WordPress Vulnerability Roundup: November 2019, Part 1
Several new WordPress plugin and theme vulnerabilities were disclosed during the first half of November, so we want to keep you aware. In this post, we cover recent WordPress plugin and theme vulnerabilities and what to do if you are running one of the vulnerable plugins or themes on your website.

Several new WordPress plugin and theme vulnerabilities were disclosed during the first half of November, so we want to keep you aware. In this post, we cover recent WordPress plugin and theme vulnerabilities and what to do if you are running one of the vulnerable plugins or themes on your website.
We divide the WordPress Vulnerability Roundup into four different categories:
 Safe SVG version 1.9.5 and below is vulnerable to a Cross-Site Scripting Bypass attack. The vulnerability allows an attacker to bypass the protection added by Safe SVG.
Safe SVG version 1.9.5 and below is vulnerable to a Cross-Site Scripting Bypass attack. The vulnerability allows an attacker to bypass the protection added by Safe SVG.
 Currency Switcher for WooCommerce version 2.11.1 has a Security Restrictions Bypass vulnerability that would allow an attacker to enable a currency not currently enabled in the settings.
Currency Switcher for WooCommerce version 2.11.1 has a Security Restrictions Bypass vulnerability that would allow an attacker to enable a currency not currently enabled in the settings.
 Tidio Live Chat version 4.1 and below is vulnerable to a Cross-Site Request Forgery leading to a Cross-Site Scripting attack. The vulnerability would allow an attacker to trick admins into adding a malicious payload that would be presented to all visitors.
Tidio Live Chat version 4.1 and below is vulnerable to a Cross-Site Request Forgery leading to a Cross-Site Scripting attack. The vulnerability would allow an attacker to trick admins into adding a malicious payload that would be presented to all visitors.
 IgniteUp – Coming Soon and Maintenance Mode version 3.4 and below has multiple vulnerabilities.
IgniteUp – Coming Soon and Maintenance Mode version 3.4 and below has multiple vulnerabilities.
 Blog2Social: Social Media Auto Post & Scheduler version 5.8.1 has a Cross-Site Scripting vulnerability. The vulnerability would allow an attacker to execute arbitrary HTML and JavaScript code that could be executed via a malicious link.
Blog2Social: Social Media Auto Post & Scheduler version 5.8.1 has a Cross-Site Scripting vulnerability. The vulnerability would allow an attacker to execute arbitrary HTML and JavaScript code that could be executed via a malicious link.
 WP Google Review Slider version 6.1 is vulnerable to an Authenticated SQL Injection attack.
WP Google Review Slider version 6.1 is vulnerable to an Authenticated SQL Injection attack.
 The YITH suite of WooCommerce plugins is vulnerable to an Authenticated Settings Change attack. This chart summarizes all 39 vulnerable YITH plugins:
The YITH suite of WooCommerce plugins is vulnerable to an Authenticated Settings Change attack. This chart summarizes all 39 vulnerable YITH plugins:
 Zoner Real Estate Theme version 4.1.1 and below a Persistent Cross-Site Scripting and Insecure Direct Object Reference vulnerabilities.
Zoner Real Estate Theme version 4.1.1 and below a Persistent Cross-Site Scripting and Insecure Direct Object Reference vulnerabilities.


 According to WordFence, there has been an uptick in the WP-VCD malvertising campaign. This particular malware is quite nasty as it is very difficult to remove from an infected site completely, and it can spread to other WordPress sites on the server. The most frustrating part for site owners that have been affected by the WP-VCD malware is that they infected their own site. Site owners who have installed free and pirated versions of paid plugins and themes, got a little more than they bargained for. The pirated software included malicious code that created a back door with a welcome mat for the WP-VCD virus.
On day 1 of the iThemes WordPress Disaster Week, we covered how to prevent a security disaster. One of the significant things that we covered was limiting PHP exploit opportunities by only installing software from trusted sources. Having a site infected with malware is always made worse when you know that it could have and should have been prevented.
According to WordFence, there has been an uptick in the WP-VCD malvertising campaign. This particular malware is quite nasty as it is very difficult to remove from an infected site completely, and it can spread to other WordPress sites on the server. The most frustrating part for site owners that have been affected by the WP-VCD malware is that they infected their own site. Site owners who have installed free and pirated versions of paid plugins and themes, got a little more than they bargained for. The pirated software included malicious code that created a back door with a welcome mat for the WP-VCD virus.
On day 1 of the iThemes WordPress Disaster Week, we covered how to prevent a security disaster. One of the significant things that we covered was limiting PHP exploit opportunities by only installing software from trusted sources. Having a site infected with malware is always made worse when you know that it could have and should have been prevented.
Summary of WordPress Vulnerabilities for
- 1. WordPress core
- 2. WordPress plugins
- 3. WordPress themes
- 4. Breaches from around the web
WordPress Core Security Update
No new WordPress vulnerabilities disclosed in the first half of November.
WordPress 5.3 did drop this week, so be sure to update your sites as soon as possible. Here’s a quick look at the top 20 new features and improvements in WordPress 5.3.
WordPress Plugin Vulnerabilities
Several new WordPress plugin vulnerabilities have been discovered this October. Make sure to follow the suggested action below to update the plugin or completely uninstall it.1. Safe SVG
 Safe SVG version 1.9.5 and below is vulnerable to a Cross-Site Scripting Bypass attack. The vulnerability allows an attacker to bypass the protection added by Safe SVG.
Safe SVG version 1.9.5 and below is vulnerable to a Cross-Site Scripting Bypass attack. The vulnerability allows an attacker to bypass the protection added by Safe SVG.
What You Should Do
The vulnerability has been patched, and you should update it to version 1.9.6.
2. Currency Switcher for WooCommerce
 Currency Switcher for WooCommerce version 2.11.1 has a Security Restrictions Bypass vulnerability that would allow an attacker to enable a currency not currently enabled in the settings.
Currency Switcher for WooCommerce version 2.11.1 has a Security Restrictions Bypass vulnerability that would allow an attacker to enable a currency not currently enabled in the settings.
What You Should Do
The vulnerability has been patched, and you should update it to version 2.11.2.
3. Tidio Live Chat
 Tidio Live Chat version 4.1 and below is vulnerable to a Cross-Site Request Forgery leading to a Cross-Site Scripting attack. The vulnerability would allow an attacker to trick admins into adding a malicious payload that would be presented to all visitors.
Tidio Live Chat version 4.1 and below is vulnerable to a Cross-Site Request Forgery leading to a Cross-Site Scripting attack. The vulnerability would allow an attacker to trick admins into adding a malicious payload that would be presented to all visitors.
What You Should Do
The vulnerability has been patched, and you should update it to version 4.2.
4. IgniteUp – Coming Soon and Maintenance Mode
 IgniteUp – Coming Soon and Maintenance Mode version 3.4 and below has multiple vulnerabilities.
IgniteUp – Coming Soon and Maintenance Mode version 3.4 and below has multiple vulnerabilities.
- Arbitrary File Deletion
- HTML injection & CSRF in email messages
- Stored Cross-Site Scripting
- Disclosure of subscribers’ email address
- Arbitrary subscriber deletion
- Arbitrary plugin’s template switch
What You Should Do
The vulnerabilities have been patched, and you should update it to version 3.4.1.
5. Blog2Social: Social Media Auto Post & Scheduler
 Blog2Social: Social Media Auto Post & Scheduler version 5.8.1 has a Cross-Site Scripting vulnerability. The vulnerability would allow an attacker to execute arbitrary HTML and JavaScript code that could be executed via a malicious link.
Blog2Social: Social Media Auto Post & Scheduler version 5.8.1 has a Cross-Site Scripting vulnerability. The vulnerability would allow an attacker to execute arbitrary HTML and JavaScript code that could be executed via a malicious link.
What You Should Do
The vulnerability has been patched, and you should update it to version 5.9.
6. WP Google Review Slider
 WP Google Review Slider version 6.1 is vulnerable to an Authenticated SQL Injection attack.
WP Google Review Slider version 6.1 is vulnerable to an Authenticated SQL Injection attack.
What You Should Do
The vulnerability has been patched, and you should update it to version 6.2.
7. YITH Plugin Framework (39 Individual Plugins)
 The YITH suite of WooCommerce plugins is vulnerable to an Authenticated Settings Change attack. This chart summarizes all 39 vulnerable YITH plugins:
The YITH suite of WooCommerce plugins is vulnerable to an Authenticated Settings Change attack. This chart summarizes all 39 vulnerable YITH plugins:
Summary of YITH Plugin Vulnerabilities
Type
Vulnerability
Fix
YITH Plugins
The vulnerability has been patched, and you should update it to
version 2.2.14.
The vulnerability has been patched, and you should update it to
version 2.3.15.
The vulnerability has been patched, and you should update to version
1.3.15.
The vulnerability has been patched, and you should update to version
1.3.12.
The vulnerability has been patched, and you should update to version
1.7.1.
The vulnerability has been patched, and you should update to version
1.3.21.
The vulnerability has been patched, and you should update it to
version 1.3.7.
The vulnerability has been patched, and you should update it to
version 1.4.9.
The vulnerability has been patched, and you should update it to
version 1.3.6.
The vulnerability has been patched, and you should update it to
version 1.2.11.
The vulnerability has been patched, and you should update it to
version 1.2.13.
The vulnerability has been patched, and you should update it to
version 1.2.1.
The vulnerability has been patched, and you should update it to
version 1.2.1.
The vulnerability has been patched, and you should update it to
version 1.5.23.
The vulnerability has been patched, and you should update it to
version 1.3.8.
The vulnerability has been patched, and you should update it
to version 1.3.6.
The vulnerability has been patched, and you should update it
to version 1.6.3.
The vulnerability has been patched, and you should update
it to version 1.4.5.
The vulnerability has been patched, and you should
update it to version 1.1.17.
The vulnerability has been patched, and you should
update it to version 1.2.14.
The vulnerability has been patched, and you should
update it to version 1.7.5.
The vulnerability has been patched, and you should
update it to version 1.8.13.
The vulnerability has been patched, and you
should update it to version 1.1.8.
The vulnerability has been patched, and you
should update it to version 1.1.13.
The vulnerability has been patched, and you
should update it to version 1.3.13.
The vulnerability has been patched, and
you should update it to version 1.2.15.
The vulnerability has been patched, and
you should update it to version 2.0.2.
The vulnerability has been patched,
and you should update it to version
1.3.11.
The vulnerability has been patched,
and you should update it to version
1.3.6.
The vulnerability has been
patched, and you should update it
to version 1.3.6.
The vulnerability has been
patched, and you should update
it to version 1.0.12.
The vulnerability has been
patched, and you should update
it to version 1.1.13.
The vulnerability has been
patched, and you should
update it to version 1.1.13.
The vulnerability has been
patched, and you should
update it to version
2.1.4.
The vulnerability has
been patched, and you
should update it to
version 3.4.1.
The vulnerability has
been patched, and you
should update it to
version 1.2.0.
The vulnerability
has been patched,
and you should
update it to version
1.2.0.
The vulnerability
has been patched,
and you should
update it to
version 1.2.6.
The
vulnerability
has been
patched, and you
should update it
to version
1.2.8.
WordPress Themes
1. Zoner – Real Estate Theme
 Zoner Real Estate Theme version 4.1.1 and below a Persistent Cross-Site Scripting and Insecure Direct Object Reference vulnerabilities.
Zoner Real Estate Theme version 4.1.1 and below a Persistent Cross-Site Scripting and Insecure Direct Object Reference vulnerabilities.
What You Should Do
The vulnerabilities have not been patched. Keep an eye on the changelog for an update that includes a fix.
How to Be Proactive About WordPress Theme & Plugin Vulnerabilities
Running outdated software is the number one reason WordPress sites are hacked. It is crucial to the security of your WordPress site that you have an update routine. You should be logging into your sites at least once a week to perform updates.Automatic Updates Can Help
Automatic updates are a great choice for WordPress websites that don’t change very often. Lack of attention often leaves these sites neglected and vulnerable to attacks. Even with recommended security settings, running vulnerable software on your site can give an attacker an entry point into your site. Using the iThemes Security Pro plugin’s Version Management feature, you can enable automatic WordPress updates to ensure you are getting the latest security patches. These settings help protect your site with options to automatically update to new versions or to increase user security when the site’s software is outdated.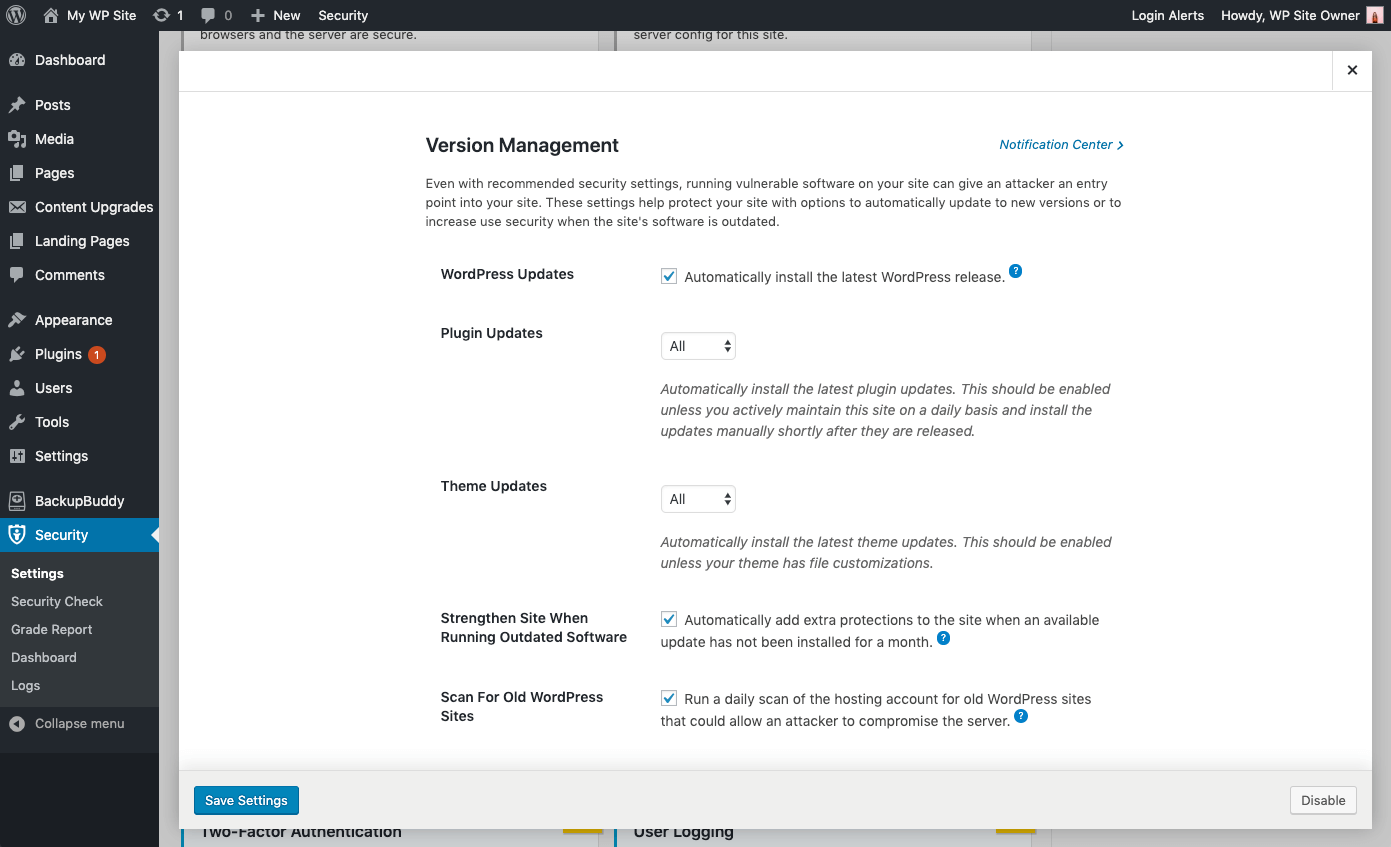
Version Management Update Options
- WordPress Updates –Automatically install the latest WordPress release.
- Plugin Automatic Updates – Automatically install the latest plugin updates. This should be enabled unless you actively maintain this site on a daily basis and install the updates manually shortly after they are released.
- Theme Automatic Updates – Automatically install the latest theme updates. This should be enabled unless your theme has file customizations.
- Granular Control over Plugin and Theme updates – You may have plugins/themes that you’d like to either manually update, or delay the update until the release has had time to prove stable. You can choose Custom for the opportunity to assign each plugin or theme to either update immediately (Enable), not update automatically at all (Disable) or update with a delay of a specified amount of days (Delay).
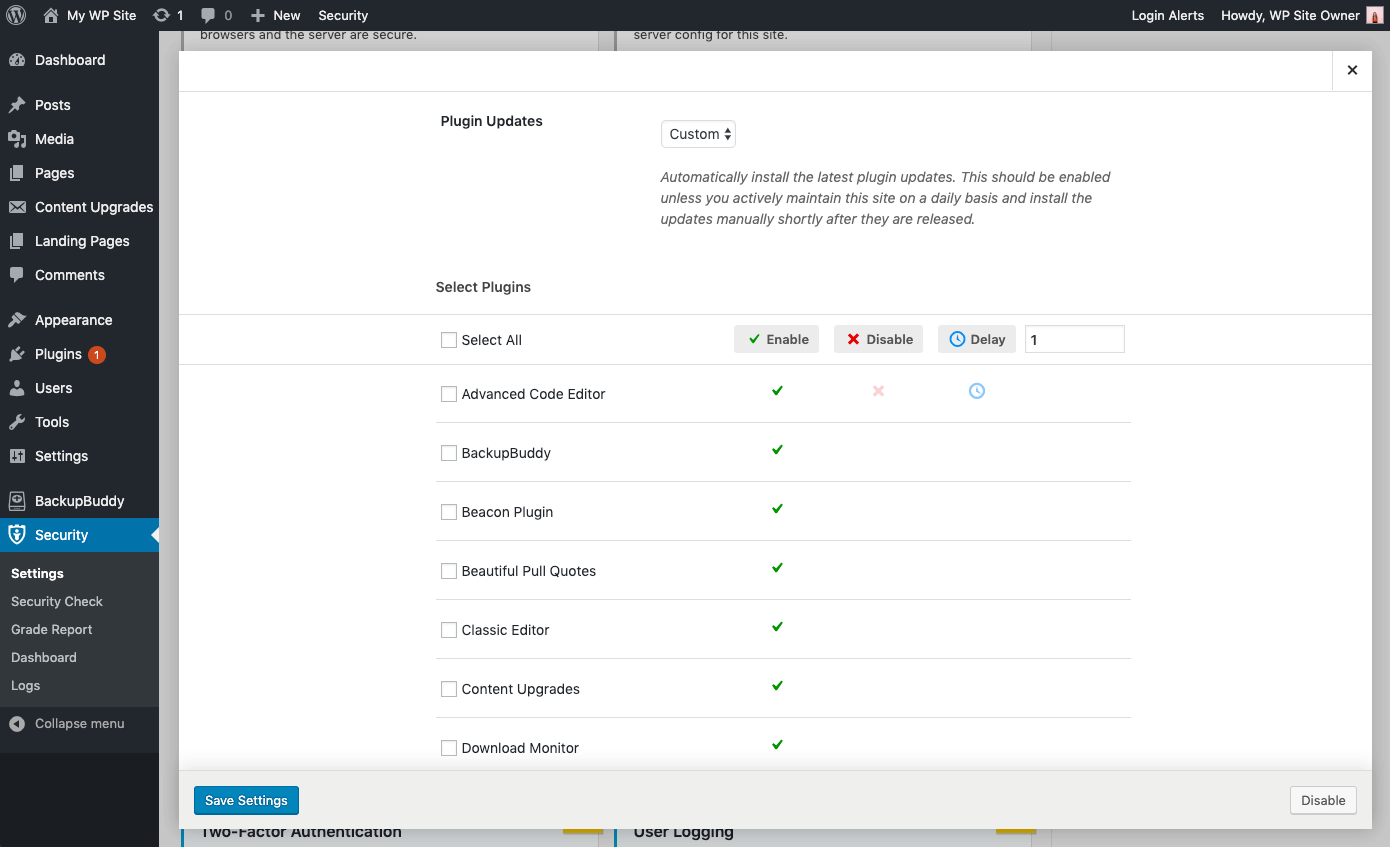
Strengthening and Alerting to Critical Issues
- Strengthen Site When Running Outdated Software – Automatically add extra protections to the site when an available update has not been installed for a month. The iThemes Security plugin will automatically enable stricter security when an update has not been installed for a month. First, it will force all users that do not have two-factor enabled to provide a login code sent to their email address before logging back in. Second, it will disable the WP File Editor (to block people from editing plugin or theme code), XML-RPC pingbacks, and block multiple authentication attempts per XML-RPC request (both of which will make XML-RPC stronger against attacks without having to turn it off completely).
- Scan for Other Old WordPress Sites – This will checks for other outdated WordPress installs on your hosting account. A single outdated WordPress site with a vulnerability could allow attackers to compromise all the other sites on the same hosting account.
- Send Email Notifications – For issues that require intervention, an email is sent to admin-level users.
Breaches From Around the Web
1. WordPress Users Infect Own Sites With Pirated Plugins & Themes
 According to WordFence, there has been an uptick in the WP-VCD malvertising campaign. This particular malware is quite nasty as it is very difficult to remove from an infected site completely, and it can spread to other WordPress sites on the server. The most frustrating part for site owners that have been affected by the WP-VCD malware is that they infected their own site. Site owners who have installed free and pirated versions of paid plugins and themes, got a little more than they bargained for. The pirated software included malicious code that created a back door with a welcome mat for the WP-VCD virus.
On day 1 of the iThemes WordPress Disaster Week, we covered how to prevent a security disaster. One of the significant things that we covered was limiting PHP exploit opportunities by only installing software from trusted sources. Having a site infected with malware is always made worse when you know that it could have and should have been prevented.
According to WordFence, there has been an uptick in the WP-VCD malvertising campaign. This particular malware is quite nasty as it is very difficult to remove from an infected site completely, and it can spread to other WordPress sites on the server. The most frustrating part for site owners that have been affected by the WP-VCD malware is that they infected their own site. Site owners who have installed free and pirated versions of paid plugins and themes, got a little more than they bargained for. The pirated software included malicious code that created a back door with a welcome mat for the WP-VCD virus.
On day 1 of the iThemes WordPress Disaster Week, we covered how to prevent a security disaster. One of the significant things that we covered was limiting PHP exploit opportunities by only installing software from trusted sources. Having a site infected with malware is always made worse when you know that it could have and should have been prevented.
Summary of WordPress Vulnerabilities for
November 2019, Part 1
Type
Vulnerability
Fix
Core
No WordPress Core vulnerabilities were disclosed in the first half of November 2019.
Plugins
Safe SVG version 1.9.5 and below is vulnerable to a Cross-Site Scripting Bypass attack.
The vulnerability has been patched, and you should update it to version 1.9.6.
Currency Switcher for WooCommerce version 2.11.1 and below is vulnerable to a Security Restriction Bypass attack.
The vulnerability has been patched, and you should update it to version 2.11.2.
Tidio Live Chat version 4.1 and below is vulnerable to a Cross-Site Request Forgery leading to a Cross-Site Scripting attack.
The vulnerability has been patched, and you should update to version 4.2.
IgniteUp – Coming Soon and Maintenance Mode version 3.4 and below has multipleVulnerabilities.
The vulnerability has been patched, and you should update to version 3.4.1.
Blog2Social: Social Media Auto Post & Scheduler version 5.8.1 and below is vulnerable to a Cross-Site Scripting attack.
The vulnerability has been patched, and you should update to version 5.9.
WP Google Review Slider version 6.1 and below is vulnerable to an Authenticated SQL Injectionattack.
The vulnerability has been patched, and you should update to version 6.2.
YITH Plugin Framework The YITH suite of WooCommerce plugins is vulnerable to an Authenticated Settings Change attack.
The vulnerability has been patched, and you should update.
A WordPress Security Plugin Can Help Secure Your Website
iThemes Security Pro, our WordPress security plugin, offers 30+ ways to secure and protect your website from common WordPress security vulnerabilities. With WordPress two-factor authentication, brute force protection, strong password enforcement, and more, you can add an extra layer of security to your website. [content_upgrade cu_id=”51030″]Get simple tips for better WordPress security. Download the new ebook: WordPress Security Pocket Guide[content_upgrade_button]Download now[/content_upgrade_button][/content_upgrade]Get iThemes Security Pro
Sign up now — Get SolidWP updates and valuable content straight to your inbox
Sign up
Placeholder text
Placeholder text
Get started with confidence — risk free, guaranteed