SQL Injection: A Guide for WordPress Users
If you’re serious about your website’s security, then it’s time to learn about the dangers of SQL injections and how you can combat them. In this guide, we’ll explain in detail what an SQL injection attack looks like, and the exact steps you need to take to avoid one. Let’s take a look.

If you’re serious about your website’s security, then it’s time to learn about the dangers of SQL injections and how you can combat them.
In this guide, we’ll explain in detail what an SQL injection attack looks like, and the exact steps you need to take to avoid one. Let’s take a look. You’ll learn all about how these attacks work, why they’re so important to defend against, and real-world examples of these vulnerabilities. Let’s dive in!
Introduction: What is SQL?
Structured Query Language, or “SQL” (pronounced like the word “sequel”) is a Relational Database Management System. Invented in 1974, it was the first easy way to store and retrieve many types of data on computer systems.
Since then, the language has skyrocketed in popularity and is still used in many content management systems (CMS) like WordPress today. Shortly after the language became popular in the scientific research community, the issue of the now-infamous SQL injection arose.
In systems like WordPress, many operations use SQL queries to retrieve and store data. These SQL queries are written by developers and are not designed to be malleable.
Unfortunately, since the inception of SQL, SQL injection attacks have been a persistent issue for systems that use this type of database, like the WordPress database. Using a quality WordPress security plugin can certainly help mitigate the risk of suffering a devastating attack or breach. However, as G.I. Joe would say, “knowing is half the battle” when it comes to any form of cyber attack.

What is an SQL Injection (SQLi)?
[pullquote]In a nutshell, an SQL injection (SQLi) is an attack that allows a hacker to take advantage of a vulnerable SQL query to run their own query. SQL injections occur when an attacker is able to run their own SQL on a server.[/pullquote]
You’ll notice that SQL injections are often referred to as “SQLI” or “SQLi” in technical publications. Remember, these attacks can happen on any system that uses SQL or a derivative of SQL to manage data. WordPress SQL injections in particular are just so well-researched and documented due to the sheer volume of sites that run on the WordPress platform.
Let’s take a look at the more technical outlay of what these attacks consist of.
SQL Injection Definition
By definition, the intent of an SQL injection is always malicious, and it typically aims to accomplish one or more of these three goals:
- Unauthorized Data Retrieval – In SQL, the SELECT command is used to grab data. If an attacker can successfully manipulate a SELECT-based query, they’ll be able to “dump” the contents of a database. This is why it’s critical to encrypt all databases with information that shouldn’t be made publicly known.
- Modification of Data – In other cases, the goal of a WordPress SQL injection may be to change entries in databases. This is commonly to assign a particular account or set of accounts permissions they wouldn’t ordinarily have.
- Denial of Service (DoS) – A DoS attack is when a malicious user makes it more difficult for legitimate users to access your site or services. A common command in SQL to delete data is simply DELETE. Attackers often mass-delete the contents of databases to make target sites unreachable or unusable.
Quick Tip: Back Up Your Website Regularly!
Many seasoned developers keep off-server copies of all the SQL they’ve written for their WordPress sites. In the form of .sql files, these can be used in conjunction with a WordPress backup plugin to ensure that even if an attacker can thwart your security, you can recover in very little time. A WordPress backup plugin like BackupBuddy backs up your entire WordPress database and any other files in your WordPress installation.
SQL Injection Attack Types Explained
Now that we’ve explored some of the damage SQL-based attacks can cause, it’s time to explore the more technical side of injections. There are a few important subsets of injection types you should know.
Classic SQL Injection (SQLi)
The most common type of injection, the classic version is when the attacker knows the SQL code in advance. This also happens to be the type of injection most used on WordPress; since WordPress is open source, the general public has access to all of its components, including its SQL queries.
We’ll jump into actual examples a bit later on, but with this form of injection, attackers often manipulate queries to “cancel out” the first part of one. They can then insert a custom query that the server will run as though the original developer wrote it.
Blind SQL Injection (SQLi)
Unlike the classic version, blind SQL injections occur when the attacker doesn’t have access to SQL code and simply has to make an educated guess. Additionally, this type requires far more skill than traditional SQLi, since the results of a successful attack are not displayed to the attacker.
That being said, there are many programs available that assist malicious users in grabbing their results bit-by-bit automatically.
Compounded SLQ Injection (SQLi)
This form of attack is when a separate attack is combined with SQLi to get the desired result. The most sophisticated out of the three subgroups, the attacker must execute an exploit that allows them to execute SQLi that wouldn’t work on its own. The exploits that most commonly accompany SQLi in this genre of attack are authentication breaches, Distributed Denial of Service (DDoS) attacks, DNS hijacking, and cross-site scripting attacks.
Why are WordPress Websites Vulnerable to SQL Injections?
WordPress is vulnerable to certain SQL injections since it’s so widely used (now powring 40% of all websites!) and has been around for awhile (since 2003). In our 2021 WordPress vulnerability report, 9.3% of vulnerabilities were SQL injections. WordPress is based on PHP, a server-side programming language that is designed to integrate easily with MySQL.
WordPress uses SQL databases to store pretty much everything, from comments to posts to accounts to ecommerce information. [pullquote]The vast majority of WordPress SQL injection attempts are on forms that submit data to a PHP script containing the SQL query that the attacker wishes to exploit.[/pullquote]
This is not a design flaw, but rather a side effect of the way WordPress was designed. Remember, pretty much everything that started before and up to the “dot com era” wasn’t designed with security in mind. As a matter of fact, the now-discontinued Phrack web magazine was the first public source to discuss SQLi in its December 1998 issue.
Though the initial SQLi exploits almost never work on a modern CMS like WordPress, attackers have gotten crafty over the years. We’ll take a look at a simple example of what SQLi could look like on a completely unprotected website. Then, we’ll show you how to look at existing exploits for various versions of WordPress.
Important Warnings Regarding SQL Injections
Before we continue, there is one more important note we want to make quite clear to help you stay on track with your joint WordPress and cybersecurity journey!
Keeping your version of WordPress updated is one of the best defenses against SQLi exploits. Even if it means temporarily breaking a few plugins, it’s worth it for your site security.
SQL Injection Example
Now that we’ve gotten those disclaimers out of the way, let’s look at SQLi examples. In order to understand these, you’ll need to know a bit of SQL jargon. SQL uses commands like SELECT to grab data, DROP TABLE to completely destroy a table within a database, DELETE to remove rows from a table, and more. Additionally, the ‘*’ character means “all” in SQL.
The most basic query in SQL is: SELECT * FROM TABLE_NAME. This says to essentially print out all data from a table named “TABLE_NAME”. When you submit data into a login form, that’s run through a PHP script that matches your credentials with a table of users. In our example, we’ll assume that we’re very bad at cyber security and have a completely unencrypted, cleartext table with columns called USER and PASS.
Preparing the Query
In our very badly-secured database, our table with usernames and passwords is called BADLY_DONE_TABLE. The query to authenticate a user logging in is simply: SELECT * FROM BADLY_DONE_TABLE WHERE USER = ‘[username from form]’ AND PASS = ‘[password from form]’.
As you can see, we are saying to grab the “list” of users, which should only be one, if the username and password that are entered into the form match. SQL also allows the keyword OR to be used in conditional statements, like the AND you see in our query.
Now, it’s time to craft our exploit.
Exploiting Our Unprotected SQL Query
Our query is set up to return the user if our username and password match. Keeping in mind that a single quote will end a string, we can type “Blahblahblah” as our username and then ‘OR ‘1’=’1.
We’re taking advantage of the fact that our query is dynamically formed and input is not “sanitized” before it’s executed. Essentially, we’re saying that if the number ‘1’ equals the number ‘1’ (surprisingly, it does!), then dump everything from the table, regardless of whether the credentials we entered are correct.
In 1998, this would have worked. Now, it generally takes far more skill in both SQL and SQLi to craft working exploits for WordPress.
SQL Injections and WordPress Websites
Our previous example wouldn’t work on modern WordPress sites unless a site administrator went out of their way to disable any and all security measures. However, using the same principles, hackers still create and sell SQLi exploits to other malicious users.
Because WordPress is open source and has a large development community behind it, many security researchers often find these exploits before a hacker does. They then report them to the WordPress team, and the exploit gets patched. In some unfortunate cases, a hacker locates the exploit first, making it “in the wild,” forcing the WordPress team to make a quick fix as soon as possible and release it as an update.
If you’re interested in seeing current and previous injection exploits for WordPress, you can check out a CVE database. This contains an index of security threats with the product name, versions affected, and a general description of how the exploit works. Pretty much all exploits you’ll find on lists like these are already patched, but they’re great to use as learning materials.
Get SolidWP tips direct in your inbox
Sign up
Get started with confidence — risk free, guaranteed
SQL Injection Prevention
After reading this, you’re probably wondering how to ensure that your WordPress site doesn’t become the next victim of an SQLi attack. The good news is that you don’t need to be a security professional to protect yourself from SQLi attacks!
- Be very careful about any PHP files you write or get from other sites and install (specifically, WordPress plugins). All it takes is a weakly-made PHP script that doesn’t sanitize user input to ruin your WordPress site.
- Use well-known security monitoring plugin like iThemes Security Pro to alert you in case someone is attempting to commit this attack against your site so you can block it beforehand.
- Most importantly, you should always keep your WordPress site updated to the latest version. Many site owners hold off on updating for one reason or another, and this is the reason for the vast majority of data breaches.
- Keep your WordPress plugins and themes updated. We can’t say it enough. Vulnerable themes and plugins are the #1 reason WordPress sites get hacked.
5 Steps to Prevent WordPress SQL Injections
1. Download and Install the iThemes Security Pro Plugin
To get started securing and protecting your site, download and install the iThemes Security Pro plugin.
2. Activate Version Management to Keep WordPress Core, Plugins and Themes Updated
Simply put: You’re putting yourself at risk for an attack if you are running outdated versions of WordPress, plugins and themes on your website. Version updates often include patches for security issues in the code, including SQL injections and remote code execution (RCE) vulnerabilities, so it’s important to always run the latest version of all software installed on your WordPress website.
Updates will appear in your WordPress dashboard as soon as they’re available. Make a practice of running a backup and then running all available updates every time you login to your WordPress site. While the task of running updates may seem inconvenient or tiresome, it’s an important WordPress security best practice.
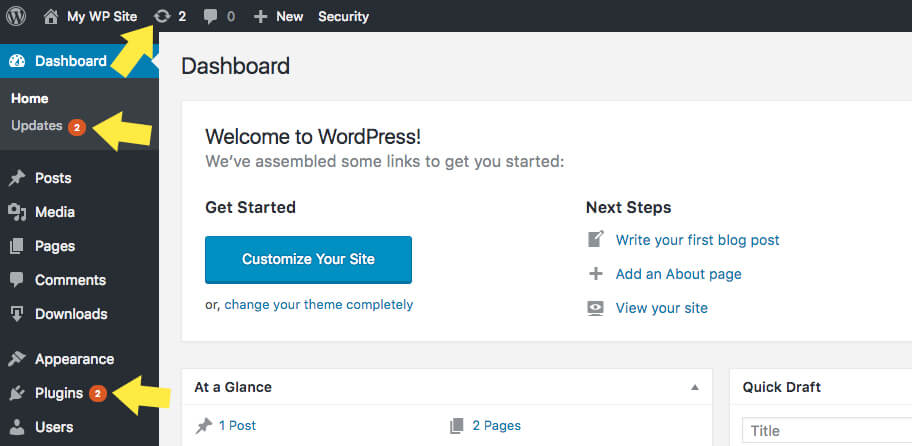
It is hard to keep track of every disclosed WordPress vulnerability—we keep track and share them in our WordPress Vulnerability Roundups—and compare that list to the versions of plugins and themes you have installed on your website. However, this doesn’t stop WordPress hackers from targeting plugins and themes with known vulnerabilities. Having software with known vulnerabilities installed on your site gives hackers the blueprints they need to take over your website.
The Version Management feature in the iThemes Security Pro plugin allows you to auto-update WordPress, plugins, and themes. Beyond that, Version Management also has options to harden your website when you are running outdated software and scan for old websites.
To get started using Version Management, enable the module on the main page of the security settings.
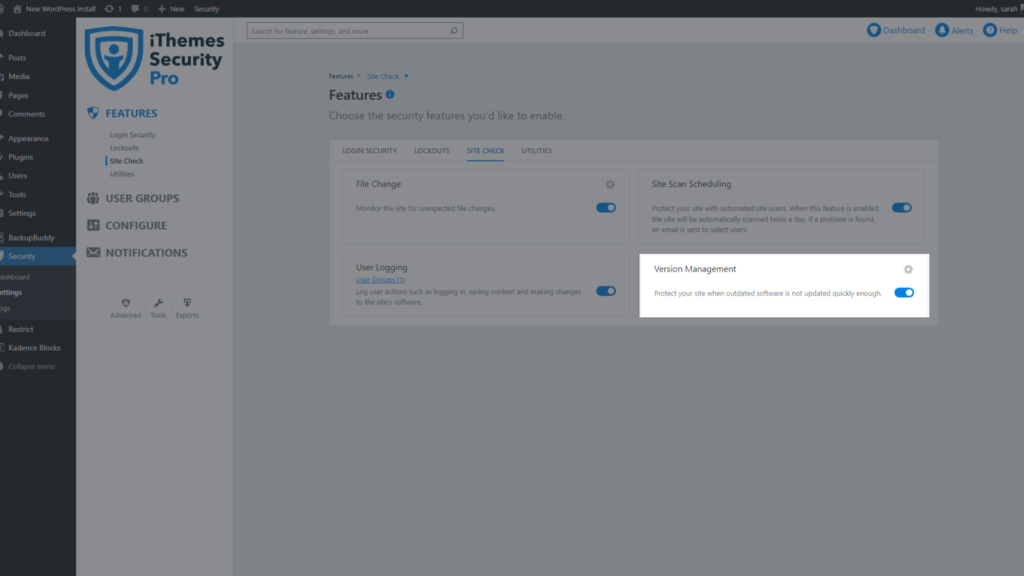
Now click the Configure Settings button to take a closer look at the settings, all designed to protect your site.
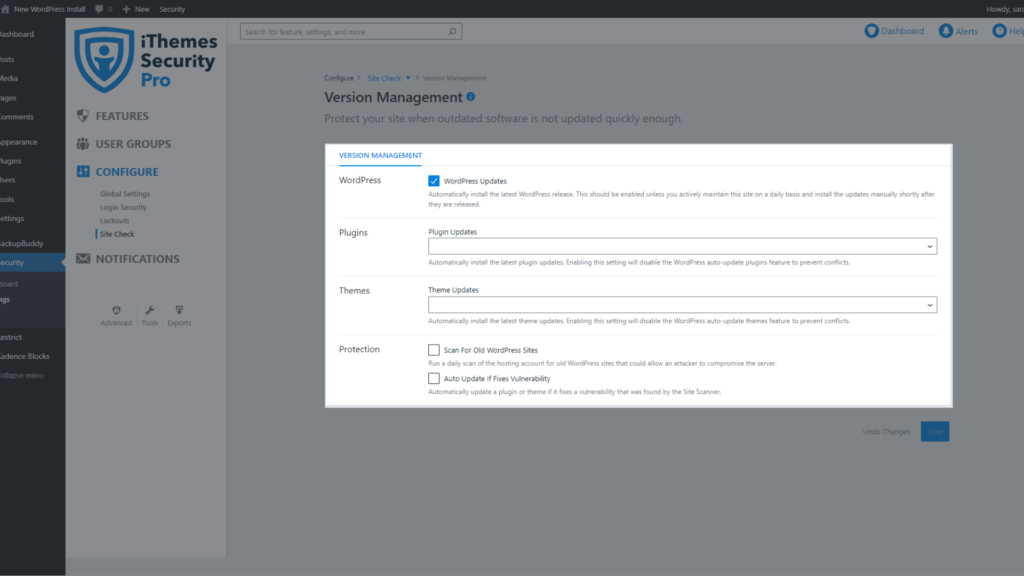
- WordPress Updates – Automatically install the latest WordPress release.
- Plugin Updates – Automatically install the latest plugin updates. Enabling this setting will disable the WordPress auto-update plugins feature to prevent conflicts.
- Theme Updates – Automatically install the latest theme updates. Enabling this setting will disable the WordPress auto-update theme feature to prevent conflicts.
- Strengthen Site When Running Outdated Software – Automatically add extra protections to the site when an available update has not been installed for a month.
- Scan For Old WordPress Sites – Run a daily scan of the hosting account for old WordPress sites that could allow an attacker to compromise the server. A single outdated WordPress site with a vulnerability could allow attackers to compromise all the other sites on the same hosting account.
- Auto Update If Fixes Vulnerability – This option works in tandem with the iThemes Security Pro Site Scan to check your website for known WordPress, plugin, and theme vulnerabilities and apply a patch when one is available.
3. Scan Your Site For Vulnerable Plugins and Themes
The iThemes Security Pro Site Scanner is another way to secure and protect your WordPress website from the number one cause of all software hacks: outdated plugins and themes with known vulnerabilities. The Site Scanner checks your site for known vulnerabilities and automatically apply a patch if one is available.
The 3 Types of WordPress Vulnerabilities Checked
- WordPress Vulnerabilities
- Plugin Vulnerabilities
- Theme Vulnerabilities
To enable the Site Scan on new installs, navigate to the iThemes Security Pro settings and click the Enable button on the Site Scan settings module.
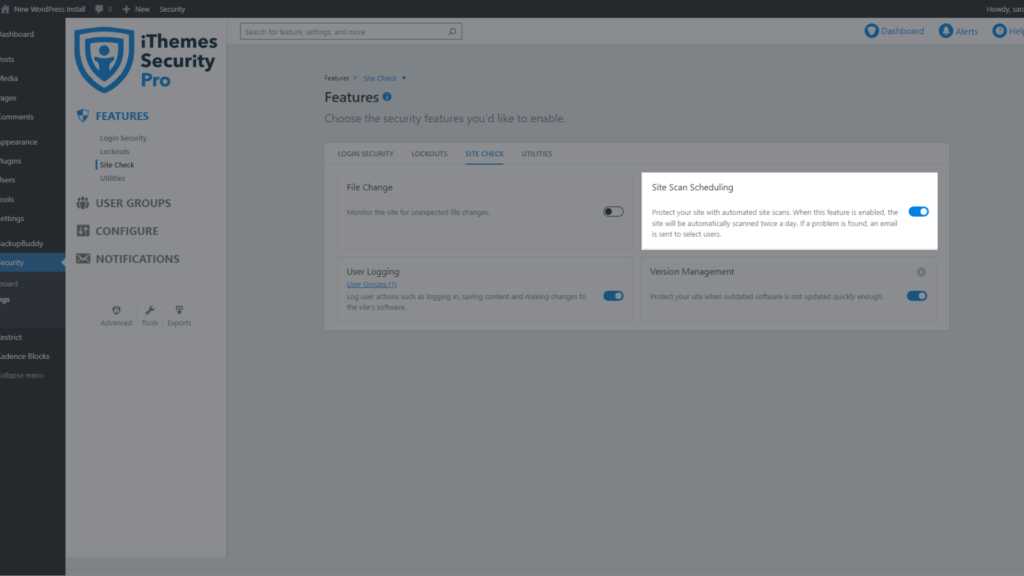
To trigger a manual Site Scan, click the Scan Now button on the Site Scan Widget located on the right side-bar of the security settings.
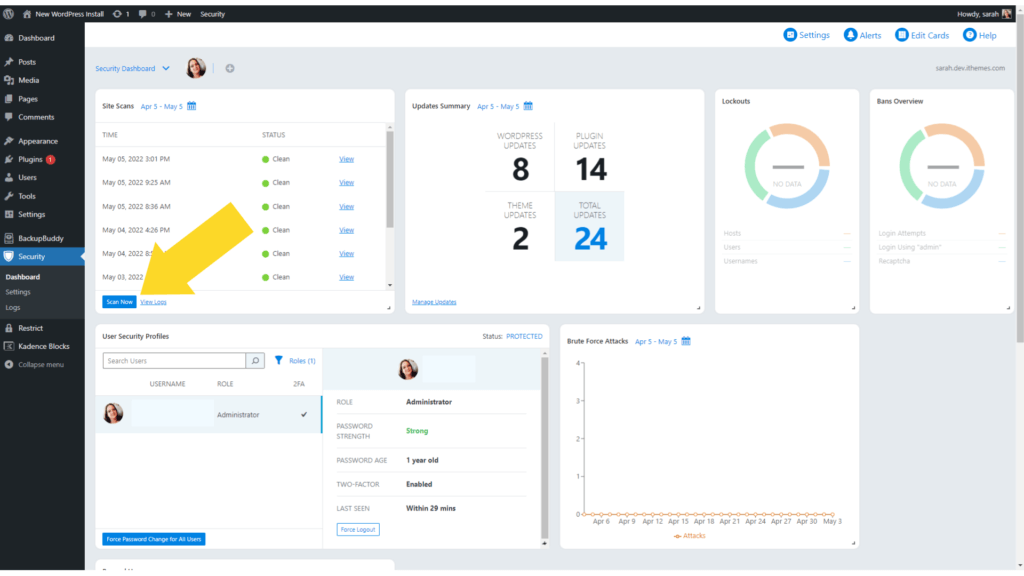
The Site Scan results will display in the widget.
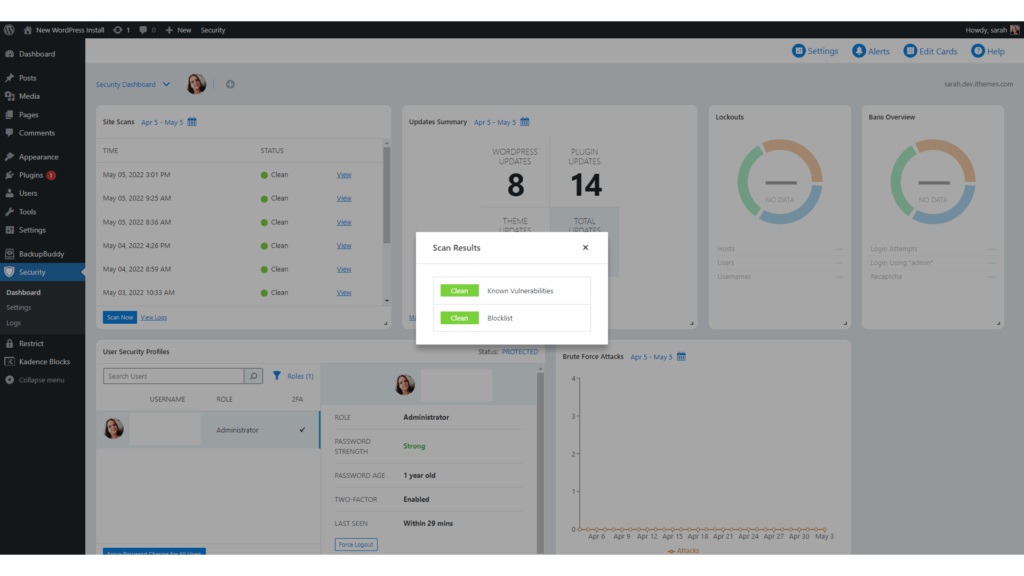
If the Site Scan detects a vulnerability, click the vulnerability link to view the details page.
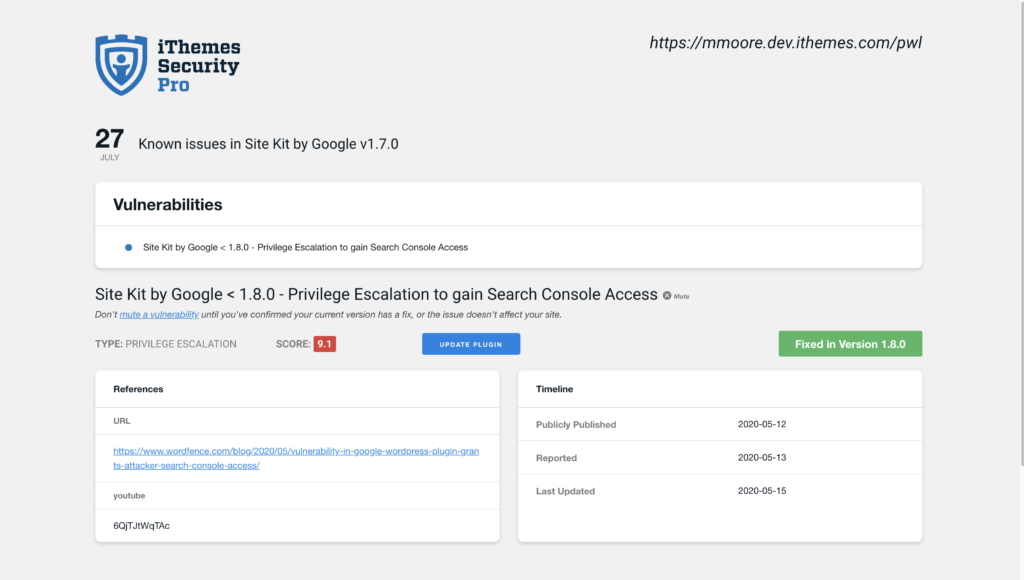
On the Site Scan vulnerability page, you will see if there is a fix available for the vulnerability. If there is a patch available, you can click the Update Plugin button to apply the fix on your website.
There can be a delay between when a patch is available and the iThemes Security Vulnerability Database getting updated to reflect the fix. In this case, you can mute the notification to not receive any more alerts related to the vulnerability.
4. Activate File Change Detection
The key to quickly spotting a security breach is monitoring file changes on your website. The File Change Detection feature in iThemes Security Pro will scan your website’s files and alert you when changes occur on your website.
There are several legitimate reasons you would see new file change activity in your logs, but if the changes made were unexpected, you should take the time to ensure the changes were not malicious. For example, if you see a change made to a plugin on the same date and time you updated the plugin, there would be no reason to investigate
To start monitoring file changes, enable File Change Detection on the main page of the security settings.
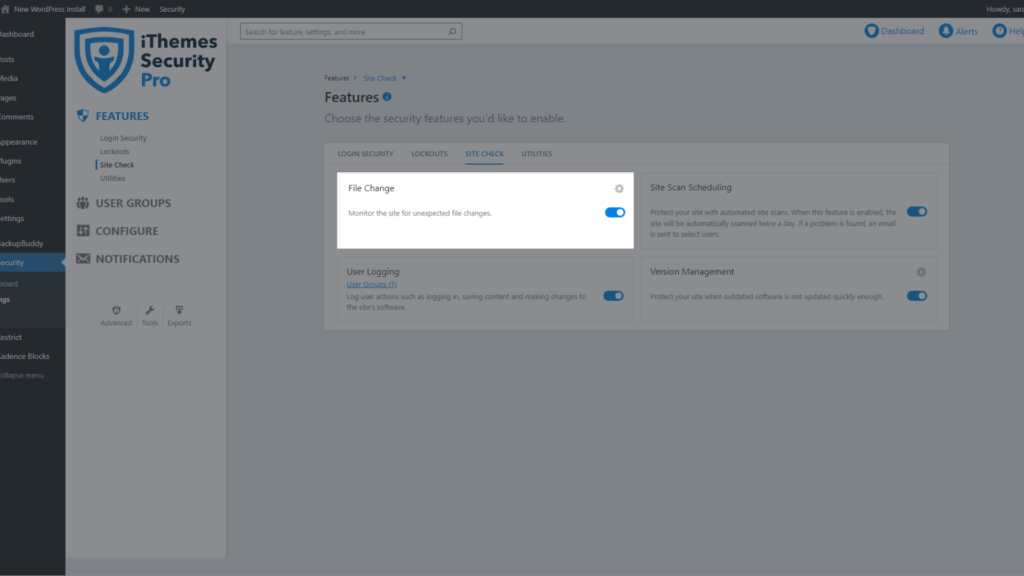
Once File Change Detection is enabled, iThemes Security Pro will start scanning all of your website’s files in chunks. Scanning your files in chunks will help to reduce the resources required to monitor file changes.
The initial file change scan will create an index of your website’s files and their file hashes. A file hash is a shortened, nonhuman readable version of the content of the file.
After the initial scan completes, iThemes Security Pro will continue to scan your file in chunks. If a file hash changes on one of the subsequent scans, that means the contents of the file have changed.
You can also run a manual file change by clicking the Scan Files Now button in the File Change Detection settings
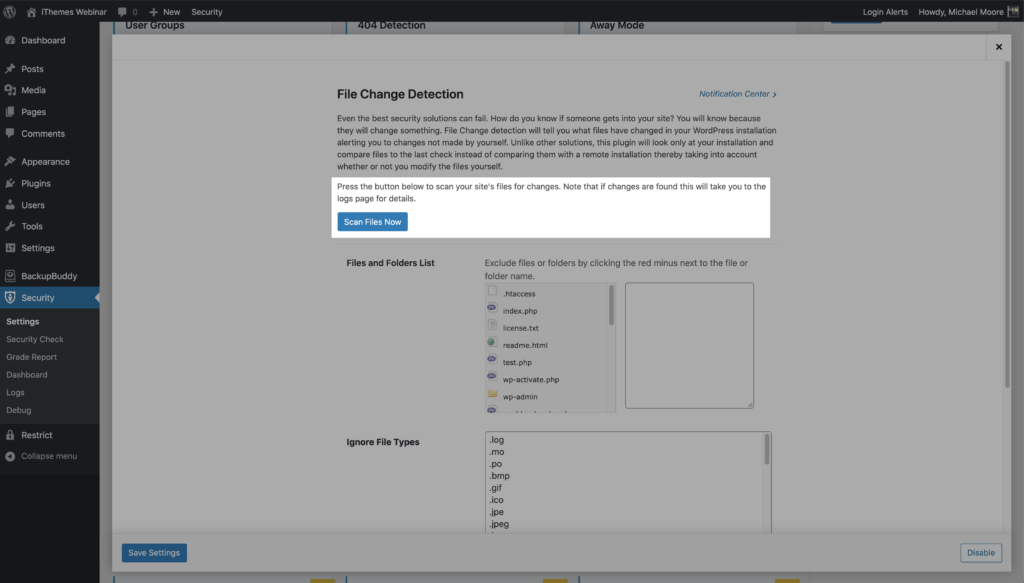
File changes happen all the time, and getting an email alert for every change would quickly become overwhelming. And before you know it, it becomes a boy who cried wolf situation, and you start ignoring the file change alerts altogether.
The good news is that iThemes Security Pro intelligently identifies legitimate changes to reduce notifications and how you can mute notifications for files that are expected to update frequently. You can manage all your iThemes Security notifications from the Notification Center within the iThemes Security plugin. From your WordPress admin dashboard, visit Security > Settings and locate the Notification Center module.
5. Turn on Two-Factor Authentication for Users That Make Changes to the Website
Two-factor authentication is a process of verifying a person’s identity by requiring two separate methods of verification. Google shared on its blog that using two-factor authentication can stop 100% of automated bot attacks. Not bad odds!
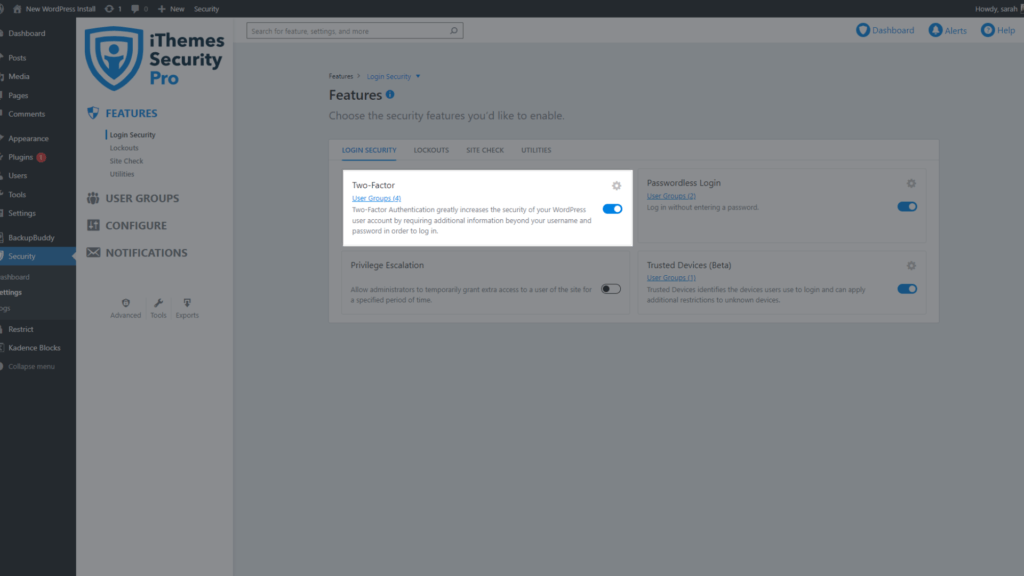
The iThemes Security plugin allows you to activate two-factor authentication for your WordPress site so users must enter a secondary code to log in.
The three two-factor authentication methods provided by iThemes Security Pro include:
- Mobile App – The mobile app method is the most secure method of two-factor authentication provided by iThemes Security Pro. This method requires you to use a free two-factor mobile app like Authy or Google Authenticator.
- Email – The email method of two-factor will send time-sensitive codes to your user’s email address.
- Backup Codes – A set of one-time use codes that can be used to login in the event the primary two-factor method is lost.
To start using Two-Factor Authentication on your website, enable the feature on the main page of the iThemes Security Pro settings.
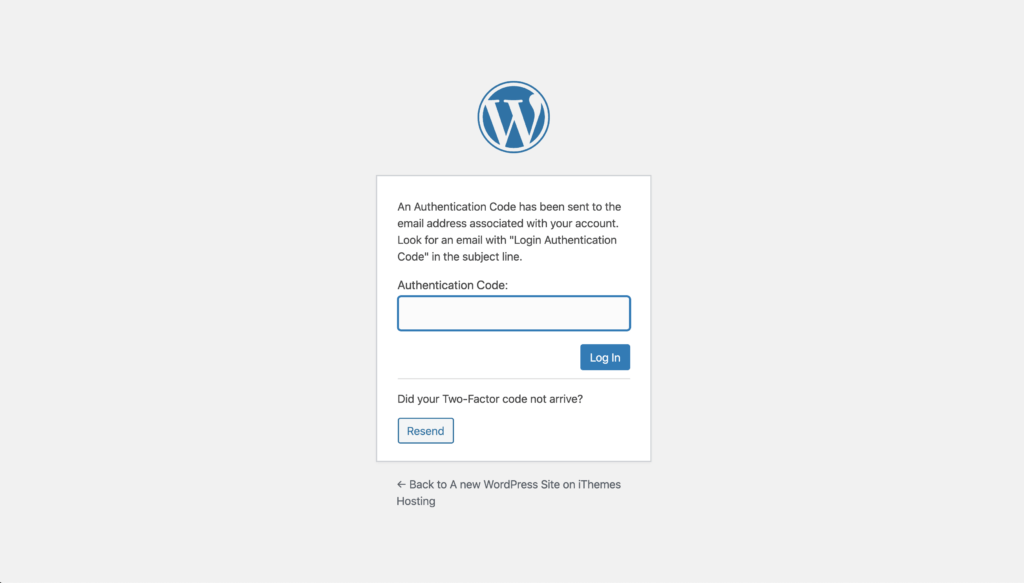
Follow the steps here to continue setting up two-factor authentication for your WordPress site. If you followed our recommendations and enabled the force requirements for privileged users, the next thing you will see is the place to enter the two-factor token.
Wrapping Up: To a Safer Web, Together
Don’t worry if you’re feeling a bit overwhelmed when you discover all of the potential security threats that are seeking out your WordPress site. The truth is that the threats are many, but the solutions can be simple.
We hope this guide helped you understand the risk of SQL injection attacks on your WordPress site. By implementing a few WordPress security best practices, along with the 5 steps above, you’ll have a better line of defense.
Solid Security is part of Solid Suite — The best foundation for WordPress websites.
Every WordPress site needs security, backups, and management tools. That’s Solid Suite — an integrated bundle of three plugins: Solid Security, Solid Backups, and Solid Central. You also get access to Solid Academy’s learning resources for WordPress professionals. Build your next WordPress website on a solid foundation with Solid Suite!
Sign up now — Get SolidWP updates and valuable content straight to your inbox
Sign up
Get started with confidence — risk free, guaranteed