What is a Website Backdoor? How to Remove and Prevent the Hack
If your WordPress website's login form is its front door, what is a website backdoor? As you might guess, it's a way to get in without using the front door. You never want anyone to be able to do this! Unfortunately, cyberattackers often are successful at creating backdoors on sites they've breached.
If your WordPress website’s login form is its front door, what is a website backdoor? As you might guess, it’s a way to get in without using the front door. You never want anyone to be able to do this! Unfortunately, cyberattackers often are successful at creating backdoors on sites they’ve breached. This allows them to keep coming back and doing more damage over time.
Attackers Will Keep Coming Through a Backdoor Until It’s Gone
Try to imagine for a moment that twelve months from now, your website has become so successful that your profits have doubled, and you’re finally getting some positive traction in your business. Suddenly all that momentum comes to a screeching halt when a hacker breaks in and installs a backdoor on your website. You think you’ve secured it, and then they’re back — adding spam links and malicious redirects, stealing sensitive customer data, or using your site for phishing to trick visitors into revealing their passwords.
This is a common story. When intruders compromise a web server’s file system, it’s almost certain they will install a backdoor before doing anything else that might alert you to their presence. This is why any indication of compromise (IOC) should lead site owners to search for backdoors.
If you’re unfamiliar with website backdoors and how to avoid or remove them, you may spend thousands of dollars and countless hours trying to repair the damage done by this type of hack. And that doesn’t even account for the lost revenue if your hacked website represents your business identity or serves as a key sales and marketing tool.
The Good News: There is a Cure for Website Backdoors
No website owner wants to live in constant fear of a malicious hack on their site, and we don’t want you to either. In this guide, we’ll show you how to secure your site so attackers never compromise it in the first place. If you have detected a backdoor on your site, we’ll walk you through the cleanup process. There are effective ways to secure your site so you never have to worry about backdoors.
What Is a Website Backdoor?
In a nutshell, a website backdoor is a hidden entry point that offers unrestricted, unauthorized access to your website to anyone who knows it’s there.
You may have difficulty determining if your site has a backdoor entry point. If someone has infected your site with a backdoor you’re unlikely to notice until they’re actively exploiting the backdoor. It’s likely a backdoor is present if you clean a hacked site, patch any vulnerabilities, and find it hacked again very quickly. There’s a good chance someone installed a backdoor in the past.
A backdoor is hard to detect because they tend to be unique, small, and well-hidden. It’s like the proverbial needle in a haystack. Some backdoor code and filenames look completely normal as if they’ve always been present on your site. Attackers camouflage their backdoors like this so they have a good chance of remaining open for future exploitation. They function as Trojan Horses — seemingly harmless until activated by an attacker.
How a Website Backdoor Infection Impacts Your Website
A website backdoor infection can lead to just about any kind of bad outcome for your website, its users, and your brand or organization. If your site becomes infected with a backdoor, you could see the following things happen:
- Clickjacking and malicious redirects send your visitors to malicious websites designed to defraud them or compromise their devices.
- Unauthorized popups appear on your web pages that ask your users to click and download software onto their devices that may harm them.
- Your site users begin to receive a bunch of spam emails from you/your site.
- You notice large files saved on your server that you didn’t authorize, such as pirated TV shows and movies.
- Cybercriminals steal sensitive information from your users’ accounts and distribute it on the dark web.
- Advertisements you don’t control or profit from hijacking your advertising spaces. Here’s a good recent example of this really bad backdoor.
- Your site’s search result ranking drops because Google identifies your site as compromised and dangerous.
- Your site’s search result ranking drops because it’s slow and riddled with spam links or spammy keywords injected into your content that search engines don’t like.
- Google blacklists your site and removes it from all search results.
- You lose your Google Adwords account.
- Your web host suspends your account and takes your site offline.
If you suspect attackers have compromised your site at all, assume they left a backdoor. You need to make a full search and remove any malicious code from your site as quickly as possible.
What Are Common Website Backdoors?
There are three kinds of backdoors:
- Simple backdoors
- Complex backdoors
- CMS-specific backdoors
Simple backdoors are brief code snippets that appear to be innocent and are extremely difficult to identify by sight.
Complex backdoors involve complex code and potentially multiple files a trained eye should recognize. These kinds of backdoors have functions that make them easy to distinguish from simple backdoors. Often a hacker will obfuscate complex backdoor code to make it difficult for malware scanners to detect them.
In a CMS-specific backdoor, a hacker will tailor their code to a specific Content Management System. These backdoors are specifically aimed at a single CMS, such as WordPress.
How To Find and Remove a Website Backdoor
You’ll need to thoroughly analyze your site’s code to remove a website backdoor manually. In most cases of backdoor infections, you’ll find the malicious code hidden within a PHP file on your server.
If you’re using WordPress as your content management system, the backdoor could be in any part of its file system:
- WordPress core files
- WordPress plugin files
- WordPress theme files
In some cases, backdoors can even be standalone files. Backdoor codes can be located in any directory that is web-accessible to the public. This makes them easy for hackers to access when they want to put a backdoor to use.
1. Make a Backup — and Label It with a Warning
If you suspect attackers have compromised your site, first create a full backup of its database and files. A WordPress backup plugin like BackupBuddy does this very well. Be sure to label this backup as possibly infected! You don’t want to trust this or any prior backups if their integrity is in doubt. However, if something goes wrong in the cleanup process, you do need a backup to fall back on.
2. Look for Unusual, Recently Added, or Changed Files
The File Change Detection feature in iThemes Security Pro will log and notify you about any new, changed, or deleted files in your WordPress folders or any others it’s monitoring. If you’re already using this feature, it will have picked up any backdoor code injection. If you’re not using this feature, you can start now, and you will catch any new malicious activity.
What might count as an “unusual” file? A good example is searchreplacedb2.php, part of a legitimate but poorly designed and widely used database tool. It has been widely used in WordPress and other CMS site migrations. Unfortunately, it runs outside of WordPress — it’s a single file you upload to your server, not as a plugin. That means someone only has to know where it is to operate it since it doesn’t require any login credentials of its own.
The features searchreplacedb2.php has can be used quite easily for malign purposes like injecting the site database with arbitrary code and content. Many people unwittingly used searchreplacedb2.php and left it on their servers! Attackers could simply search for its presence and use it to hack the site.
3. Verify and Restore the Integrity of Your Core Files
Monitor File Changes
In iThemes Security Pro, be sure to check the “Compare Files Online” box under Security › Settings › Configure › Site Check › File Change. Now you’ll receive an alert if anything changes or is out of order in your WordPress core, theme, or plugin files.

Verify WordPress Core Files are Authentic
If you’re an advanced user and are familiar with WP-CLI, you can use the wp core verify-checksums command to confirm all your core WordPress files are authentic and have not been modified. For less advanced users, the free AntiVirus plugin offers similar functionality through a simple interface in the WordPress administrator dashboard.
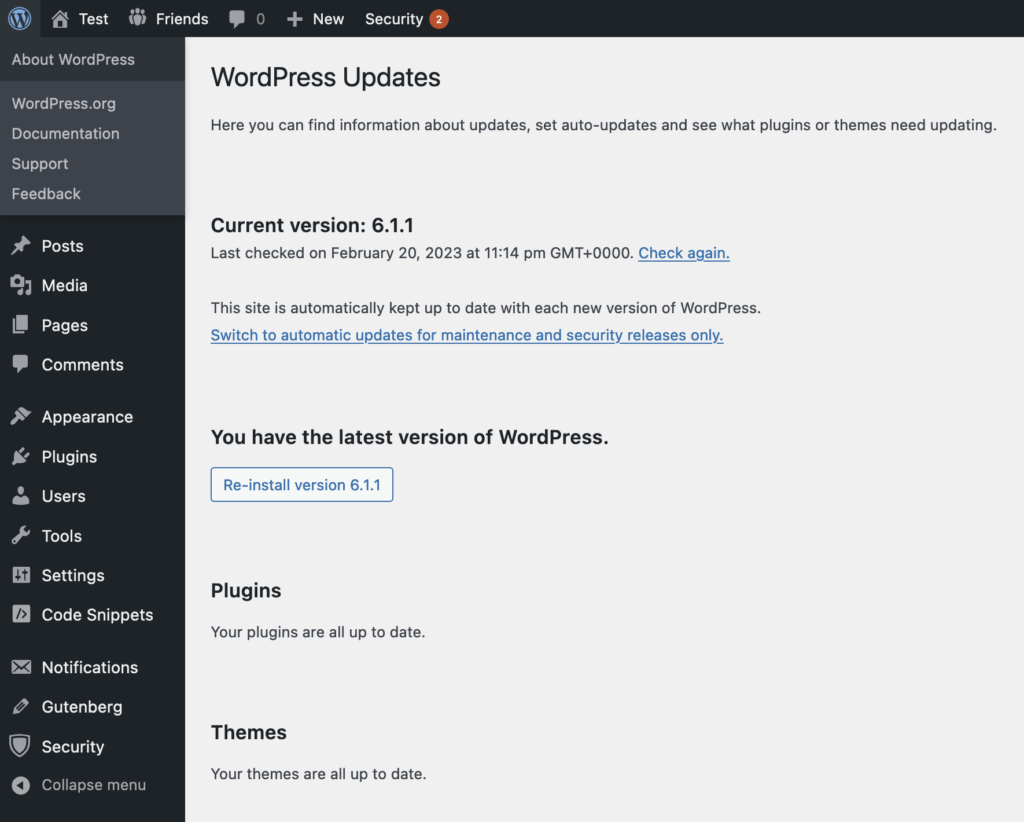
Force Reinstall Core, Theme, and Plugin Files
If any of WordPress’s core files have changed — or if you just want to refresh them all to be sure they’re clean — you can go to Dashboard › Updates in the WordPress administrator interface and click the “Re-Install” button. You can use the Force Reinstall plugin to do the same thing with your plugins and themes.
Review .htaccess and wp-config.php
Next, navigate to Security › Settings › Tools in iThemes Security Pro and run the tools that flush the server and WordPress config rules. Similar to force reinstalling other files, this is helpful in case the .htaccess and wp-config.php files have been compromised. These files contain settings for the Apache HTTP server and WordPress itself. Take a close look at them if you think they may have been altered by an intruder.
Force reinstalling all the things is a good way to ensure that WordPress core, theme, and plugin files are authentic. If you are using iThemes Security’s File Change Detection or similar tools, they may pick up differences between previously compromised variants of core, theme, and plugin files when you reinstall the official releases — a sign something wasn’t right. This may help you hone in on the location of a backdoor. However, a backdoor file outside the WordPress core, plugin, and theme file manifests could still be lurking within the legitimate files.
Change WordPress’s Encryption Salts
Finally, change the WordPress Salts. You’ll find a tool for doing this under Security › Settings › Tools in iThemes Security Pro.
You will force a logout for all logged-in users (including you) when you change salts. Salts are random cryptographic keys that harden the encryption of user login credentials. They’re stored in wp-config.php, so an intruder with access to your file system may have found them. It’s possible to use the salts to decrypt user login credentials.
4. Identify IP Addresses Accessing Suspicious Files and Backdoors
Review Web Access Logs
Finally, you’ll want to review your site’s raw HTTP access log files. By now you may have identified a suspiciously added or changed file with the help of the tools and procedures we’ve just discussed. In these files, you may see a common malware signature in the use of the PHP eval() function. Or, you may have found a web shell — a file manager that runs in the browser. A good example is WSO Shell, which has been used for many years to exploit websites that have been compromised. Once the shell code can be uploaded to your server, anyone using it can do just about anything to your file system — and potentially your WordPress database.
Take Filenames and Kick IP @ss!
Of course, you should delete these files if you find them — they’re malware — but make a record of their filenames first. Now you can search for those malware filenames in your server access logs and see who put them there, and who has been accessing them. “Who” in this case will be one or more IP addresses. You’ll find your logs in an appropriately named folder (like /logs/) on your server, above the web root. Your hosting account panel will have them available in a more accessible interface. Here’s where to find your HTTP access logs on a cPanel server.
Backdoor use normally shows up in access logs as POST HTTP requests to a specific file that doesn’t belong there. Once you’ve found one or more of those files, you want to find all requests to them — and their originating IP addresses. You can search through your logs for the IPs connecting to a backdoor and see what else the intruder has been up to. It may lead you to other backdoors. Repeat the process we’ve laid out here to track them all down. Add the intruder IPs to your blocklist in iThemes Security Pro.
How to Prevent Website Backdoor Hacks — and Other Unfortunate Events
Nearly all cases where a WordPress site is compromised are enabled by neglected software updates and other maintenance or a lack of basic security practices around user access and credential management.
1. Limit User Access Privileges
It’s incredibly important to be selective about the people who have elevated access roles and permissions on your WordPress site. Follow the principle of the least privilege: don’t give any user higher access privileges than they need.
WordPress will allow you to choose between six different user roles for each of your users. The roles are:
- Subscriber
- Author
- Contributor
- Editor
- Admin
- Superadmin (applies only to multisite accounts)
Before giving anyone site access, make sure you consider the role they should be given. Standard site users should be given roles that don’t have a lot of capabilities, such as Subscriber or Author.
Restrict site admin roles to only two or three people at the most, if possible. Using iThemes Security Pro, you can set up and enforce security policies for specific user groups. For example, you might require Administrators to use strong passwords, two-factor authentication, and/or passkey. You can offer multiple options to your users or require them to be used.
2. Harden User Authentication
After themes and plugins, your login page is your site’s next most vulnerable point. Because it’s the most vulnerable page on your entire website, it is important to address WordPress login security.
Through brute force attacks, bots will try hundreds or thousands of different login credentials within a few minutes to gain unauthorized access to your site. And they’ll keep trying until the correct login credentials are found.
Require Strong Passwords
Several different measures can be employed that can protect your login page from bots and hackers. Requiring strong passwords is one way to keep brute force attacks from succeeding. Using iThemes Security Pro, you can make strong passwords mandatory for your users.
Use Two-Factor Authentication
Beyond that, you can require two-factor authentication (2FA) for users. This will ensure that brute force attacks will never be able to succeed. Using iThemes Security Pro, you can require specific user groups (or all users) to set up 2FA.
Use Passkeys
Even better, use passkeys with iThemes Security Pro. Passkeys is the easiest and most secure way to log in to your WordPress site without the inconvenience of two-factor apps, password managers, or complex password requirements. Powered by the WebAuthn standard, passkeys include biometric login methods (like Apple’s Face ID, Touch ID, or Windows Hello) and are supported by all major browsers, including Chrome, Firefox, and Safari. Major tech companies like Google, Apple, and Microsoft all back the WebAuthn standard to make passkeys the future of secure logins across the web.
We’re proud to say iThemes Security Pro was the first WordPress security plugin to offer support for passkeys. As with 2FA, you can require specific user groups (or all users) to set up passkeys or simply provide it to them as an option.
Use a CAPTCHA
CAPTCHAs are another protection you may want to use to filter out bots that are attempting to log into your site or submit other form information. Using iThemes Security Pro, you can set up reCAPTCHA, hCaptcha, or Turnstile as an added security measure.
3. Keep Your Site Updated At All Times
Almost all vulnerabilities that can be exploited in WordPress sites emerge in a plugin. Usually, a simple update — often one that could’ve been made months or even years earlier — would have thwarted the attackers. A simple click of the “update” button!
Like any other software you use, WordPress core, themes, and plugins develop vulnerabilities over time. And when a core, theme, or plugin developer discovers new potential security vulnerabilities, they quickly work to release a repair patch through an update.
If you delay running these updates or fail to run them all together, your WordPress site is now vulnerable. Hackers are experts at finding and exploiting these weaknesses before they’re resolved.
By simply keeping the software you run on your WordPress site updated, you help ensure that your site remains secure. We cannot stress it enough: update your WordPress site!
Subscribe to our weekly security report to learn what core, plugin, and theme updates you need to make or look out for as new vulnerabilities are discovered. There are typically around 50 new vulnerabilities each week — out of an ecosystem of over 60,000 plugins, just counting those at wordpress.org.
Get SolidWP tips direct in your inbox
Sign up
Get started with confidence — risk free, guaranteed
4. Make It Hard to Access Your Site’s Filesystem
An intruder can only place a backdoor on your WordPress site if they have direct access to your server’s file system. By default. WordPress allows users with Administrator privileges to directly edit and add files within its install folder. Other plugins you add to your WordPress site may offer similar privileges. If they’re not needed, turn them off, or a stolen or guess admin password is all an intruder needs to take over your site.
Using iThemes Security Pro, it’s easy to lock down these exploitable features. After you’ve gone through the iThemes Security setup wizard, you should also deactivate the plugin and theme code editor. Then an intruder who gains administrator access can’t arbitrarily add or change code on your site.
Next, in the Security › Settings › Tools use the Check File Permissions tool to make sure the files and folders on your webserver have secure permission settings.
5. Never Use Nulled Themes and Plugins
A pirated or “nulled” plugin or theme is a premium product you download and use without paying for a license. While it may sound tempting to use premium themes and plugins for free, they come at a huge cost.
Nearly all pirated software is infected with website backdoors. When you install these products on your site, you immediately enable hackers to access your site without your knowledge or authorization.
And that is the motive for almost every publisher who puts pirated WordPress products on the market for download.
It’s crucial never to use any nulled WordPress plugins and themes on your site. If you currently have one (or more) installed, make sure to delete it from your site immediately. Then, use iThemes Security Pro to scan your entire site to ensure you aren’t running any other themes or plugins littered with malicious code.
6. Use Developers You Trust
If you need to hire a developer to build something custom for your site, they’ll need full admin access to complete the task. This means that you should only work with developers that you trust.
Some of the most trusted sources for hiring a WordPress developer include:
- Stack Overflow
- WordPress Jobs
- Codeable.io
- Smashing Jobs
- WPMU Dev Pros
You can rest assured that developers you hire from these sources won’t install any backdoor code on your site. It’s worth paying for quality and trust. Unqualified developers may write easily exploited, vulnerable code recycled from the web. Or they may leave behind unintentionally exploitable tools.
7. Use a Web Application Firewall
A Web Application Firewall (WAF) is an intelligent barrier between your site and incoming requests from users, some of whom are malicious hackers and bots.
Protecting Against Website Backdoors
The best step you can take right now to avoid damage from a backdoor hack is to download and install the iThemes Security Pro plugin for WordPress.
iThemes Security Pro will scan your site for malicious activity 24/7 while enabling you to employ the site-hardening measures needed to avoid backdoors. And if your site is ever hacked, the plugin will walk you through the best ways to clean it up before any more damage can be done.
Keep your WordPress site safe from hacks and malicious attacks by using the iThemes Security Pro plugin. Your future self will thank you.
Get SolidWP tips direct in your inbox
Sign up
Get started with confidence — risk free, guaranteed
Solid Security is part of Solid Suite — The best foundation for WordPress websites.
Every WordPress site needs security, backups, and management tools. That’s Solid Suite — an integrated bundle of three plugins: Solid Security, Solid Backups, and Solid Central. You also get access to Solid Academy’s learning resources for WordPress professionals. Build your next WordPress website on a solid foundation with Solid Suite!
Sign up now — Get SolidWP updates and valuable content straight to your inbox
Sign up
Get started with confidence — risk free, guaranteed
