WordPress Vulnerability Roundup: September 2020, Part 2
Quite a few new WordPress plugin and theme vulnerabilities were disclosed during the second half of September, making this one of our largest round-ups to date. In this post, we cover recent WordPress plugin, theme, and core vulnerabilities and what to do if you are running one of the vulnerable plugins or themes on your website.

Quite a few new WordPress plugin and theme vulnerabilities were disclosed during the second half of September, making this one of our largest round-ups to date. In this post, we cover recent WordPress plugin, theme, and core vulnerabilities and what to do if you are running one of the vulnerable plugins or themes on your website.
The WordPress Vulnerability Roundup is divided into three different categories: WordPress core, WordPress plugins, and WordPress themes.
WordPress Core Vulnerabilities
No WordPress core vulnerabilities were disclosed in the second of September. Just make sure you are running the latest version of WordPress, which is version 5.5.1.
WordPress Plugin Vulnerabilities
1. Asset CleanUp

Asset CleanUp versions below 1.3.6.7 have a Cross-Site Request Forgery and a Cross-Site Scripting vulnerabilities.
2. Sticky Menu, Sticky Header
Sticky Menu, Sticky Header versions below 2.21 have a Cross-Site Request Forgery and a Cross-Site Scripting vulnerabilities.
3. Cookiebot

Cookiebot versions below 3.6.1 have a Cross-Site Request Forgery and a Cross-Site Scripting vulnerabilities.
4. All In One WP Security & Firewall

All In One WP Security & Firewall versions below 4.4.4 have a Cross-Site Request Forgery and a Cross-Site Scripting vulnerabilities.
5. Absolutely Glamorous Custom Admin

Absolutely Glamorous Custom Admin versions below 6.5.5 have a Cross-Site Request Forgery and a Cross-Site Scripting vulnerabilities.
6. Elementor Addon Elements

Elementor Addon Elements versions below 1.6.4 have a Cross-Site Request Forgery and a Cross-Site Scripting vulnerabilities.
7. Email Subscribers & Newsletters

Email Subscribers & Newsletters versions below 4.5.6 have an Unauthenticated Email Forgery/Spoofing vulnerability.
8. 10Web Social Post Feed

10Web Social Post Feed versions below 1.1.27 have an Authenticated SQL Injection vulnerability.
9. Affiliate Manager

Affiliate Manager versions below 2.7.8 have an Unauthenticated Stored Cross-Site Scripting vulnerability.
10. WP Hotel Booking
WP Hotel Booking versions below 1.10.2 have a Cross-Site Request Forgery vulnerability.
11. WP Project Manager
WP Project Manager versions below 2.4.1 have a Cross-Site Request Forgery vulnerability.
12. 10WebAnalytics

10WebAnalytics versions below 1.2.9 have a Cross-Site Request Forgery vulnerability.
13. Top 10 – Popular posts plugin for WordPress
Top 10 – Popular posts plugin for WordPress versions below 2.9.5 have a Cross-Site Request Forgery vulnerability.
14. Lightweight Sidebar Manager
Lightweight Sidebar Manager versions below 1.1.4 have a Cross-Site Request Forgery vulnerability.
15. Radio Buttons for Taxonomies

Radio Buttons for Taxonomies versions below 2.0.6 have a Cross-Site Request Forgery vulnerability.
16. Product Catalog X

Product Catalog X versions below 1.5.13 have a Cross-Site Request Forgery vulnerability.
17. Paid Memberships Pro

Paid Memberships Pro versions below 2.4.3 have a Cross-Site Request Forgery vulnerability.
18. NotificationX
NotificationX versions below 1.8.3 have a Cross-Site Request Forgery vulnerability.
19. Coming Soon & Maintenance Mode Page

Coming Soon & Maintenance Mode Page versions below 1.58 have a Cross-Site Request Forgery vulnerability.
20. Menu Swapper
Menu Swapper versions below 1.1.1 have a Cross-Site Request Forgery vulnerability.
21. Woody ad snippets
Woody ad snippets versions below 2.3.10 have a Cross-Site Request Forgery vulnerability.
22. Forminator

Forminator versions below 1.13.5 have a Cross-Site Request Forgery vulnerability.
23. RSS Aggregator by Feedzy

RSS Aggregator by Feedzy versions below 3.4.3 have a Cross-Site Request Forgery vulnerability.
24. Feed Them Social

Feed Them Social versions below 2.8.7 have a Cross-Site Request Forgery vulnerability.
25. WP ERP

WP ERP versions below 1.6.4 have a Cross-Site Request Forgery vulnerability.
26. eCommerce Product Catalog
eCommerce Product Catalog versions below 2.9.44 have a Cross-Site Request Forgery vulnerability.
27. Easy Testimonials

Easy Testimonials versions below 3.7 have a Cross-Site Request Forgery vulnerability.
28. Dokan

Dokan versions below 3.0.9 have a Cross-Site Request Forgery vulnerability.
29. Best WooCommerce Multivendor Marketplace Solution

Best WooCommerce Multivendor Marketplace Solution versions below 3.5.8 have a Cross-Site Request Forgery vulnerability.
30. Custom Field Template
Custom Field Template versions below 2.5.2 have a Cross-Site Request Forgery vulnerability.
31. Coupon Creator

Coupon Creator versions below 3.1.1 have a Cross-Site Request Forgery vulnerability.
32. Cool Timeline

Cool Timeline versions below 2.0.3 have a Cross-Site Request Forgery vulnerability.
33. Funnel Builder by CartFlows

Funnel Builder by CartFlows versions below 1.5.16 have a Cross-Site Request Forgery vulnerability.
34. Import / Export Customizer Settings
Import / Export Customizer Settings versions below 1.0.4 have a Cross-Site Request Forgery vulnerability.
35. Discount Rules for WooCommerce

Discount Rules for WooCommerce versions below 2.2.1 have multiple Authorization Bypass vulnerabilities.
36. MetaSlider
MetaSlider versions below 3.17.2 have an Authenticated Stored Cross-Site Scripting vulnerability.
37. Drag and Drop Multiple File Upload
Drag and Drop Multiple File Upload versions below 1.3.5.5 have an Unauthenticated Remote Code Execution vulnerability.
WordPress Theme Vulnerabilities
1. JobMonster

JobMonster versions below 4.6.6.1 have a Directory Listing in Upload Folder vulnerability.
iThemes Security Pro Feature Spotlight: Trusted Devices
There are many features in iThemes Security Pro that can stop hackers from exploiting vulnerabilities in WordPress plugins and themes. Authentication Bypass and Session Hijacking are two of the most dangerous types of vulnerabilities. Both of these vulnerabilities can be exploited by hackers to bypass authentication protections and take control over your website.
Today we are going to cover Trusted Devices, a robust security method to protect your website even when it is vulnerable to bypass authentication or session hijacking attacks.
Trusted Devices is a robust security method to protect your website even when it is vulnerable to bypass authentication or session hijacking attacks.
Why We Developed Trusted Devices
Let’s say you follow all of the WordPress security best practices to protect your user account. Not only do you use a unique, strong password for every site, but you also lock down all of your online accounts with two-factor authentication. You are a good example of what it looks like to take WordPress security seriously.
Yet, even with all of the security measures you put into place, somehow, your website was still hacked. And, to make matters worse, the attacker used YOUR WordPress user to hack the site. How did this happen to you, the security guru?!
Unfortunately, even if you do everything right to secure your WordPress user account, there are still methods that hackers can use to exploit your account.
For example, WordPress generates a session cookie every time you log into your website. And let’s say that you have a browser extension that has been abandoned by the developer and is no longer releasing security updates. Unfortunately for you, the neglected browser extension has a vulnerability. The vulnerability allows bad actors to hijack your browser cookies, including the earlier-mentioned WordPress session cookie. This type of hack is known as Session Hijacking. So, an attacker can exploit the extension vulnerability to piggyback off your login and start making malicious changes with your WordPress user.
Pretty crummy, right? We agree, so we created a way to protect your account, even when bad actors can find and exploit other vulnerabilities.
What Are Trusted Devices?
The Trusted Devices feature in iThemes Security Pro works to identify the devices that you and other users use to login to your WordPress site. After your devices are identified, we can stop session hijackers and other bad actors from doing any damage on your website.
When a user has logged in on an unrecognized device, Trusted Devices can restrict their administrator-level capabilities. This means that if an attacker were able to break into the backend of your WordPress site, they wouldn’t have the ability to make any malicious changes to your website.
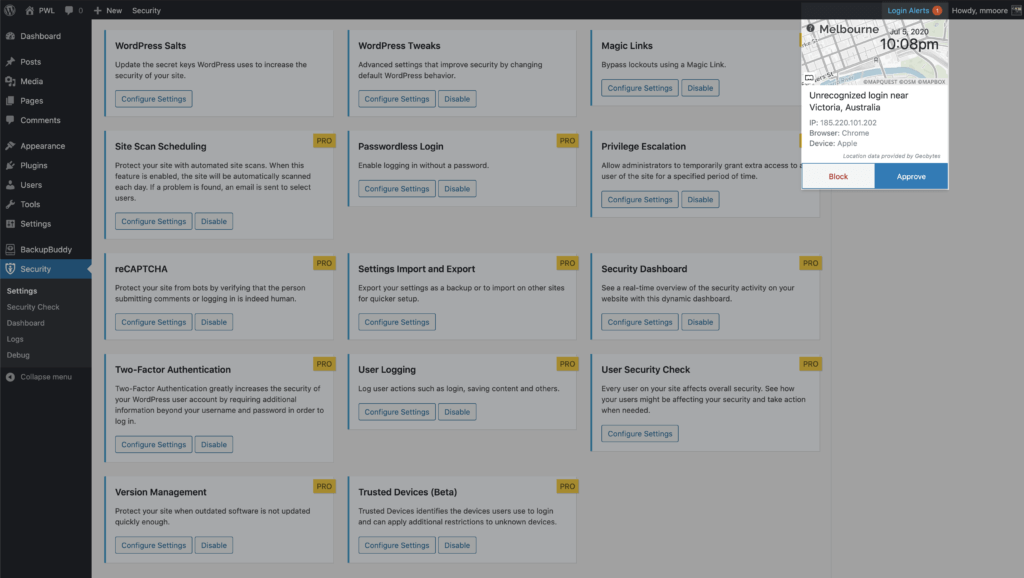
In this scenario, you will receive an email that lets you know that someone logged into your site from an unrecognized device. The email includes an option to block the hacker’s device. Then you can just laugh and laugh, knowing that you ruined a bad guy’s day.
Another benefit of Trusted Devices is that it makes Session Hijacking a thing of the past. If a user’s device changes during a session, iThemes Security will automatically log the user out to prevent any unauthorized activity on the user’s account, such as changing the user’s email address or uploading malicious plugins.
Man, it sure does feel good preventing malicious attacks from being successful!
How to Use the Trusted Devices Feature in iThemes Security Pro
To start using Trusted Devices, enable them on the main page of the security settings, and then click the Configure Settings button.
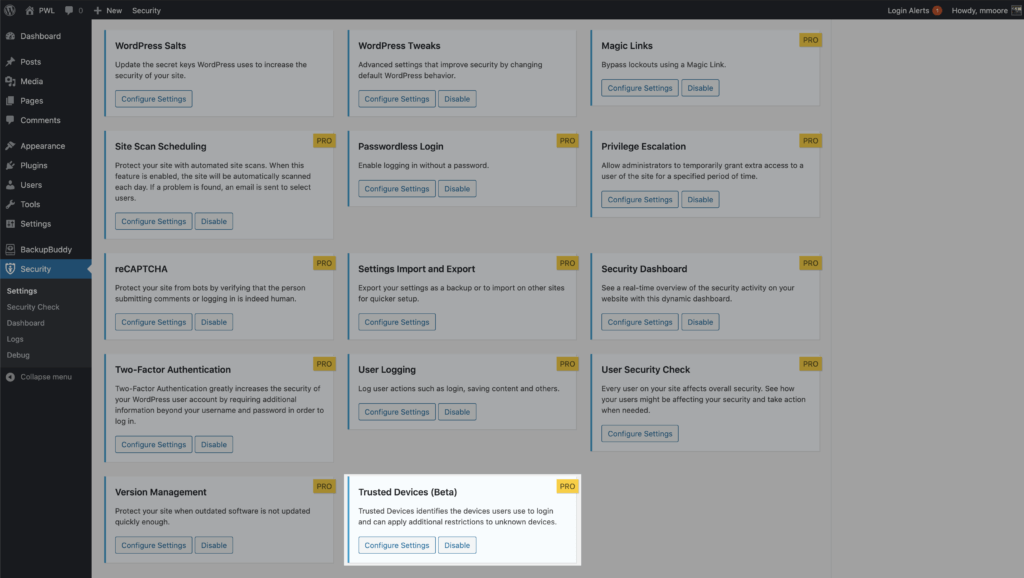
In the Trusted Devices settings, decide which users you want to use the feature, and enable then Restrict Capabilities and Session Hijacking Protection features.
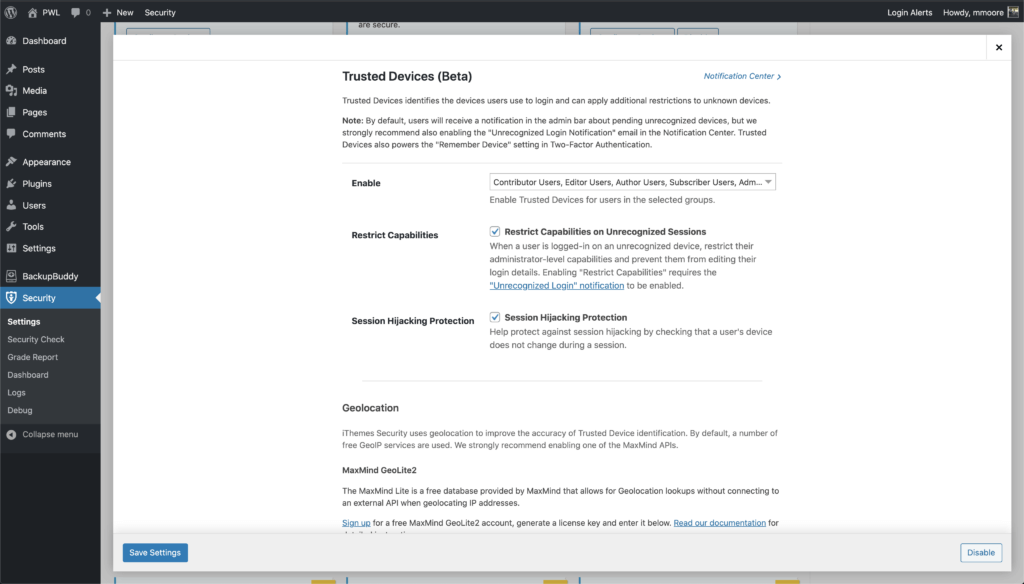
After enabling the new Trusted Devices setting, users will receive a notification in the WordPress admin bar about pending unrecognized devices. If your current device hasn’t been added to the trusted devices list, click the Confirm This Device link to send the authorization email.
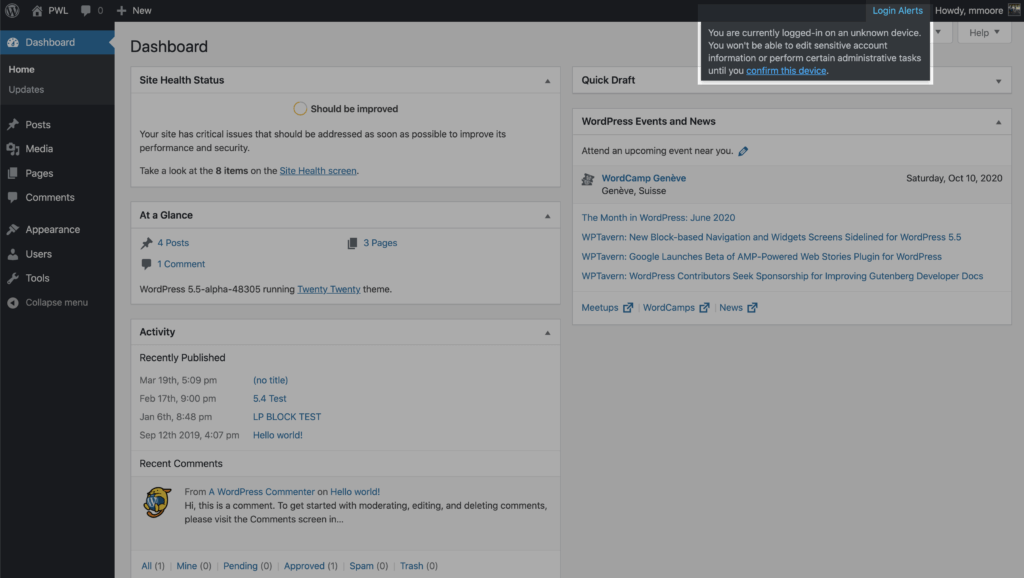
Click the Confirm Device button in the Unrecognized Login email to add your current devices to the Trusted Devices list.
Once Trusted Devices is enabled, users can manage devices from their WordPress User Profile page. From this screen, you can approve or deny devices from the Trusted Devices list.
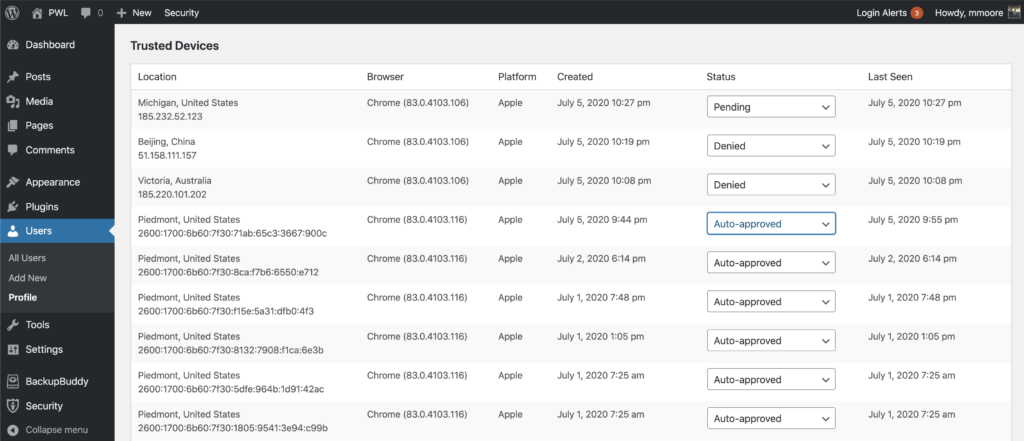
Additionally, you have the option to signup for some third-part APIs to improve the accuracy of the Trusted Devices identification and to use static image maps to display the approximate location of an unrecognized login. Check out the Trusted Devices setting to see what integrations are available,
A WordPress Security Plugin Can Help Secure Your Website
iThemes Security Pro, our WordPress security plugin, offers 50+ ways to secure and protect your website from common WordPress security vulnerabilities. With WordPress, two-factor authentication, brute force protection, strong password enforcement, and more, you can add an extra layer of security to your website.
Get iThemes Security Pro
Sign up now — Get SolidWP updates and valuable content straight to your inbox
Sign up
Get started with confidence — risk free, guaranteed