WordPress Vulnerability Roundup: December 2020, Part 1
New WordPress plugin and theme vulnerabilities were disclosed during the first half of December. This post covers recent WordPress plugin, theme, and core vulnerabilities and what to do if you run one of the vulnerable plugins or themes on your website. The WordPress Vulnerability Roundup is divided into three different categories: WordPress core, WordPress plugins, and WordPress themes.

New WordPress plugin and theme vulnerabilities were disclosed during the first half of December. This post covers recent WordPress plugin, theme, and core vulnerabilities and what to do if you run one of the vulnerable plugins or themes on your website.
The WordPress Vulnerability Roundup is divided into three different categories: WordPress core, WordPress plugins, and WordPress themes.
WordPress Core Vulnerabilities
No new WordPress core vulnerabilities have been disclosed this month.
However, a new major version of WordPress core was just released yesterday. WordPress 5.6 includes several new features and improvements, so be sure to update.
WordPress Plugin Vulnerabilities
1. WPJobBoard

WPJobBoard versions below 5.7.0 have Unauthenticated SQL Injection, Reflected XSS, & XFS vulnerabilities.
2. WP Google Map Plugin
WP Google Map Plugin versions below 4.1.4 have an Authenticated SQL Injection vulnerability.
3. BuddyPress

BuddyPress versions below 6.4.0 Lack of Capability Check vulnerability.
4. Events Manager

Events Manager versions below 5.9.8 have a Cross-Site Scripting & an SQL Injection vulnerability.
5. Age Gate

Age Gate versions below 2.13.5 have an Unauthenticated Open Redirect vulnerability.
6. Canto
All versions of Canto have an Unauthenticated Blind SSRF vulnerability.
7. Profile Builder

Profile Builder versions below 3.3.3 have an Authenticated Blind SQL Injection vulnerability.
8. Paid Memberships Pro

Paid Memberships Pro versions below 2.5.1 have an Authenticated Cross-Site Scripting vulnerability.
9. Themify Portfolio Post

Themify Portfolio Post versions below 1.1.6 an Authenticated Stored Cross-Site Scripting vulnerability.
10. Easy WP SMTP

Easy WP SMTP versions below 1.4.3 have a Debug Log Disclosure vulnerability.
WordPress Theme Vulnerabilities
1. Wibar
Wibar versions below 1.2.1 has an Authenticated Stored Cross-Site Scripting vulnerability.
December Security Tip: Why You Need a Universal User for Support
Anytime you create a new user on your website, you are adding another entry point that a hacker could exploit. But there will likely be times you may need some outside help for your website, like when you are seeking support or after hiring an independent contractor. You need a safe, secure way to add temporary admin access to your website.
Granting Outside Access to your Website: Your Typical Bad Options
Typically, you have two options to provide external access to your website…. and neither are great.
1. Share Your Admin User’s Credentials
Your first and worst option is to share the username and password of your WordPress admin user.
Why Sharing Your Admin Credentials is a Terrible Idea
- Reduced Security – If you share your user’s credentials, you will have to disable two-factor authentication to allow the person using your credentials to login. Google shared on its blog that using two-factor authentication, or 2-step verification, can stop 100% of automated bot attacks. Disabling two-factor authentication, even for a short period of time, drastically reduces your website’s security.
- Inconvenient – Sharing your credentials requires you to change your password. If you forget to change your password, there are one or more people that have admin access to your website whenever they want it.
2. Create a Separate User for the Support Tech
While creating a brand new admin user for the support specialist is better than sharing your admin credentials, it still isn’t great.
Why Creating a User for the Support Tech is Terrible
- Increased Vulnerability – Creating a new administrator user adds another point of entry that could be exploited. If you don’t have a password policy in place, the support tech could choose a weak password, making your WordPress login more vulnerable to attack.
- Inconvenient – Going through the process of setting up a new user anytime you need outside help is time-consuming. You have to create the new user and then remember to delete the user when they no longer need access to your website. It is a WordPress security best practice to remove any unused users from your website.
Granting Outside Access to Your Website: The Better Way
The iThemes Security Pro Privilege Escalation feature allows you to grant a user extra capabilities temporarily.
Privilege Escalation makes it easy and safe to create a universal user that you can give to any outside developers or support techs that need temporary access to your website.
With Privilege Escalation, you can create a new user and name it Support and give it the Subscriber user role. The next time you need to provide temporary access to your website, you can bump the Support user from a subscriber to an administrator. We will walk through how to do this later in the post, but first, let’s talk about why Privilege Escalation is a better way of granting access to your website.
Why Privilege Escalation is Better
- Easy – You don’t have to create a new user every time you need to grant access to your website.
- Automatic – The privilege escalation only lasts for 24 hours. After 24 hours is up, the user automatically loses all the additional privileges. You don’t have to remember to remove users or change any passwords.
- No Sacrifice in Security – You can still require this universal support user to use the email method of two-factor to login, which means you have the same level security as you do with your other admin users. Because the actual user role is a subscriber, you don’t run any real risk leaving it on your website.
How to Use Privilege Escalation in iThemes Security Pro
To get started, enable Privilege Escalation on the main page of the security settings.
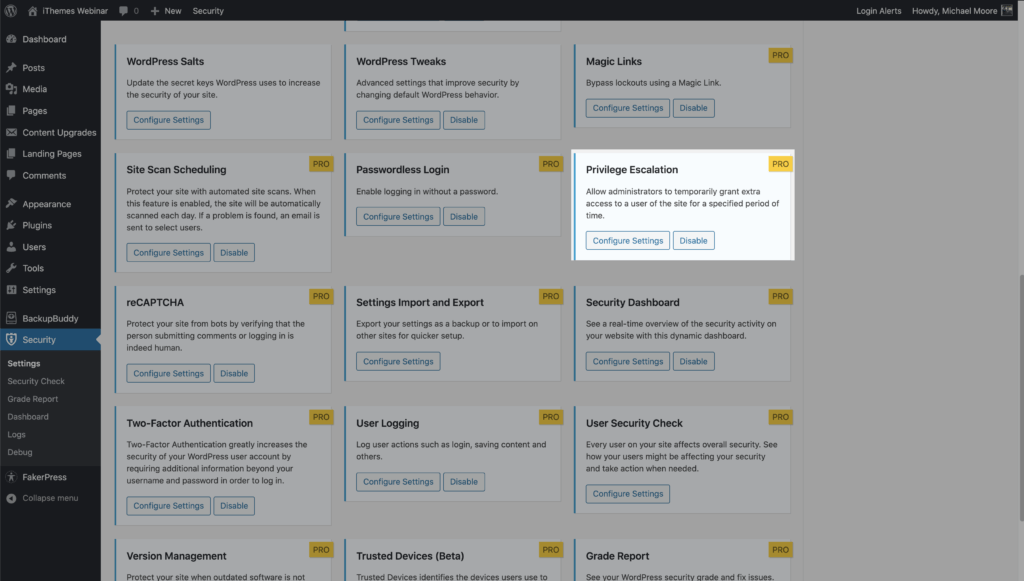
You can create a new user and name it Support and give it the Subscriber user role. The next time you need to provide temporary access to your website, navigate to your Support user’s Profile page.
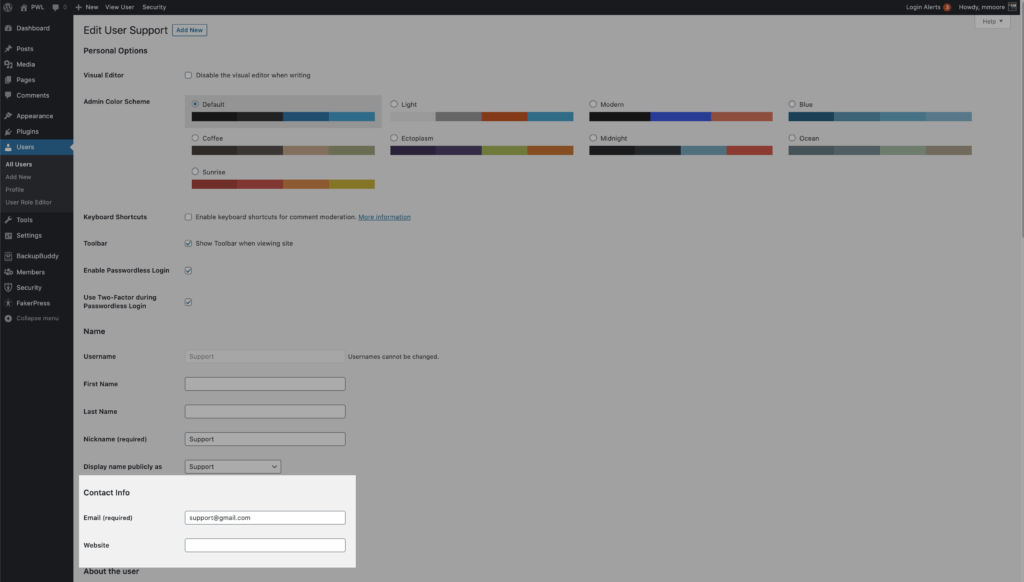
Update the email address to allow the outside support person to request a new password. Then scroll down until you see the Temporary Privilege Escalation settings. Click the Set Temporary Role toggle, and select Admin. The user will now have Admin access for the next 24 hours.
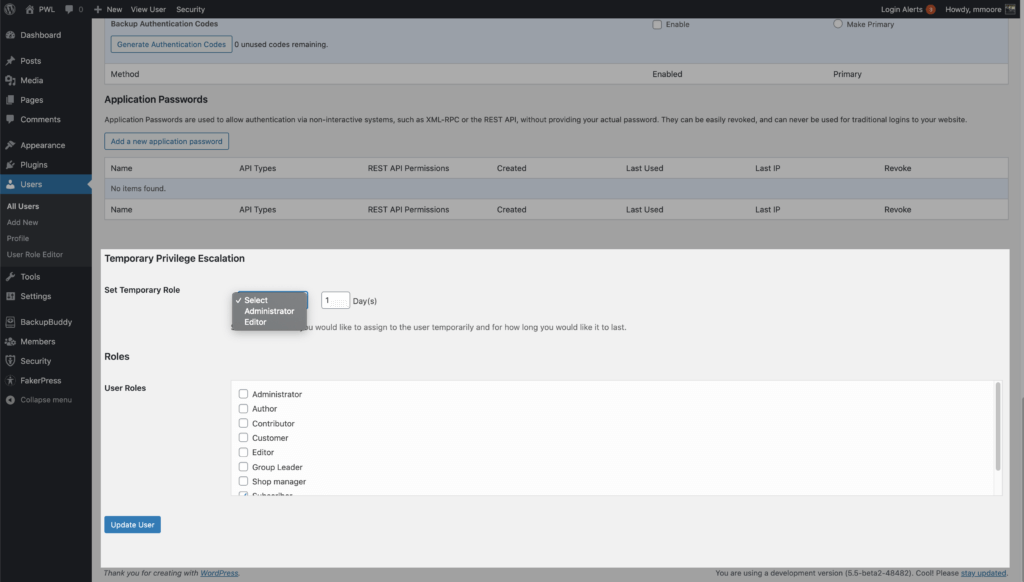
If they don’t need the full 24 hours, you can revoke the privilege escalation from the user profile page. If you need more than 24 hours, you can set the exact number of days you need in the Days field.
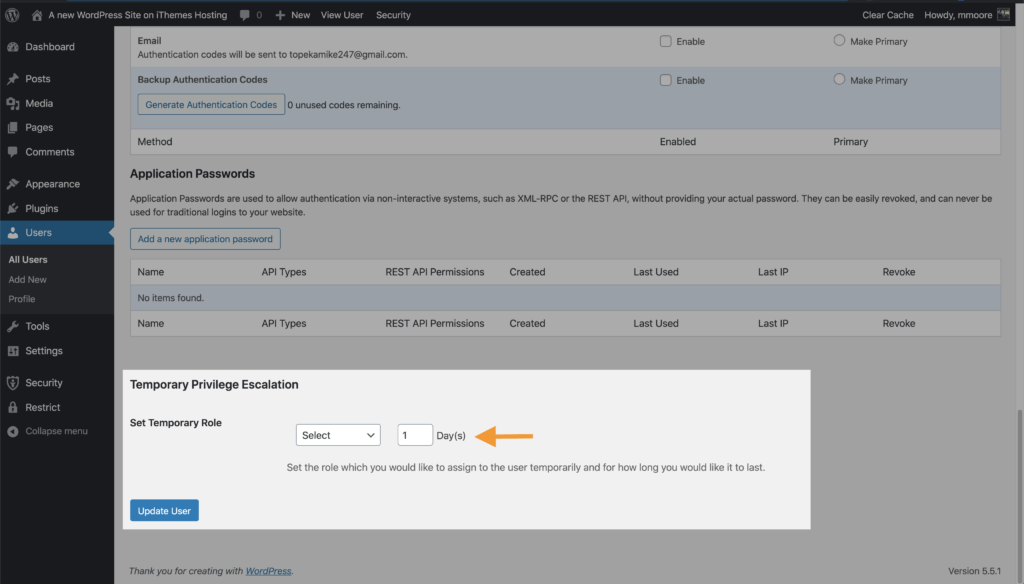
See how it works
A WordPress Security Plugin Can Help Secure Your Website
iThemes Security Pro, our WordPress security plugin, offers 50+ ways to secure and protect your website from common WordPress security vulnerabilities. With WordPress, two-factor authentication, brute force protection, strong password enforcement, and more, you can add an extra layer of security to your website.
Get iThemes Security Pro
Sign up now — Get SolidWP updates and valuable content straight to your inbox
Sign up
Get started with confidence — risk free, guaranteed