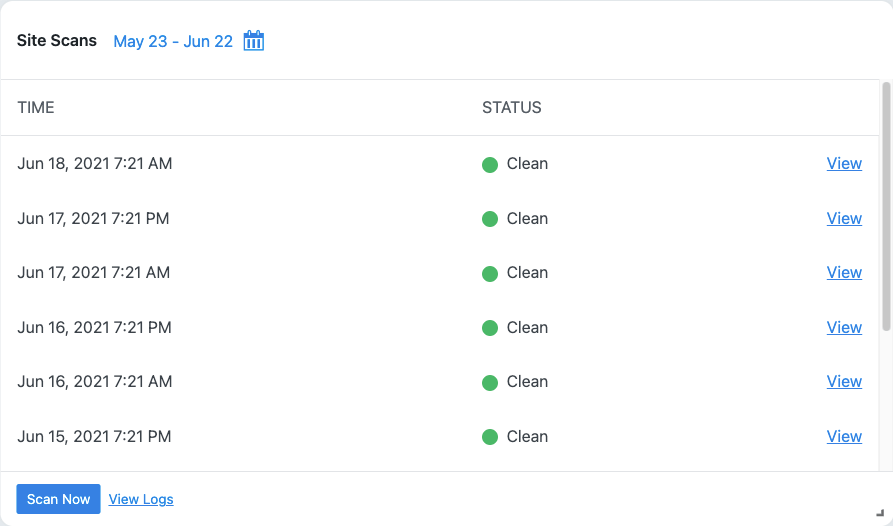
If the Site Scan detects a vulnerability, click the vulnerability link to view the details page.
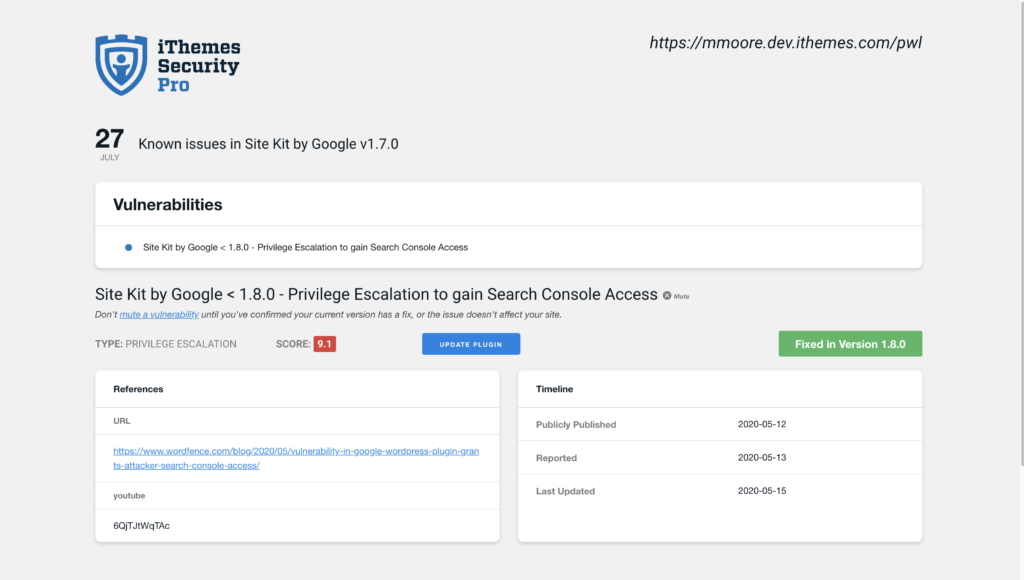
On the Site Scan vulnerability page, you will see if there is a fix available for the vulnerability. If there is a patch available, you can click the Update Plugin button to apply the fix on your website.
2. Turn on Version Management to Auto Update if Fixes Vulnerability
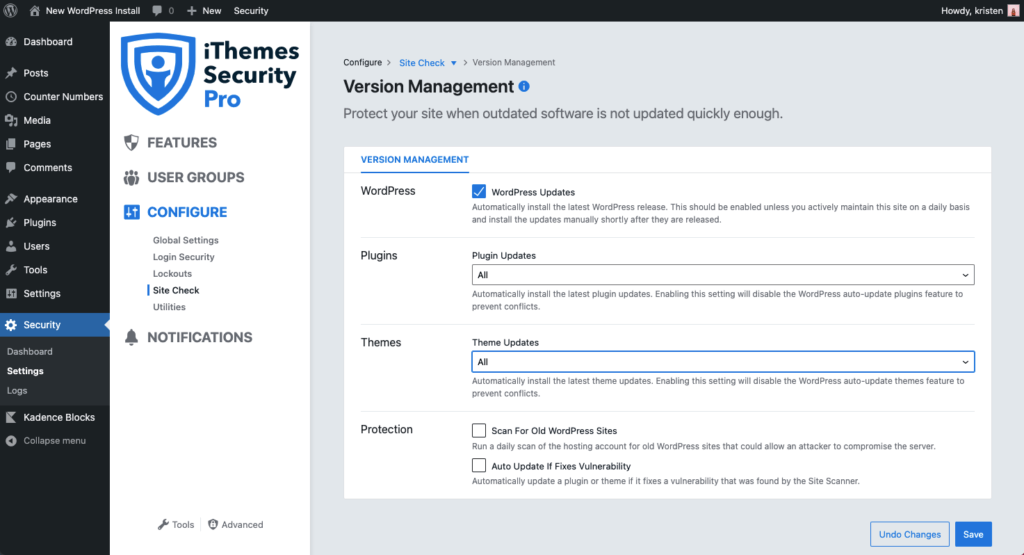
The Version Management feature in iThemes Security Pro integrates with the Site Scan to protect your site when outdated software is not updated quickly enough. Even the strongest security measures will fail if you are running vulnerable software on your website. These settings help protect your site with options to update to new versions automatically if a known vulnerability exists and a patch is available.
From the Settings page in iThemes Security Pro, navigate to the Features screen. Click the Site Check tab. From here, use the toggle to enable Version Management. Using the settings gear, you can configure even more settings, including how you want iThemes Security Pro to handle updates to WordPress, plugins, themes, and additional protection.
Make sure to select Auto Update if it Fixes a Vulnerability box so that iThemes Security Pro will automatically update a plugin or theme if it fixes a vulnerability that was found by the Site Scanner.
3. Get an Email Alert When iThemes Security Pro Finds a Known Vulnerability On Your Site
Once you’ve enabled Site Scan Scheduling, head to the Notification Center settings of the plugin. On this screen, scroll to the Site Scan Results section.
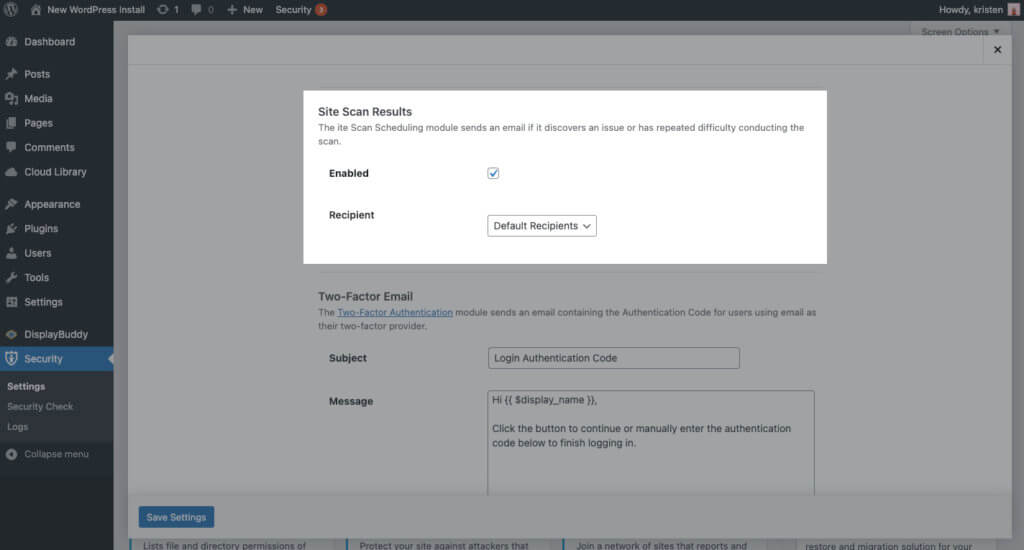
Click the box to enable the notification email and then click the Save Settings button.
Now, during any scheduled site scans, you’ll get an email if iThemes Security Pro discovers any known vulnerabilities. The email will look something like this.
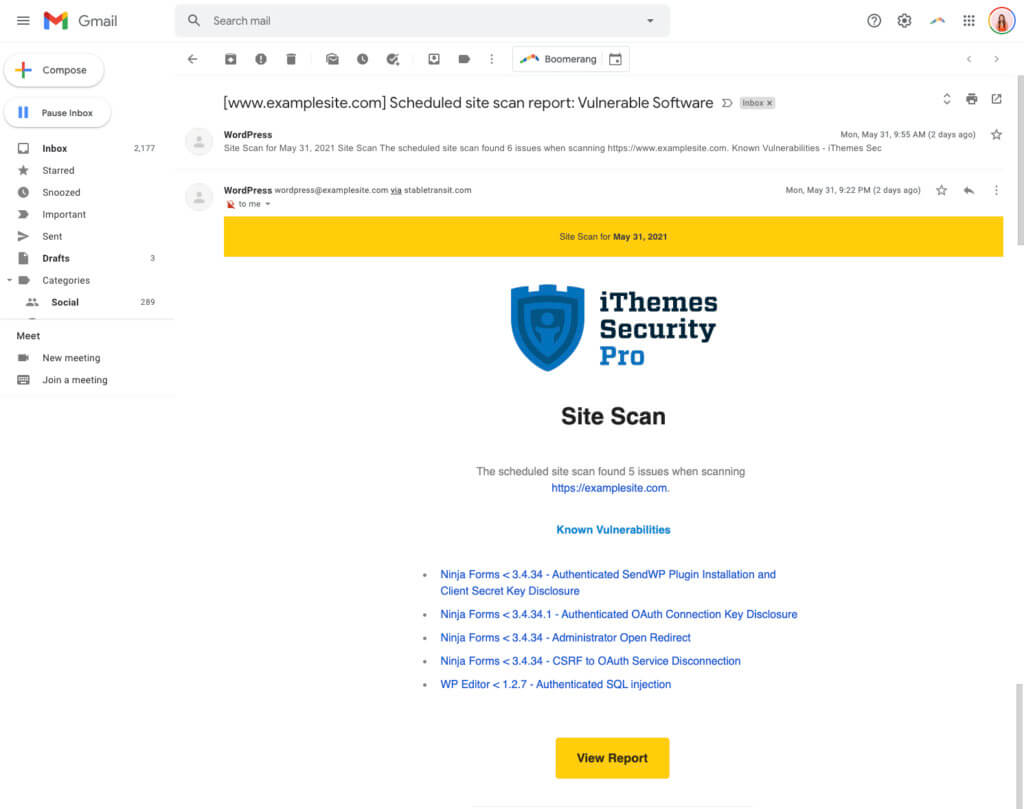
Get iThemes Security Pro and Rest a Little Easier Tonight
iThemes Security Pro, our WordPress security plugin, offers 50+ ways to secure and protect your website from common WordPress security vulnerabilities. With WordPress, two-factor authentication, brute force protection, strong password enforcement, and more, you can add extra layers of security to your website.
Get iThemes Security Pro
Sign up now — Get SolidWP updates and valuable content straight to your inbox
Sign up
Get started with confidence — risk free, guaranteed