WordPress Vulnerability Roundup: October 2019, Part 1
Several new WordPress plugin and theme vulnerabilities were disclosed during the first half of October, so we want to keep you aware. In this post, we cover recent WordPress plugin and theme vulnerabilities and what to do if you are running one of the vulnerable plugins or themes on your website. We divide the WordPress Vulnerability Roundup into four different categories: 1.

- 1. WordPress core
- 2. WordPress plugins
- 3. WordPress themes
- 4. Breaches from around the web
WordPress Core Security Update
WordPress 5.2.3 and below has several vulnerabilities:- Cross-Site Scripting
- Unauthenticated Posts
- Cross-Site Scripting leading to a Javascript Injection
- JSON Cache Poisoning
- Server-Side Request Forgery
- Referrer Validation in the admin.
What You Should Do
WordPress Plugin Vulnerabilities
Several new WordPress plugin vulnerabilities have been discovered this October. Make sure to follow the suggested action below to update the plugin or completely uninstall it.1. All In One WP Security & Firewall
 All In One WP Security & Firewall version 4.4.1 and below has an Open Redirect that exposes the “hidden” login page.
If you are still relying on a “hidden” login to secure your WordPress login, it is time to update your methods. Check out our 5 Simple Rules for WordPress Login Security.
All In One WP Security & Firewall version 4.4.1 and below has an Open Redirect that exposes the “hidden” login page.
If you are still relying on a “hidden” login to secure your WordPress login, it is time to update your methods. Check out our 5 Simple Rules for WordPress Login Security.
What You Should Do
2. Popup Maker
 Popup Maker version 1.8.12 and below has a Broken Authentication vulnerability.
Popup Maker version 1.8.12 and below has a Broken Authentication vulnerability.
What You Should Do
3. iThemes Sync
 iThemes Sync version 2.0.17 and below has an Insufficient Secure Key Validation Vulnerability. The vulnerability could lead to a full compromise of a WordPress site, so confirm your site is running version 2.0.18
iThemes Sync version 2.0.17 and below has an Insufficient Secure Key Validation Vulnerability. The vulnerability could lead to a full compromise of a WordPress site, so confirm your site is running version 2.0.18
What You Should Do
4. Download Plugins and Themes from Dashboard
 Download Plugins and Themes from Dashboard version 1.5.0 and below is vulnerable to an Unauthenticated Stored XSS attack.
Download Plugins and Themes from Dashboard version 1.5.0 and below is vulnerable to an Unauthenticated Stored XSS attack.
What You Should Do
5. wpDataTables
 wpDataTables version 2.0.7 and below is vulnerable to a Cross-Site Scripting and SQL Injection attack.
wpDataTables version 2.0.7 and below is vulnerable to a Cross-Site Scripting and SQL Injection attack.
What You Should Do
6. Lara’s Google Analytics
 Lara’s Google Analytics 2.0.4 and below is vulnerable to an Authenticated Stored Cross-Site Scripting attack.
Lara’s Google Analytics 2.0.4 and below is vulnerable to an Authenticated Stored Cross-Site Scripting attack.
What You Should Do
7. Export Users to CSV
 Export Users to CSV version 1.3 and below has an Unauthorized CSV Access vulnerability.
Export Users to CSV version 1.3 and below has an Unauthorized CSV Access vulnerability.
What You Should Do
8. SoundPress Plugin
 SoundPress Plugin version 2.2.0 and below is vulnerable to a Cross-Site Scripting attack.
SoundPress Plugin version 2.2.0 and below is vulnerable to a Cross-Site Scripting attack.
What You Should Do
WordPress Themes
How to Be Proactive About WordPress Theme & Plugin Vulnerabilities
Running outdated software is the number one reason WordPress sites are hacked. It is crucial to the security of your WordPress site that you have an update routine. You should be logging into your sites at least once a week to perform updates.Automatic Updates Can Help
Automatic updates are a great choice for WordPress websites that don’t change very often. Lack of attention often leaves these sites neglected and vulnerable to attacks. Even with recommended security settings, running vulnerable software on your site can give an attacker an entry point into your site. Using the iThemes Security Pro plugin’s Version Management feature, you can enable automatic WordPress updates to ensure you are getting the latest security patches. These settings help protect your site with options to automatically update to new versions or to increase user security when the site’s software is outdated.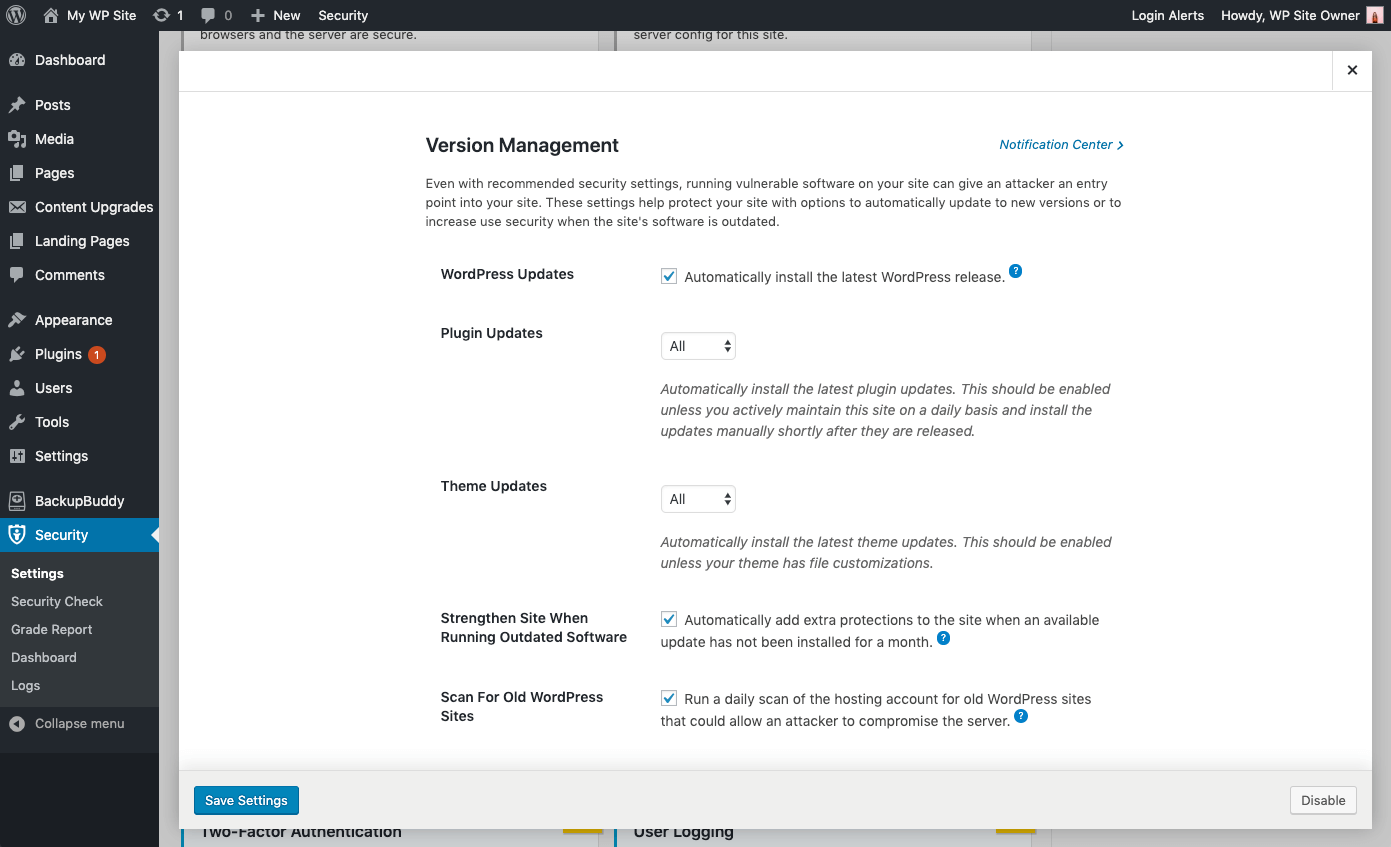
Version Management Update Options
- WordPress Updates –Automatically install the latest WordPress release.
- Plugin Automatic Updates – Automatically install the latest plugin updates. This should be enabled unless you actively maintain this site on a daily basis and install the updates manually shortly after they are released.
- Theme Automatic Updates – Automatically install the latest theme updates. This should be enabled unless your theme has file customizations.
- Granular Control over Plugin and Theme updates – You may have plugins/themes that you’d like to either manually update, or delay the update until the release has had time to prove stable. You can choose Custom for the opportunity to assign each plugin or theme to either update immediately (Enable), not update automatically at all (Disable) or update with a delay of a specified amount of days (Delay).
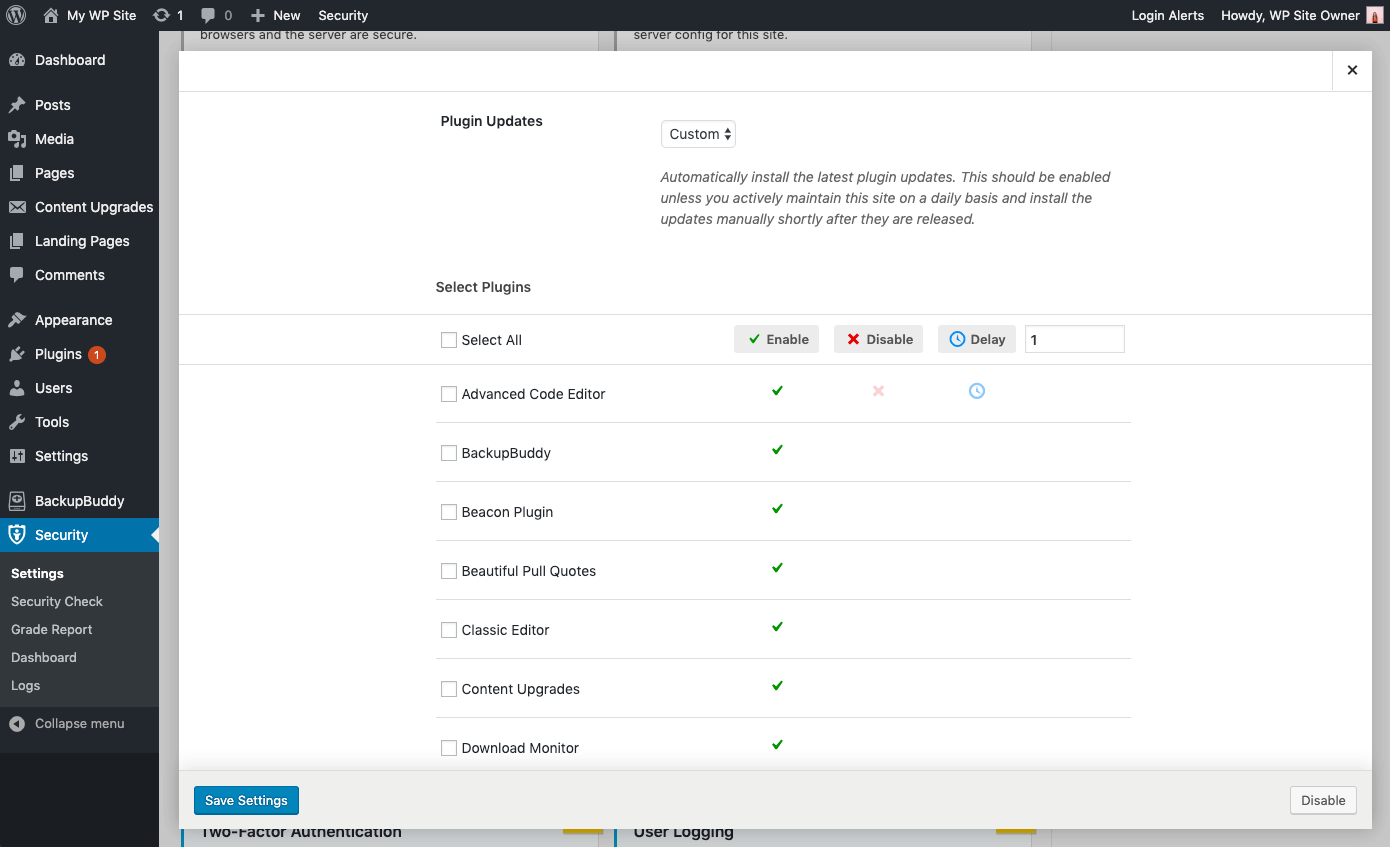
Strengthening and Alerting to Critical Issues
- Strengthen Site When Running Outdated Software – Automatically add extra protections to the site when an available update has not been installed for a month. The iThemes Security plugin will automatically enable stricter security when an update has not been installed for a month. First, it will force all users that do not have two-factor enabled to provide a login code sent to their email address before logging back in. Second, it will disable the WP File Editor (to block people from editing plugin or theme code), XML-RPC pingbacks, and block multiple authentication attempts per XML-RPC request (both of which will make XML-RPC stronger against attacks without having to turn it off completely).
- Scan for Other Old WordPress Sites – This will checks for other outdated WordPress installs on your hosting account. A single outdated WordPress site with a vulnerability could allow attackers to compromise all the other sites on the same hosting account.
- Send Email Notifications – For issues that require intervention, an email is sent to admin-level users.
Breaches From Around the Web
1. Hackers Using Gifs to Attack Drupal
 Akami–a security research company–has noticed an increase in attacks embedding malicious codes inside .gif files. The good news is that Drupal patched this vulnerability more than a year ago. The bad news is that poorly maintained sites still haven’t been updated.
The number one reason malicious attacks are successful is due to outdated software. Don’t be the guy/gal whose site is compromised by a year old update. Update your site
Akami–a security research company–has noticed an increase in attacks embedding malicious codes inside .gif files. The good news is that Drupal patched this vulnerability more than a year ago. The bad news is that poorly maintained sites still haven’t been updated.
The number one reason malicious attacks are successful is due to outdated software. Don’t be the guy/gal whose site is compromised by a year old update. Update your site
2. Signal Vulnerability Allows Hackers to Listen to Android Microphones
 Google Project Zero recently disclosed a vulnerability in the messaging app Signal. The vulnerability can be used when calling someone’s phone using the Signal app. During the phone call, the hacker will need to press the mute button while the target’s phone is ringing. Pressing the mute button will force the target’s device to answer the call, allowing the attacker to eavesdrop on their mark.
After being notified of the bug by Google Project Zero, Signal quickly released a patch. The exploit required the attacker to remove and modified code in the app. Thankfully, due to the difficulty, there are no reports of the exploit being used in the wild.
Google Project Zero recently disclosed a vulnerability in the messaging app Signal. The vulnerability can be used when calling someone’s phone using the Signal app. During the phone call, the hacker will need to press the mute button while the target’s phone is ringing. Pressing the mute button will force the target’s device to answer the call, allowing the attacker to eavesdrop on their mark.
After being notified of the bug by Google Project Zero, Signal quickly released a patch. The exploit required the attacker to remove and modified code in the app. Thankfully, due to the difficulty, there are no reports of the exploit being used in the wild.
October 2019, Part 1 WordPress Vulnerability Summary
- Cross-Site Scripting
- Unauthenticated Posts
- Cross-Site Scripting leading to a Javascript Injection
- JSON Cache Poisoning
- Server-Side Request Forgery
- Referrer Validation in the admin.
All In One WP Security & Firewall version 4.4.1 and below has an Open Redirect that exposes the “hidden” login page.
Popup Maker version 1.8.12 and below has a Broken Authentication vulnerability.
iThemes Sync version 2.0.17 and below has an Insufficient Secure Key Validation Vulnerability. The vulnerability could lead to a full compromise of a WordPress site, so confirm your site is running version 2.0.18
Download Plugins and Themes from Dashboard version 1.5.0 and below is vulnerable to an Unauthenticated Stored XSS attack.
wpDataTables version 2.0.7 and below is vulnerable to a Cross-Site Scripting and SQL Injection attack.
Lara’s Google Analytics 2.0.4 and below is vulnerable to an Authenticated Stored Cross-Site Scripting attack.
Export Users to CSV version 1.3 and below has an Unauthorized CSV Access vulnerability.
A WordPress Security Plugin Can Help Secure Your Website
iThemes Security Pro, our WordPress security plugin, offers 30+ ways to secure and protect your website from common WordPress security vulnerabilities. With WordPress, two-factor authentication, brute force protection, strong password enforcement, and more, you can add an extra layer of security to your website. [content_upgrade cu_id=”50951″]Learn more about WordPress security with 10 key tips. Download the ebook now: A Guide to WordPress Security[content_upgrade_button]Download now[/content_upgrade_button][/content_upgrade]Get iThemes Security
Sign up now — Get SolidWP updates and valuable content straight to your inbox
Sign up
Get started with confidence — risk free, guaranteed