GoDaddy Hacked: 5 Ways to Secure Your WordPress Site
UPDATED New details have emerged following our original post. The breach that affected up to 1.2 million hosting customers at GoDaddy was found to also affect six other hosting providers also owned by GoDaddy. These include 123Reg, Domain Factory, Heart Internet, Host Europe, Media Temple, tsoHost.

UPDATED
New details have emerged following our original post. The breach that affected up to 1.2 million hosting customers at GoDaddy was found to also affect six other hosting providers also owned by GoDaddy. These include 123Reg, Domain Factory, Heart Internet, Host Europe, Media Temple, tsoHost. In the California disclosure notification, GoDaddy provided specific dates for the intrusions, September 6-11, 2021 and on November 7, 2021. Recommendations here are applicable for customers of those hosting companies as well.
In a security disclosure published today, GoDaddy says that up to 1.2 million active and inactive customers have been exposed after hackers gained access to its managed WordPress hosting platform. The hack was first discovered by GoDaddy on November 17, 2021.
In this post, we’ll unpack a few of the details of the recent GoDaddy hack, how it affects customers, and our recommendations for what to do if you’re a WordPress hosting customer at GoDaddy.
GoDaddy’s Security Incident Disclosure on November 22, 2021
In the public security incident disclosure released today, Demetrius Comes, GoDaddy Chief Information Security Officer, explained the details of the GoDaddy hack:
“Using a compromised password, an unauthorized third party accessed the provisioning system in our legacy code base for Managed WordPress,” he explains. “Our investigation is ongoing and we are contacting all impacted customers directly with specific details.”
According to the disclosure, GoDaddy determined that beginning on September 6, 2021, the “unauthorized third party” used a compromised password to gain access to the following customer information:
- Up to 1.2 million active and inactive Managed WordPress customers had their email address and customer number exposed. The exposure of email addresses presents risk of phishing attacks.
- The original WordPress Admin password that was set at the time of provisioning was exposed. If those credentials were still in use, GoDaddy reset those passwords.
- For active customers, sFTP and database usernames and passwords were exposed. GoDaddy reset both passwords.
- For a subset of active customers, the SSL private key was exposed. GoDaddy is in the process of issuing and installing new certificates for those customers.
Am I Affected by the GoDaddy Hack?
According to the disclosure, the hack impacts both current and past customers of GoDaddy’s managed WordPress hosting platform. This includes WordPress hosting plans from Basic, Delux, Ultimate, to Ecommerce. The disclosure does not indicate if other hosting plans were impacted.
What Should I Do If I’m Affected?
If you use GoDaddy to host your WordPress site, we have a few (strong) recommendations:
1. Reset your WordPress admin password.
As a precaution, reset your WordPress password. You can do so from the WordPress login screen located at [yourURL]/wp-admin. Change your password to something that’s strong, unique, and complex. See our WordPress password security tips here.
2. Implement two-factor authentication for WordPress admin accounts.
Using the iThemes Security plugin, activate WordPress two-factor authentication for all your admin-level accounts. Two-factor authentication is a process of verifying a person’s identity by requiring two separate methods of verification.
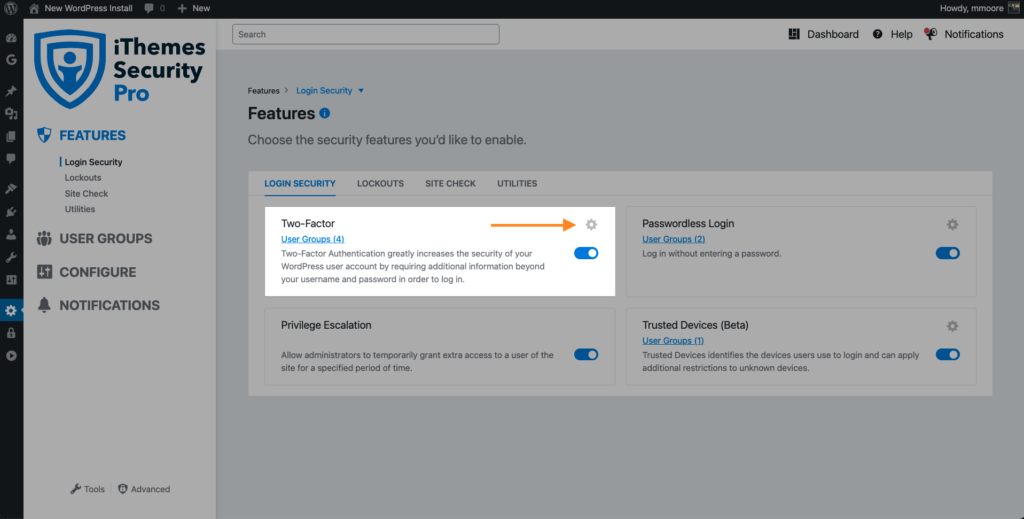
Two-factor is a FREE feature in the iThemes Security plugin, so download iThemes Security and install it on your WordPress site.
Download iThemes Security
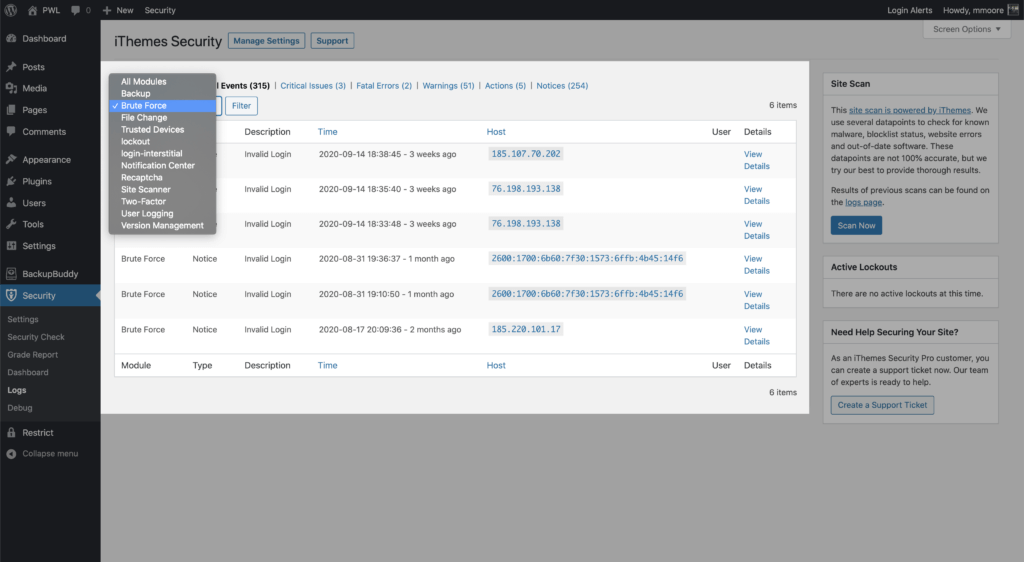
3. Review your website’s security logs to see if there are unexpected logins to admin accounts.
Website security logging is an essential part of your WordPress security strategy. Insufficient logging and monitoring can lead to a delay in the detection of a security breach.
WordPress security logs have several benefits in your overall security strategy:
1. Identify and stop malicious behavior. Every day, lots of activity is happening on your site that you may not be aware of. Many of these activities can be directly related to the security of your site. That’s why logging is so important: activities are tracked so that you can know if a hack or breach has occurred.
2. Spot activity that can alert you of a breach. Activities like unrecognized file changes or suspicious user activity may indicate a hack. That’s what it’s so important to know when these activities have occurred so you can quickly know if a breach has happened.
3. Assess how much damage was done. With WordPress security logs, you can see file changes and user activity that may be related to a hack or breach. Logs give you a sort of trail that can help undo any damage done by a hacker to insert malicious scripts or make other file changes on your website.
4. Aide in the repair of a hacked site. If your site does get hacked, you will want to have the best information to aide in a quick investigation and recovery. WordPress security logs can guide you through the timeline of a hack and show everything the hacker changed, from adding new users to adding unwanted pharma ads on your site.
iThemes Security Pro’s WordPress security logs make it easy to track user activity, such as logins, user creation/registration, adding/removing plugins, and changes to posts/pages.
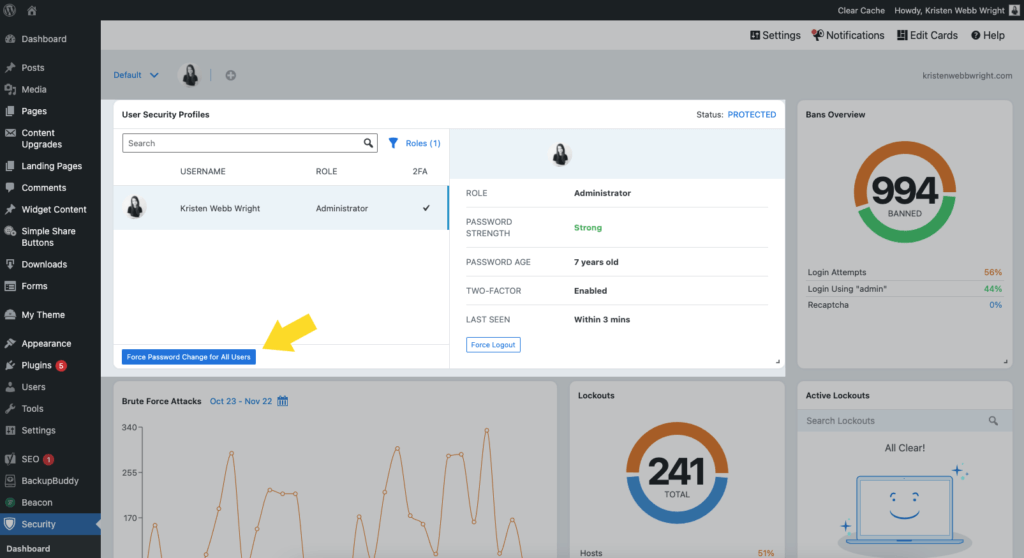
4. Force a password change from your WordPress security dashboard.
From the iThemes Security Pro dashboard, you can force a password change for all users. This will require users to change their password out of an abundance of caution.
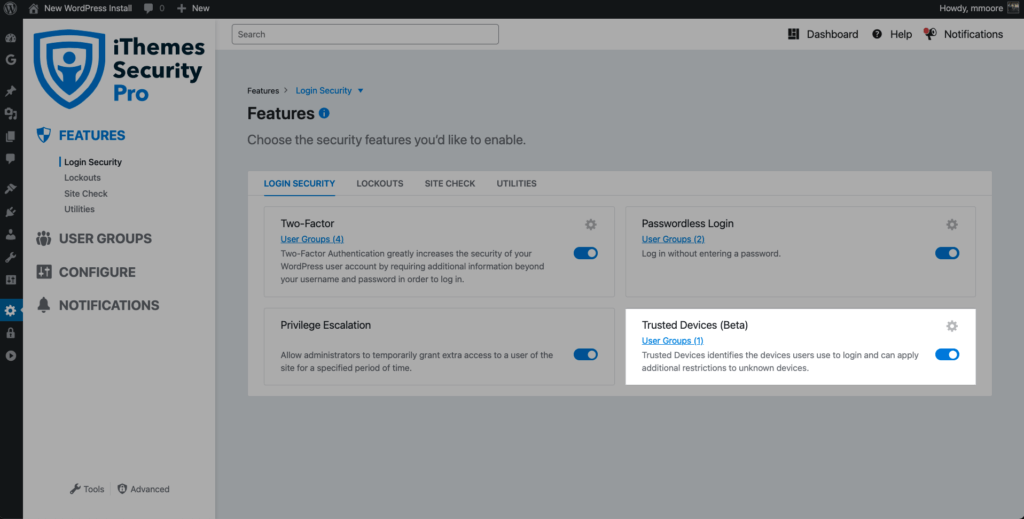
5. Enable Trusted Devices with Session Hijacking Protection.
The Trusted Devices feature in the iThemes Security Pro plugin works to identify the devices that you and other users use to login to your WordPress site. After your devices are identified, we can stop session hijackers and other bad actors from doing any damage on your website.
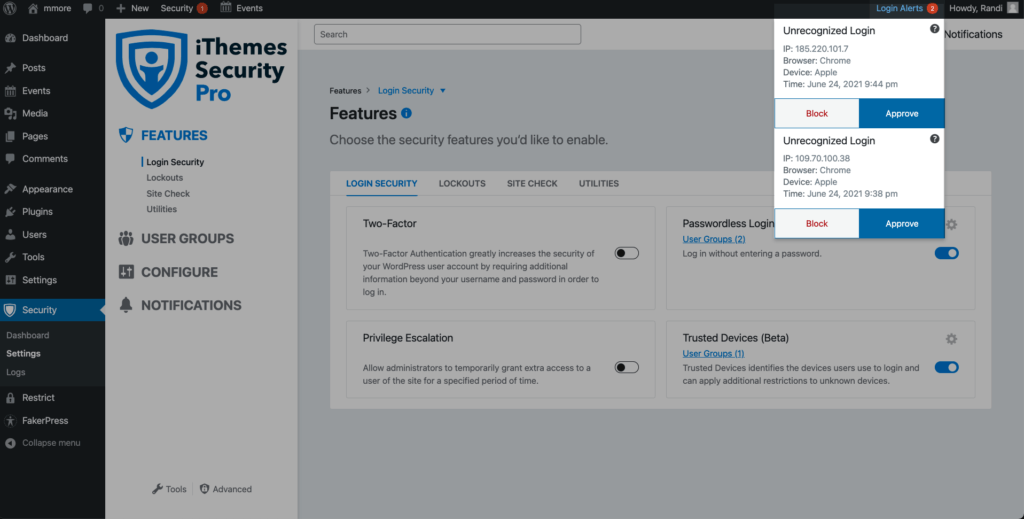
When a user has logged in on an unrecognized device, Trusted Devices can restrict their administrator-level capabilities. This means that if an attacker were able to break into the backend of your WordPress site, they wouldn’t have the ability to make any malicious changes to your website.
iThemes Security Pro will also send you an email that lets you know that someone logged into your site from an unrecognized device. The email includes an option to block the hacker’s device.
Then you’ll be able to see when unrecognized logins occur on your site from devices that weren’t approved.
Be on Guard for an Increase in Phishing Emails
As indicated by the security disclosure, the leak of GoDaddy customer email addresses could pose a phishing risk. Be on the lookout for suspicious emails from GoDaddy.
Phishing is a cyber-attack method using email, social media, text messages, and phone calls to trick the victim into giving up personal information. The attacker will then use the information to access personal accounts or commit identity fraud.
4 Tips to Spot a Phishing Email
- Look at the from email address – If you receive an email from a business like GoDaddy, the portion of the sender’s email address after the “@” should match the business name. If an email represents a company or government entity but is using a public email address like “@gmail,” this is likely a sign of a phishing email. Keep an eye out for subtle misspellings of the domain name. For example, let’s look at this email address “[email protected].” We can see that Netflix has an extra “x” at the end. The misspelling is a clear sign that the email was sent by a scammer and should be deleted immediately.
- Look for grammatical errors – An email full of grammatical mistakes is a sign of a malicious email. All of the words may be spelled correctly, but sentences are missing words that would make the sentence coherent. For example, “Your account is been hacked. Update password to account security”. Everyone makes mistakes, and not every email with a typo or two is an attempt to scam you. However, multiple grammatical errors warrant a closer look before responding.
- Look for Suspicious attachments or links – It is worth pausing for a moment before interacting with any attachments or links included in an email. If you don’t recognize the sender of an email, you shouldn’t download any attachments included in the email as it could contain malware and infect your computer. If the email claims to be from a business, you can Google their contact information to verify the email was sent from them before opening any attachments. If an email contains a link, you can hover your mouse over the link to verify the URL is sending you where it should be.
- Watch out for urgent requests – A common trick used by scammers is to create a sense of urgency. A malicious email might manufacture a scenario that needs immediate action. The more time you have time to think, the greater the chance you will identify the request is coming from a scammer. Common phishing examples include that urgent email from your “boss” asking you to pay a vendor ASAP or from your bank informing you that your account has been hacked and immediate action is required.
Wrapping Up: To a Safer Web, Together
Using a few WordPress security best practices, you can defend your site from compromised passwords and vulnerabilities. As the threat of hacks and breaches are on the rise for WordPress sites, the iThemes Security Pro plugin was designed to help you rest a little easier each night.
Get iThemes Security Pro with 24/7 Website Security Monitoring
iThemes Security Pro, our WordPress security plugin, offers 50+ ways to secure and protect your website from common WordPress security vulnerabilities. With WordPress, two-factor authentication, brute force protection, strong password enforcement, and more, you can add extra layers of security to your website.
Get iThemes Security Pro
Sign up now — Get SolidWP updates and valuable content straight to your inbox
Sign up
Get started with confidence — risk free, guaranteed