WordPress Vulnerability Roundup: July 2019, Part 1
New WordPress plugin and theme vulnerabilities were disclosed during the first half of this month, so we want to keep you aware. We divide the WordPress Vulnerability Roundup into four different categories: 1. WordPress core 2. WordPress Plugins 3. WordPress Themes 4. Breaches From Around the Web *We include breaches from around the web because it is essential to also be aware of vulnerabilities outside of the WordPress ecosystem.

New WordPress plugin and theme vulnerabilities were disclosed during the first half of this month, so we want to keep you aware.
We divide the WordPress Vulnerability Roundup into four different categories:
 Yoast SEO versions 1.2.0-11.5 and below is vulnerable to an Authenticated Stored XSS attack.
Yoast SEO versions 1.2.0-11.5 and below is vulnerable to an Authenticated Stored XSS attack.
 WooCommerce version 3.6.4 and below is vulnerable to a Cross-Site Request Forgery and File Type Check.
WooCommerce version 3.6.4 and below is vulnerable to a Cross-Site Request Forgery and File Type Check.
 Ad Inserter version 2.4.19 and below is vulnerable to an Authenticated Path Traversal attack.
Ad Inserter version 2.4.19 and below is vulnerable to an Authenticated Path Traversal attack.
 Ocean Extra plugin version 1.5.8 and below is vulnerable to an Unauthenticated Settings change and CSS injection. The exploit will allow an attacker to change some WordPress settings and inject CSS to deface the site.
Ocean Extra plugin version 1.5.8 and below is vulnerable to an Unauthenticated Settings change and CSS injection. The exploit will allow an attacker to change some WordPress settings and inject CSS to deface the site.
 WP Statistics plugin, version 12.6.6.1 and below, is vulnerable to an Unauthenticated Blind SQL Injection
WP Statistics plugin, version 12.6.6.1 and below, is vulnerable to an Unauthenticated Blind SQL Injection
 Visitors Traffic Real Time Statistics plugin 2.0.5 and below is vulnerable to a Cross-Site Request Forgery attack.
Visitors Traffic Real Time Statistics plugin 2.0.5 and below is vulnerable to a Cross-Site Request Forgery attack.
 Essential Real Estate plugin version 1.7.1 and below is vulnerable to a Cross-Site Scripting attack.
Essential Real Estate plugin version 1.7.1 and below is vulnerable to a Cross-Site Scripting attack.
 Appointment Booking Calendar version 1.3.18 and below is vulnerable to an Unauthenticated Stored XSS attack. The lack of an authorization check could lead to a Cross-Site Scripting attack.
Appointment Booking Calendar version 1.3.18 and below is vulnerable to an Unauthenticated Stored XSS attack. The lack of an authorization check could lead to a Cross-Site Scripting attack.
 Gallery PhotoBlocks version 1.1.40 and below is vulnerable to a Cross-Site Scripting attack.
Gallery PhotoBlocks version 1.1.40 and below is vulnerable to a Cross-Site Scripting attack.
 Slimstat Analytics version 4.8.3 and below is vulnerable to a Cross-Site Request Forgery and Stored XSS attack.
Slimstat Analytics version 4.8.3 and below is vulnerable to a Cross-Site Request Forgery and Stored XSS attack.
 WP Google Maps version 7.11.34 and below is vulnerable to a Cross-Site Request Forgery and Stored XSS attack.
WP Google Maps version 7.11.34 and below is vulnerable to a Cross-Site Request Forgery and Stored XSS attack.
 LiveChat version 3.7.2 and below is vulnerable to a Cross-Site Request Forgery and Stored XSS attack.
LiveChat version 3.7.2 and below is vulnerable to a Cross-Site Request Forgery and Stored XSS attack.
 Icegram version 1.10.28.2 and below is vulnerable to a Cross-Site Request Forgery and Stored XSS attack.
Icegram version 1.10.28.2 and below is vulnerable to a Cross-Site Request Forgery and Stored XSS attack.
 The WP Like Button plugin is vulnerable to an Authentication Bypass attack.
The WP Like Button plugin is vulnerable to an Authentication Bypass attack.
 File Manager version 5.0 and below has multiple vulnerabilities. As reported by WebARX, if exploited, the vulnerabilities allow any logged-in user to view, delete, or download backups. If your site has open enrollment, this means anyone can download a copy of your database and find sensitive information that could lead to further compromises.
File Manager version 5.0 and below has multiple vulnerabilities. As reported by WebARX, if exploited, the vulnerabilities allow any logged-in user to view, delete, or download backups. If your site has open enrollment, this means anyone can download a copy of your database and find sensitive information that could lead to further compromises.
 Newsletter Lite version 4.6.16 and below is vulnerable to an Authenticated Reflected XSS attack.
Newsletter Lite version 4.6.16 and below is vulnerable to an Authenticated Reflected XSS attack.
 One Click SSL version 1.4.6 and below has multiple vulnerabilities. The vulnerabilities, if exploited, could allow an unauthorized settings change and allow a low privileged user to call AJAX methods.
One Click SSL version 1.4.6 and below has multiple vulnerabilities. The vulnerabilities, if exploited, could allow an unauthorized settings change and allow a low privileged user to call AJAX methods.
 Ultimate Member version 2.0.51 and below is vulnerable to a Cross-Site Request Forgery and Stored XSS attack.
Ultimate Member version 2.0.51 and below is vulnerable to a Cross-Site Request Forgery and Stored XSS attack.
 FV Flowplayer Video Player version 7.3.18.727 and below is vulnerable to a SQL Injection.
FV Flowplayer Video Player version 7.3.18.727 and below is vulnerable to a SQL Injection.
 Zoner – Real Estate WordPress Theme version 4.1, and below is vulnerable to a Reflected XSS and Stored XSS attack.
Zoner – Real Estate WordPress Theme version 4.1, and below is vulnerable to a Reflected XSS and Stored XSS attack.
 The video conference company Zoom had a vulnerability on the macOS version of their app. The vulnerability would allow a malicious website to force a Zoom user to join a Zoom call.
Zoom wanted all users to join a meeting with a single click. This was working great until Apple decided that URLs shouldn’t open other apps without approval, and added a security measure requiring an additional approval click.
So Zoom decided to take advantage of how Apple allows app developers to create a local web server to create a server to bypass the new approval requirement.
Although Zoom initially said this was a non-issue, they listened to the feedback they were receiving and decided to patch the app and altogether remove the local web server. Apple also issued a patch removing the local web server to protect outdated versions of Zoom from the vulnerability.
The video conference company Zoom had a vulnerability on the macOS version of their app. The vulnerability would allow a malicious website to force a Zoom user to join a Zoom call.
Zoom wanted all users to join a meeting with a single click. This was working great until Apple decided that URLs shouldn’t open other apps without approval, and added a security measure requiring an additional approval click.
So Zoom decided to take advantage of how Apple allows app developers to create a local web server to create a server to bypass the new approval requirement.
Although Zoom initially said this was a non-issue, they listened to the feedback they were receiving and decided to patch the app and altogether remove the local web server. Apple also issued a patch removing the local web server to protect outdated versions of Zoom from the vulnerability.
 The Agent Smith malware gained its name by replacing portions of other Android apps code with its code. The Malware doesn’t attempt to harvest any user data. Instead, it forces the apps it hacked to show more ads and then takes credit for showing the ads to collect the revenue.
The app originated on 9Apps, a third-party app store that is popular in India. The malware author attempted to add 11 of their infested apps to the Google Play Store. But, before the apps could do any harm, they were detected and removed by Google.
The Agent Smith malware gained its name by replacing portions of other Android apps code with its code. The Malware doesn’t attempt to harvest any user data. Instead, it forces the apps it hacked to show more ads and then takes credit for showing the ads to collect the revenue.
The app originated on 9Apps, a third-party app store that is popular in India. The malware author attempted to add 11 of their infested apps to the Google Play Store. But, before the apps could do any harm, they were detected and removed by Google.
 Apple disclosed a vulnerability on the Apple Watch Walkie Talkie app. Apple disabled the app to patch the vulnerability that allows an attacker to eavesdrop on conversations. It is important to note that Apple said there is no evidence that the vulnerability has ever been exploited.
Apple disclosed a vulnerability on the Apple Watch Walkie Talkie app. Apple disabled the app to patch the vulnerability that allows an attacker to eavesdrop on conversations. It is important to note that Apple said there is no evidence that the vulnerability has ever been exploited.
- 1. WordPress core
- 2. WordPress Plugins
- 3. WordPress Themes
- 4. Breaches From Around the Web
WordPress Core Vulnerabilities
No WordPress vulnerabilities were disclosed so far in July of 2019.
WordPress Plugin Vulnerabilities
Several new WordPress plugin vulnerabilities have been discovered this July. Make sure to follow the suggested action below to update the plugin or completely uninstall it.1. Yoast SEO
 Yoast SEO versions 1.2.0-11.5 and below is vulnerable to an Authenticated Stored XSS attack.
Yoast SEO versions 1.2.0-11.5 and below is vulnerable to an Authenticated Stored XSS attack.
What You Should Do
The vulnerability has been patched, and you should update to version 11.6.
2. WooCommerce
 WooCommerce version 3.6.4 and below is vulnerable to a Cross-Site Request Forgery and File Type Check.
WooCommerce version 3.6.4 and below is vulnerable to a Cross-Site Request Forgery and File Type Check.
What You Should Do
The vulnerability has been patched, and you should update to version 3.6.5.
3. Ad Inserter
 Ad Inserter version 2.4.19 and below is vulnerable to an Authenticated Path Traversal attack.
Ad Inserter version 2.4.19 and below is vulnerable to an Authenticated Path Traversal attack.
What You Should Do
The vulnerability has been patched, and you should update to version 2.4.20.
4. Ocean Extra
 Ocean Extra plugin version 1.5.8 and below is vulnerable to an Unauthenticated Settings change and CSS injection. The exploit will allow an attacker to change some WordPress settings and inject CSS to deface the site.
Ocean Extra plugin version 1.5.8 and below is vulnerable to an Unauthenticated Settings change and CSS injection. The exploit will allow an attacker to change some WordPress settings and inject CSS to deface the site.
What You Should Do
The vulnerabilities have been patched, and you should update to version 1.5.9.
5. WP Statistics
 WP Statistics plugin, version 12.6.6.1 and below, is vulnerable to an Unauthenticated Blind SQL Injection
WP Statistics plugin, version 12.6.6.1 and below, is vulnerable to an Unauthenticated Blind SQL Injection
What You Should Do
The vulnerability has been patched, and you should update to version 12.6.7.
6. Visitors Traffic Real Time Statistics
 Visitors Traffic Real Time Statistics plugin 2.0.5 and below is vulnerable to a Cross-Site Request Forgery attack.
Visitors Traffic Real Time Statistics plugin 2.0.5 and below is vulnerable to a Cross-Site Request Forgery attack.
What You Should Do
The vulnerability has been patched, and you should update to version 1.13.
7. Essential Real Estate
 Essential Real Estate plugin version 1.7.1 and below is vulnerable to a Cross-Site Scripting attack.
Essential Real Estate plugin version 1.7.1 and below is vulnerable to a Cross-Site Scripting attack.
What You Should Do
The vulnerability has been patched, and you should update to version 1.7.2.
8. Appointment Booking Calendar
 Appointment Booking Calendar version 1.3.18 and below is vulnerable to an Unauthenticated Stored XSS attack. The lack of an authorization check could lead to a Cross-Site Scripting attack.
Appointment Booking Calendar version 1.3.18 and below is vulnerable to an Unauthenticated Stored XSS attack. The lack of an authorization check could lead to a Cross-Site Scripting attack.
What You Should Do
The vulnerability has been patched, and you should update to version 1.3.19.
9. Gallery PhotoBlocks
 Gallery PhotoBlocks version 1.1.40 and below is vulnerable to a Cross-Site Scripting attack.
Gallery PhotoBlocks version 1.1.40 and below is vulnerable to a Cross-Site Scripting attack.
What You Should Do
The vulnerability has been patched, and you should update to version 1.1.41.
10. Slimstat Analytics
 Slimstat Analytics version 4.8.3 and below is vulnerable to a Cross-Site Request Forgery and Stored XSS attack.
Slimstat Analytics version 4.8.3 and below is vulnerable to a Cross-Site Request Forgery and Stored XSS attack.
What You Should Do
The vulnerability has been patched, and you should update to version 4.8.4.
11. WP Google Maps
 WP Google Maps version 7.11.34 and below is vulnerable to a Cross-Site Request Forgery and Stored XSS attack.
WP Google Maps version 7.11.34 and below is vulnerable to a Cross-Site Request Forgery and Stored XSS attack.
What You Should Do
The vulnerability has been patched, and you should update to version 7.11.35.
12. LiveChat
 LiveChat version 3.7.2 and below is vulnerable to a Cross-Site Request Forgery and Stored XSS attack.
LiveChat version 3.7.2 and below is vulnerable to a Cross-Site Request Forgery and Stored XSS attack.
What You Should Do
The vulnerability has been patched, and you should update to version 3.7.4.
13. Icegram
 Icegram version 1.10.28.2 and below is vulnerable to a Cross-Site Request Forgery and Stored XSS attack.
Icegram version 1.10.28.2 and below is vulnerable to a Cross-Site Request Forgery and Stored XSS attack.
What You Should Do
The vulnerability has been patched, and you should update to version 1.10.29.
14. WP Like Button
 The WP Like Button plugin is vulnerable to an Authentication Bypass attack.
The WP Like Button plugin is vulnerable to an Authentication Bypass attack.
What You Should Do
WordPress.org has closed the WP Like Button plugin, so remove the plugin and find a replacement.
15. File Manager
 File Manager version 5.0 and below has multiple vulnerabilities. As reported by WebARX, if exploited, the vulnerabilities allow any logged-in user to view, delete, or download backups. If your site has open enrollment, this means anyone can download a copy of your database and find sensitive information that could lead to further compromises.
File Manager version 5.0 and below has multiple vulnerabilities. As reported by WebARX, if exploited, the vulnerabilities allow any logged-in user to view, delete, or download backups. If your site has open enrollment, this means anyone can download a copy of your database and find sensitive information that could lead to further compromises.
What You Should Do
The vulnerability has been patched, and you should update to version 5.2.
16. Newsletters
 Newsletter Lite version 4.6.16 and below is vulnerable to an Authenticated Reflected XSS attack.
Newsletter Lite version 4.6.16 and below is vulnerable to an Authenticated Reflected XSS attack.
What You Should Do
The vulnerability has been patched, and you should update to version 4.6.18.
17. One Click SSL
 One Click SSL version 1.4.6 and below has multiple vulnerabilities. The vulnerabilities, if exploited, could allow an unauthorized settings change and allow a low privileged user to call AJAX methods.
One Click SSL version 1.4.6 and below has multiple vulnerabilities. The vulnerabilities, if exploited, could allow an unauthorized settings change and allow a low privileged user to call AJAX methods.
What You Should Do
The vulnerability has been patched, and you should update to version 1.4.7.
18. Ultimate Member
 Ultimate Member version 2.0.51 and below is vulnerable to a Cross-Site Request Forgery and Stored XSS attack.
Ultimate Member version 2.0.51 and below is vulnerable to a Cross-Site Request Forgery and Stored XSS attack.
What You Should Do
The vulnerability has been patched, and you should update to version 2.0.52.
19. FV Flowplayer Video Player
 FV Flowplayer Video Player version 7.3.18.727 and below is vulnerable to a SQL Injection.
FV Flowplayer Video Player version 7.3.18.727 and below is vulnerable to a SQL Injection.
What You Should Do
The vulnerability has been patched, and you should update to version 7.3.19.727.
WordPress Themes
20. Zoner – Real Estate WordPress Theme
 Zoner – Real Estate WordPress Theme version 4.1, and below is vulnerable to a Reflected XSS and Stored XSS attack.
Zoner – Real Estate WordPress Theme version 4.1, and below is vulnerable to a Reflected XSS and Stored XSS attack.
What You Should Do
The vulnerability has been patched, and you should update to version 4.2.
How to Be Proactive About WordPress Theme & Plugin Vulnerabilities
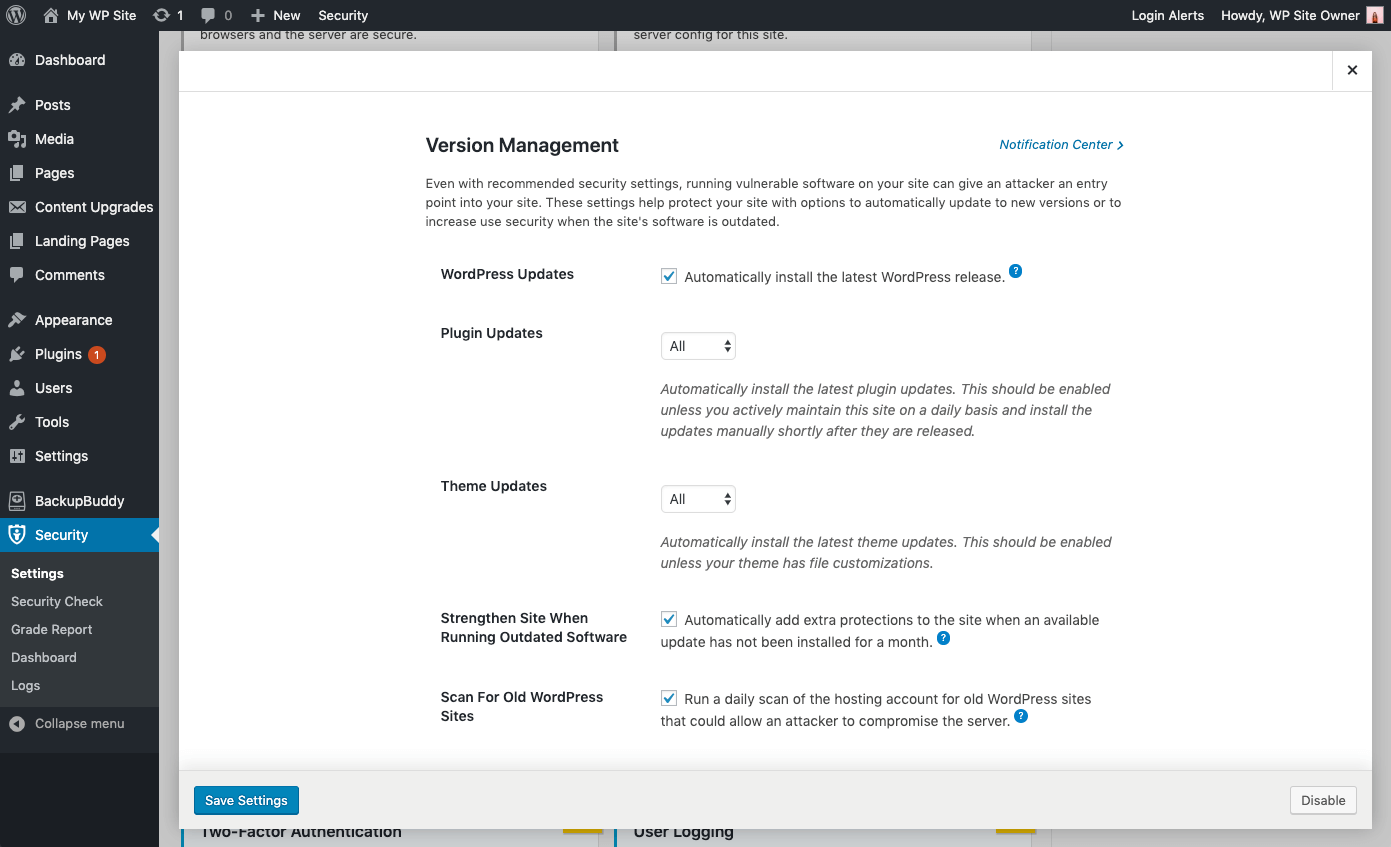
Running outdated software is the number one reason WordPress sites are hacked. It is crucial to the security of your WordPress site that you have an update routine. You should be logging into your sites at least once a week to perform updates.Automatic Updates Can Help
Automatic updates are a great choice for WordPress websites that don’t change very often. Lack of attention often leaves these sites neglected and vulnerable to attacks. Even with recommended security settings, running vulnerable software on your site can give an attacker an entry point into your site. Using the iThemes Security Pro plugin’s Version Management feature, you can enable automatic WordPress updates to ensure you are getting the latest security patches. These settings help protect your site with options to automatically update to new versions or to increase user security when the site’s software is outdated.
Version Management Update Options
- WordPress Updates –Automatically install the latest WordPress release.
- Plugin Automatic Updates – Automatically install the latest plugin updates. This should be enabled unless you actively maintain this site on a daily basis and install the updates manually shortly after they are released.
- Theme Automatic Updates – Automatically install the latest theme updates. This should be enabled unless your theme has file customizations.
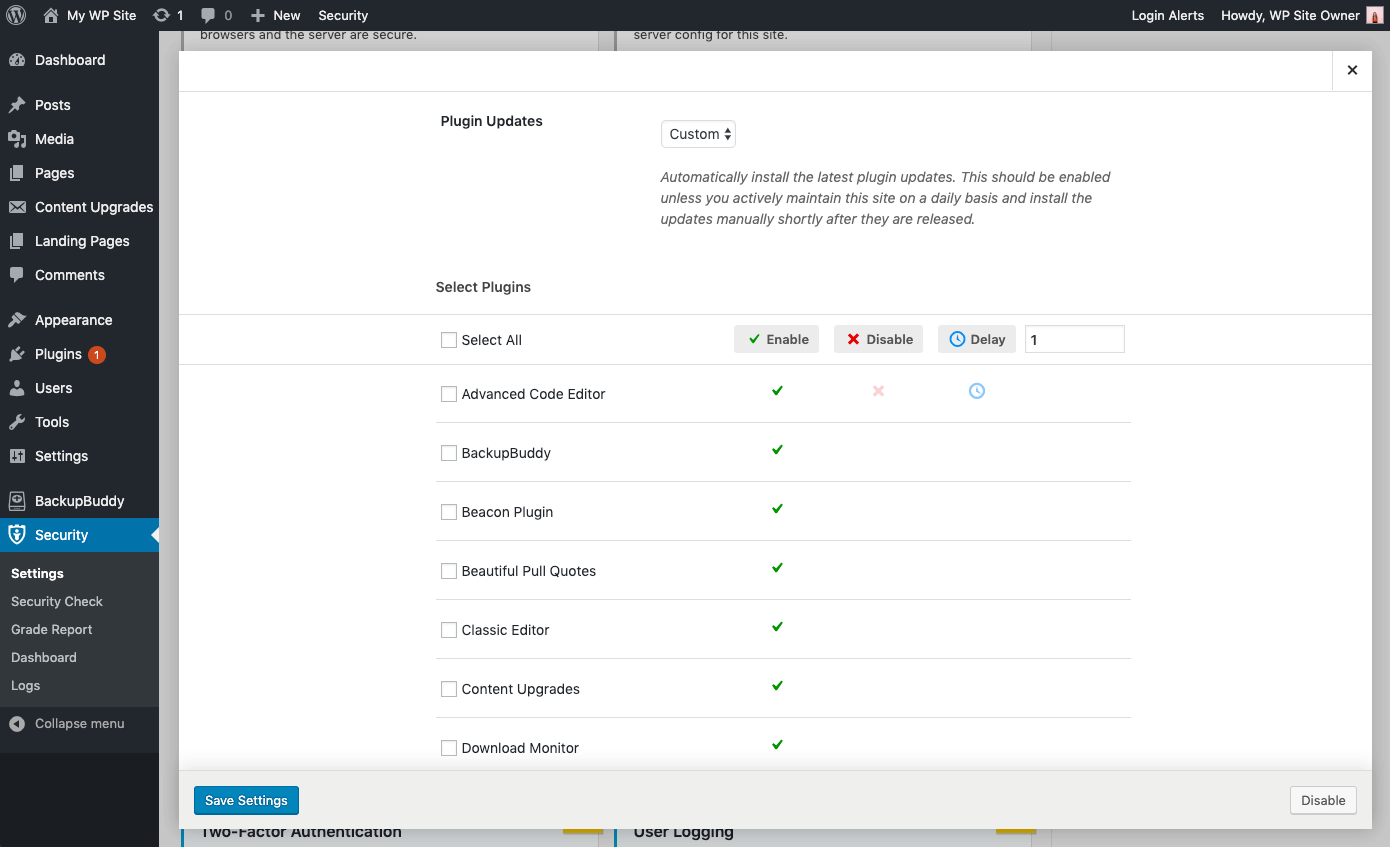
- Granular Control over Plugin and Theme updates – You may have plugins/themes that you’d like to either manually update, or delay the update until the release has had time to prove stable. You can choose Custom for the opportunity to assign each plugin or theme to either update immediately (Enable), not update automatically at all (Disable) or update with a delay of a specified amount of days (Delay).

Strengthening and Alerting to Critical Issues
- Strengthen Site When Running Outdated Software – Automatically add extra protections to the site when an available update has not been installed for a month. The iThemes Security plugin will automatically enable stricter security when an update has not been installed for a month. First, it will force all users that do not have two-factor enabled to provide a login code sent to their email address before logging back in. Second, it will disable the WP File Editor (to block people from editing plugin or theme code), XML-RPC pingbacks and block multiple authentication attempts per XML-RPC request (both of which will make XML-RPC stronger against attacks without having to turn it off completely).
- Scan for Other Old WordPress Sites – This will checks for other outdated WordPress installs on your hosting account. A single outdated WordPress site with a vulnerability could allow attackers to compromise all the other sites on the same hosting account.
- Send Email Notifications – For issues that require intervention, an email is sent to admin-level users.
Breaches From Around the Web
1. Zoom
 The video conference company Zoom had a vulnerability on the macOS version of their app. The vulnerability would allow a malicious website to force a Zoom user to join a Zoom call.
Zoom wanted all users to join a meeting with a single click. This was working great until Apple decided that URLs shouldn’t open other apps without approval, and added a security measure requiring an additional approval click.
So Zoom decided to take advantage of how Apple allows app developers to create a local web server to create a server to bypass the new approval requirement.
Although Zoom initially said this was a non-issue, they listened to the feedback they were receiving and decided to patch the app and altogether remove the local web server. Apple also issued a patch removing the local web server to protect outdated versions of Zoom from the vulnerability.
The video conference company Zoom had a vulnerability on the macOS version of their app. The vulnerability would allow a malicious website to force a Zoom user to join a Zoom call.
Zoom wanted all users to join a meeting with a single click. This was working great until Apple decided that URLs shouldn’t open other apps without approval, and added a security measure requiring an additional approval click.
So Zoom decided to take advantage of how Apple allows app developers to create a local web server to create a server to bypass the new approval requirement.
Although Zoom initially said this was a non-issue, they listened to the feedback they were receiving and decided to patch the app and altogether remove the local web server. Apple also issued a patch removing the local web server to protect outdated versions of Zoom from the vulnerability.
2. Agent Smith Android Malware
 The Agent Smith malware gained its name by replacing portions of other Android apps code with its code. The Malware doesn’t attempt to harvest any user data. Instead, it forces the apps it hacked to show more ads and then takes credit for showing the ads to collect the revenue.
The app originated on 9Apps, a third-party app store that is popular in India. The malware author attempted to add 11 of their infested apps to the Google Play Store. But, before the apps could do any harm, they were detected and removed by Google.
The Agent Smith malware gained its name by replacing portions of other Android apps code with its code. The Malware doesn’t attempt to harvest any user data. Instead, it forces the apps it hacked to show more ads and then takes credit for showing the ads to collect the revenue.
The app originated on 9Apps, a third-party app store that is popular in India. The malware author attempted to add 11 of their infested apps to the Google Play Store. But, before the apps could do any harm, they were detected and removed by Google.
3. Apple disables Walkie Talkie on the Apple Watch
 Apple disclosed a vulnerability on the Apple Watch Walkie Talkie app. Apple disabled the app to patch the vulnerability that allows an attacker to eavesdrop on conversations. It is important to note that Apple said there is no evidence that the vulnerability has ever been exploited.
Apple disclosed a vulnerability on the Apple Watch Walkie Talkie app. Apple disabled the app to patch the vulnerability that allows an attacker to eavesdrop on conversations. It is important to note that Apple said there is no evidence that the vulnerability has ever been exploited.
A WordPress Security Plugin Can Help Secure Your Website
iThemes Security Pro, our WordPress security plugin, offers 30+ ways to secure and protect your website from common WordPress security vulnerabilities. With WordPress two-factor authentication, brute force protection, strong password enforcement, and more, you can add an extra layer of security to your website. [content_upgrade cu_id=”50548″]Learn more about all of iThemes Security’s WordPress security features. Download the new ebook: iThemes Security Setup Guide[content_upgrade_button]Download now[/content_upgrade_button][/content_upgrade]Get iThemes Security Pro
Sign up now — Get SolidWP updates and valuable content straight to your inbox
Sign up
Placeholder text
Placeholder text
Get started with confidence — risk free, guaranteed