WordPress Vulnerability Roundup: February 2021, Part 2
New WordPress plugin and theme vulnerabilities were disclosed during the second half of February. This post covers the recent WordPress plugin, theme, and core vulnerabilities and what to do if you run one of the vulnerable plugins or themes on your website. The WordPress Vulnerability Roundup is divided into three different categories: WordPress core, WordPress plugins, and WordPress themes.

New WordPress plugin and theme vulnerabilities were disclosed during the second half of February. This post covers the recent WordPress plugin, theme, and core vulnerabilities and what to do if you run one of the vulnerable plugins or themes on your website.
The WordPress Vulnerability Roundup is divided into three different categories: WordPress core, WordPress plugins, and WordPress themes.
Each vulnerability will have a severity rating of Low, Medium, High, or Critical. The severity ratings are based on the Common Vulnerability Scoring System.
WordPress Core Vulnerabilities
However, WordPress version 5.6.2 was released to fix a few bugs introduced in WordPress version 5.6.1.
WordPress Plugin Vulnerabilities
1. Post SMTP Mailer/Email Log

Vulnerability: CSRF Nonce Bypass
Patched in Version: 2.0.21
Severity: Medium – CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:L/I:N/A:N
2. Better Search
Vulnerability: CSRF Nonce Bypass in Import/Export
Patched in Version: 2.5.3
Severity: Medium – CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:H/A:N
3. Theme Editor

Vulnerability: Authenticated Arbitrary File Download
Patched in Version: 2.6
Severity: Medium – CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:N/A:N
4. Customer Service Software & Support Ticket System

Vulnerability: Reflected Cross-Site Scripting
Patched in Version: 5.6.0
Severity: Medium – CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N
5. Zebra_Form Library
Vulnerability: Reflected Cross-Site Scripting
Patched in Version: No known fix
Severity: Medium – CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N
Affected Plugins:
Teaser Maker: No known fix – plugin closed
Ad Swapper: No known fix – plugin closed
Drug Search: No known fix – plugin closed
WP Inimat: No known fix – plugin closed
6. Ninja Forms
Vulnerability: Authenticated SendWP Plugin Installation and Client Secret Key Disclosure
Patched in Version: 3.4.34
Severity: Critical – CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H
Vulnerability: Authenticated OAuth Connection Key Disclosure
Patched in Version: 3.4.34
Severity: High – CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:C/C:N/I:H/A:N
Vulnerability: Administrator Open Redirect
Patched in Version: 3.4.34
Severity: Medium – CVSS:3.1/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N
Vulnerability: CSRF to OAuth Service Disconnection
Patched in Version: 3.4.34
Severity: Medium – CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:N/I:L/A:L
7. Custom Banners

Vulnerability: CSRF Nonce Bypass in saveCustomFields
Patched in Version: 3.3
Severity: Medium – CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:L/A:N
8. Process Steps Template Designer
Vulnerability: CSRF to Stored Cross-Site Scripting
Patched in Version: 1.3
Severity: Medium – CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N
9. eCommerce Product Catalog
Vulnerability: CSRF Nonce Bypass
Patched in Version: 3.0.18
Severity: Medium – CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:L/A:N
10. Backup Guard

Vulnerability: Authenticated Arbitrary File Upload
Patched in Version: 1.6.0
Severity: Critical – CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H
11. Responsive Menu
Vulnerability: CSRF to Settings Update
Patched in Version: 4.0.4
Severity: Medium– CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:L/A:L
Vulnerability: CSRF to Arbitrary File Upload
Patched in Version: 4.0.4
Severity: High– CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
Vulnerability: Authenticated Arbitrary File Upload
Patched in Version: 4.0.4
Severity: Critical– CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H
12. Orbit Fox by ThemeIsle

Vulnerability: Authenticated Stored Cross-Site Scripting
Patched in Version: 2.10.3
Severity: Medium – CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:C/C:L/I:L/A:N
Vulnerability: Authenticated Privilege Escalation
Patched in Version: 2.10.3
Severity: Critical – CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H
13. Testimonial Rotator

Vulnerability: Authenticated Stored Cross-Site Scripting
Patched in Version: No known fix
Severity: High – CVSS:3.1/AV:N/AC:H/PR:L/UI:R/S:C/C:H/I:H/A:H
14. WP Content Plus
Vulnerability: CSRF Nonce Bypass
Patched in Version: 3.2
Severity: High – CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:L/I:H/A:N
15. QuadMenu
Vulnerability: Unauthenticated RCE via compiler_save
Patched in Version: 2.0.7
Severity: Critical – CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
16. YITH WooCommerce Gift Cards Premium

Vulnerability: RCE via Arbitrary File Upload
Patched in Version: 3.3.1
Severity: Critical – CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
17. Photo Gallery by 10web

Vulnerability: Reflected Cross-Site Scripting
Patched in Version: 1.5.69
Severity: Medium – CVSS:3.1/AV:N/AC:H/PR:N/UI:R/S:C/C:L/I:L/A:N
18. Web-Stat
Vulnerability: API Key Disclosure
Patched in Version: 1.4.1
Severity: High – CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:L/I:L/A:L
19. NextGEN Gallery Pro
Vulnerability: Reflected Cross-Site Scripting
Patched in Version: 3.1.11
Severity: Medium – CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N
WordPress Theme Vulnerabilities
February Security Tip: Why You Should Be Logging Website Security Activity
Security logging should be an essential part of your WordPress security strategy. Why?
Insufficient logging and monitoring can lead to a delay in the detection of a security breach. Most breach studies show that the time to detect a breach is over 200 days!
That amount of time allows an attacker to breach other systems, modify, steal, or destroy more data. For this reason, “insufficient logging” landed on the OWASP top 10 of web application security risks.
WordPress security logs have several benefits in your overall security strategy, helping you:
- Identity and stop malicious behavior.
- Spot activity that can alert you of a breach.
- Assess how much damage was done.
- Aid in the repair of a hacked site.
If your site does get hacked, you will want to have the best information to aid in a quick investigation and recovery.
The good news is that iThemes Security Pro can help you implement website logging. iThemes Security Pro’s WordPress security logs tracks all these website activities for you:
Stats from your logs are then displayed in a real-time WordPress security dashboard that you can view from your WordPress admin dashboard.
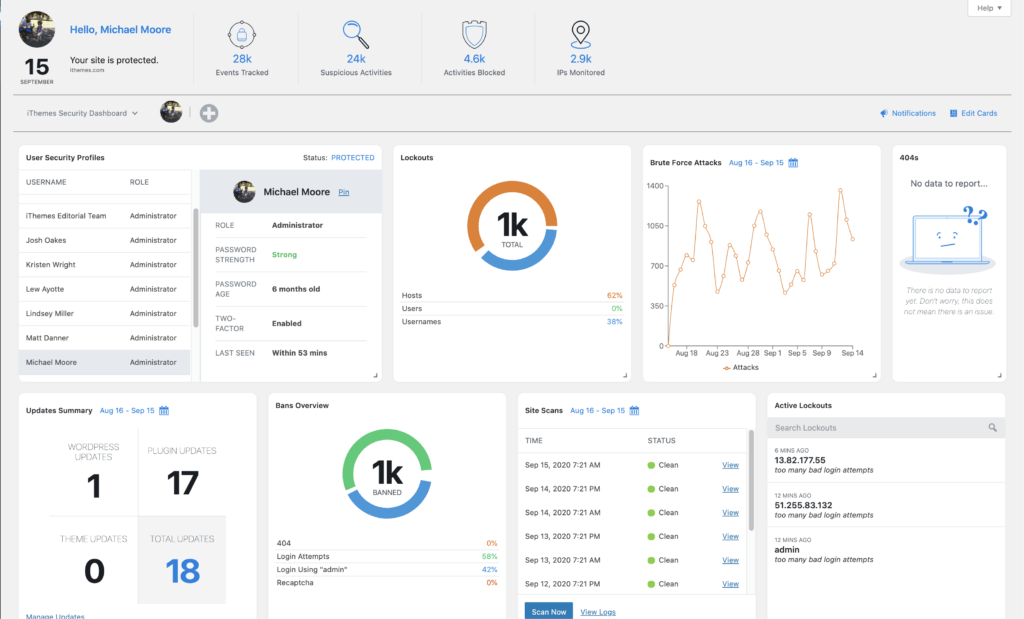
Check out this feature spotlight post where we unpack all the steps of adding WordPress security logs to your website using iThemes Security Pro.
See how it works
A WordPress Security Plugin Can Help Secure Your Website
iThemes Security Pro, our WordPress security plugin, offers 50+ ways to secure and protect your website from common WordPress security vulnerabilities. With WordPress, two-factor authentication, brute force protection, strong password enforcement, and more, you can add an extra layer of security to your website.
Get iThemes Security Pro
Sign up now — Get SolidWP updates and valuable content straight to your inbox
Sign up
Get started with confidence — risk free, guaranteed