What is a WordPress Pharma Hack?
One of the most common techniques for hacking a website involves manipulating search indexes to include undeserving content in high search positions. This is a type of Black Hat SEO hack, also known as a WordPress pharma hack, or SEO spam. For millions of website owners worldwide, WordPress is the best solution for creating e-commerce stores and every other kind of website.

One of the most common techniques for hacking a website involves manipulating search indexes to include undeserving content in high search positions. This is a type of Black Hat SEO hack, also known as a WordPress pharma hack, or SEO spam.
For millions of website owners worldwide, WordPress is the best solution for creating e-commerce stores and every other kind of website. And because of the popularity of the WordPress CMS, it’s a frequent target for malicious attacks and hacks. But what exactly is a WordPress pharma hack?
In this guide, we’ll discuss the details of what a WordPress pharma hack is, some prominent examples of what this type of attack looks like, and how to prevent them. Let’s take a look.
What is a WordPress Pharma Hack?
In a nutshell, a WordPress pharma hack is a hacking technique that uses malware to infect a legitimate WordPress site to redirect to spam web pages that showcase ads selling knock-off versions of branded pharmaceuticals, such as Cialis and Viagra.
At times, these hacks will direct to other types of pharmaceutical products. But Cialis and Viagra are by far the most common.
A pharma hack is a type of Black Hat SEO hack or SEO spam.
Get SolidWP tips direct in your inbox
Sign up
Get started with confidence — risk free, guaranteed
Why Do Hackers Exploit WordPress Sites With Pharma Hacks?
There’s a simple answer to why hackers target WordPress sites with pharma hacks: Searches online are a huge source of traffic referrals. An SEO hack is the easiest way to bring in a lot more referral traffic without putting in the work to generate traffic organically.
A WordPress pharma hacks ensures that the hacker has a prominent place in the SERPs (Search Engine Results Page) by hacking into sites with high search authority, then infecting them with spam redirection hacks.
What Does a WordPress Pharma Hack Look Like?
In a recent WordPress pharma hack, we witnessed a very sophisticated version of what the hack looks like. In this pharma attack, the hacker tailored Google search results directly with the name of a website within the title.
By doing this, people genuinely believe they are clicking on a legitimate website that sells legal pharmaceuticals.
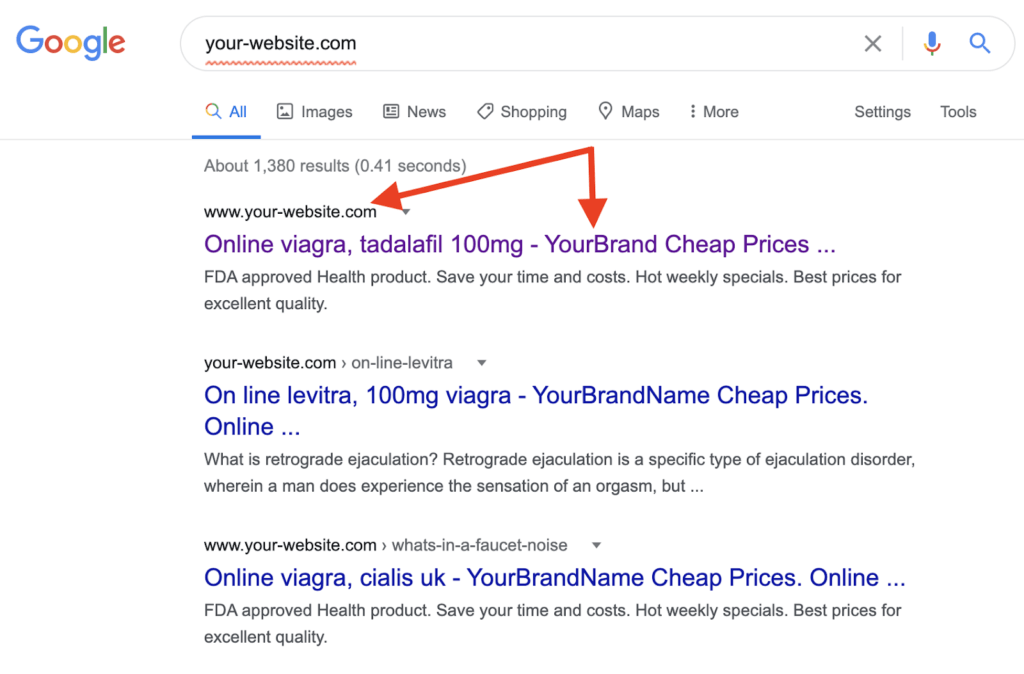
As you can see, the hack makes it appear that you are about to click on a legitimate pharmaceutical ad, when you’re really clicking on spam.
How To Know If Your WordPress Website Is Infected By a Pharma Hack
Without knowing what you’re looking for, it’s difficult to detect SEO spam because it’s not immediately visible if you’re a WordPress administrator or website manager. Good hackers know how to hide what they’re doing by following practices such as cloaking.
However, there are some simple tricks and tools that you can employ that will uncover whether your site has been infected with a pharma hack.
1. Use a WordPress Security Plugin
As a responsible WordPress site owner, it’s important to understand that the security of your site is of the utmost importance. If you’re running a site that isn’t fully secured by a powerful WordPress security plugin suite, you’re putting your entire site, and your users, at the risk of a potential cybersecurity attack.
A good WordPress security plugin needs to be powerful, completely up-to-date, and easy for website owners to use.
And the iThemes Security Pro plugin is a great solution. iThemes Security has a powerful Site Scan feature that integrates with Google Safe Browsing to show if your site is listed on Google’s Blocklist, which usually indicates you have some type of malware on your site.
iThemes Security also offers file change detection, which is a powerful way to monitor any file changes on your site. Hackers usually modify or change files on your site, so keeping a log of these changes (and getting alerts when files change) can help indicate something suspicious has happened, what was changed, and when it happened.
2. Check Google Search
To find infected websites, search keywords such as viagra wp-page. Keep in mind that, because of Google’s webmaster policies, infected sites won’t be shown on the first results page. You’ll need to scroll to pages three and four at least.
If you see your website in the search, this means your site is a victim of a WordPress pharma hack or other black hat SEO spam.
You’ll notice that the list includes infected sites as well as fake pages. If you click on these pages, you’ll likely be redirected to other pages. Or, the spam content may load on the legitimate website’s page as a result of the infection.
To find out if any of your site’s pages are infected with SEO spam for Viagra, simply add the word “viagra” to your domain name in a Google search (viagra site:yourdomain.com).
Often, only a couple of pages of your site will be infected. And those pages aren’t visible to you in your WordPress dashboard. By doing this search, you’ll uncover what those infected pages/URLs are.
3. Check Results As Google Bot
As discussed, these pharma spam pages aren’t visible on a standard search engine. But a user agent, such as Googlebot, can see and detect them.
To view what Googlebot sees, simply use a browser User-Agent Switcher which can be installed on Firefox or Chrome.
Here’s how:
- Install a User-Agent Switcher add-on
- Navigate to the infected webpage
- Edit the User-Agent string to any of the ones given below:
Mozilla/5.0 (compatible; Googlebot/2.1; +http://www.google.com/bot.html)Googlebot/2.1 (+http://www.google.com/bot.html)
- Right-click on the page and view the page source. This will enable you to see the redirect
Keep in mind that if you have the User-Agent Switcher active for too long, you may get blacklisted or blocked from sites that maintain good security protocols. This is because, to them, you’ll appear as Googlebot.
The Anatomy of a WordPress Pharma Hack
Now, let’s break down the actual anatomy of what happens during a WordPress pharma hack.
1. Your Vulnerability to a Pharma Hack
To pull off this type of hack, the hacker must first exploit a known vulnerability or a zero-day exploit.
Some of the most common vulnerabilities include:
- SQL injections of XSS. These happen because of poor software coding standards within the theme or the plugins you run. Sometimes, these issues even occur in the WordPress core software. Always keep the software you run on WordPress completely up-to-date, including your plugins and themes.
- Weak FTP and account passwords. Strong passwords are absolutely essential if you’re a WordPress site owner. And this applies to websites of all sizes. Even the GitHub repository of Linux Gen was recently hacked due to weak login credentials.
- Error display and content listing is enabled. As a result, your site’s critical files are openly readable by anyone on the Internet.
2. The Persistence of a Pharma Hack
A WordPress pharma hack succeeds by altering your root directory’s contents. And most spam attacks will happen through your /includes or /misc folders.
A spammer will gain persistence, or prolonged access, using methods such as:
- Adding new pages such as
leftpanelsin.php,cache.php, etc. - Modifying PHP files such as
index.php,wp-page.php,nav.php, etc. - Hiding the spam files inside
/imagesfolder. Web crawlers don’t expect to see files here, which keeps them from being detected. - Obfuscating code using base64 encoding
- Editing
xmlrpc.phpto avoid detection by webmasters - Using cron jobs to reinfect
- Cloaking: Differentiating between web crawlers based on user-agent. The result is that the content seen by Googlebot is different than the content a Mozilla user sees.
- Appending dot before the file extension. Therefore, renaming the page as
.otherfilein order to be invisible.
3. The Results of a Pharma Hack
What happens to you, as a WordPress site owner, when a hacker succeeds at a pharma hack on your site?
- Your site will lose its good reputation, as it will now be displaying Cialis and Viagra ads.
- You’ll likely be blocklisted by Google, which means it’ll be very difficult to regain your site’s reputation.
- Users will no longer trust your site and won’t return.
- Search engine rankings will plummet.
- Your site will be generating clicks to other sites. The same clicks you’ve worked so diligently to earn will be going elsewhere.
Obviously, all of these results are detrimental to your website and your business.
Fixing a WordPress Pharma Hack
Pharma hacks are hidden. As such, searching for, and removing a WordPress pharma hack, can be a long and tedious process.
Here’s what to do:
1. Backup Your Site
To ensure that you don’t lose all the work you’ve put into your site, download the BackupBuddy plugin and make a complete backup of your core files, database, and theme and plugin files. Yes, even the malware. Trust us, you’ll be glad you have this is anything goes wrong during the cleanup process.
Obviously, it helps if you have a backup of the “clean” version of your site prior to the pharma hack, so be sure to implement backups as a preventative security measure.
2. Scan For Vulnerabilities, Known Malware, and Your Google Blocklist Status
Use the iThemes Security Pro plugin discussed earlier to run a full scan of your site. The Site Scan feature scans your WordPress core version, plugins, and themes for any known vulnerabilities that may have opened a backdoor for the attack. In addition, Site Scan integrates with Google Safe Browsing which indicates if Google has found any known malware on your site. If so, your site will be added to Google’s blocklist. iThemes Security will show your Google Blocklist status.
3. Remove Infected Files
Use an FTP client to connect to your hosting server. Alternatively, you can use a file manager.
Navigate to /wp-content/ folder and look for the hacked plugins and files. Files that are hacked will include words such as .cache, .class, or .old that are used to camouflage them as legitimate plugin files.
Remember that a dot placed at the beginning of a file name makes them hidden. So make sure you have the “show hidden files” option selected when doing this.
When you file these files, remove them.
Check out our full post, downloadable checklist and video on how to clean a hacked WordPress site.
4. Clean Your .htaccess File
The .htaccess file is a high-level configuration file for the server that defines how server requests get processed.
A hacker is able to use this file to create website backdoors. In the .htaccess file, look for any code that looks like this:
RewriteEngine On
RewriteCond %{ENV:REDIRECT_STATUS} 200
RewriteRule ^ - [L]
RewriteCond %{HTTP_USER_AGENT} (google|yahoo|msn|aol|bing) [OR] #checks for Google, Yahoo, msn, aol and bing crawler
RewriteCond %{HTTP_REFERER} (google|yahoo|msn|aol|bing)
RewriteRule ^(.*)$ somehackfile.php?$1 [L] #redirects to a hack file
Rename the current .htaccess file. Then, to completely regenerate the .htaccess file, simply head to your WordPress dashboard, navigate to Settings, then select Permalink and click save.
5. Remove Malicious Code In the Database
This is a step you should not undergo until you have a full site backup in place using the BackupBuddy plugin.
After that’s done, you can manually clean your database with these steps:
- Go to phpMyAdmin
- Select the database
- Click on
wp_optionstable - Use the Search tab to look for malicious entries
A sampling of possible malicious entries to search for are:
fwpwp_check_hashclass_generic_supportwidget_generic_supportftp_credentials
Remember to be extremely careful to not delete anything important from your wp_options table. This could cause your site to severely malfunction or completely crash.
Of course, if you’re not comfortable digging this far into your site, it’s best to seek an expert’s help.
6. Find and Remove Code That’s Suspicious
Suspicious code is a major cause of WordPress website hacks. Suspicious code will look something like:
<ul id="menu"> <li><a href="hackerdomain.com">Something2</a></li>
Code like this will redirect your site to a domain that’s controlled by the attacker. It’s important to check for any domains in your site’s code that shouldn’t be there.
Most often, a hacker will hide their code in base64. This helps them avoid being detected. What this means is that, instead of seeing their website URL (hackerdomain.com), it instead will look something like YXR0YWNrZXJkb21haW4uY29t.
Or course, this makes the suspicious code more difficult to detect. To search for these base64 encodings in your files, it’s helpful to use the grep command:
find . -name "*.php" -exec grep "base64"'{}'\; -print &> b64-detections.txt
This code searches the .php files you choose for base64 encodings. Afterwards, the results are stored in b64-detections.txt.
Once you have that file, search for an online resource that will decode them so you can find out what’s happening on your site behind the scenes.
7. Scan for Content Differences
The iThemes Security Pro plugin can be used to monitor any file changes on your site, and will compare your WordPress core files and third party files in the WordPress repository for unusual or suspicious entries and file names.
After determining which of your files have been hacked, you can either delete the infected code or restore your plugin files. It’s very important to completely clean the code of your site. Malicious code that gets left behind could quickly cause your site to be reinfected.
8. Restore Your Site’s Reputation
Now that you’ve cleaned your site, you’ll need to do triage on your site’s reputation with Google.
Simply cleaning and restoring your hacked WordPress site won’t automatically restore the reputation of the site. In fact, there are several things you’ll need to do to make sure that Google and the other search engines don’t continue to penalize your site after it’s been hacked and cleaned.
Often, the first sign you’ll have that your site has been hacked is that Google informs you of the situation. In order to see how Google is currently viewing your site, head to the Google Search Console.
If you find any extraneous Sitemaps in the Search Console that shouldn’t be there, or seem to be putting out spam links, you’ll want to delete those immediately. After this, you’ll want to take a look at any security issues that exist in the Search Console. If the big red screen of doom and gloom from Google is currently being shown, you’re going to see some big flags in the Search Console under Security Issues.
This is where you will request that Google reviews your website now that it’s been cleaned.
Preventing a WordPress Pharma Hack
If you ever find areas of your site that are impacted by this type of hack, work through the steps we’ve detailed in this guide to resolve the issue as quickly as possible. Now that you’re aware of what a pharma hack on WordPress is and how to make sure your site isn’t impacted, it’s time to get to work to harden your site against any future attacks.
1. Install and Activate the iThemes Security Pro plugin
Start off by downloading and installing the iThemes Security Pro plugin to determine if your site has been infected. The plugin adds multiple layers of website security by monitoring file changes, increasing user security, scanning your plugins and themes for vulnerabilities (and then automatically updating them for you), and providing online file comparisons that may indicate a hack.
At a minimum, enable the following settings within the iThemes Security plugin:
- Enable two-factor authentication to all admin users.
- Enable iThemes Site Scan to scan your website twice a day for vulnerable plugins, themes & WordPress core versions.
- Turn on Version Management with automatic vulnerability patching.
- Turn on File Change Detection
2. Install and Activate the BackupBuddy plugin
Having a backup strategy for your website is a crucial part of preventing future hacks. A backup means you have a copy of your website at a certain point in time, like before a hack occurred. Having this backup means you can easily restore your site to a previous version. (Just be sure to shore up any vulnerabilities or website backdoors) that exist in that version of your site or the hack could occur again.
3. Use Website Security Best Practices
As a website manager, admin, or owner, your online security will impact your website’s security.
For example:
- Never reuse passwords for multiple accounts.
- Never share your passwords with others.
- Use two-factor authentication for your WordPress admin login.
- Never install nulled WordPress plugins or themes.
- Keep your WordPress core version, plugins, and themes updated to the latest versions.
- Use a reputable web host with solid server security.
- Use a WordPress security plugin and backup plugin.
4. Stay Vigilant About Your Website’s Security
Research shows that the average time it takes to find a security breach or hack is 200 days! Neglected sites are often the most vulnerable to these types of hacks, so make a point to check in your site’s security and performance even if you have sites you don’t often log into.
Simply checking in on how your site looks, reviewing security logs, and making sure all your themes, plugins, and WordPress core versions are up-to-date will go a long way in preventing a WordPress pharma hack. Armed with the knowledge of how to secure your site and with a few tools to help do the work, your site is more likely to stay safe and secure .
Secure & Protect Your Site from Hacks & Security Breaches
WordPress currently powers over 40% of all websites, so it has become an easy target for hackers with malicious intent. The iThemes Security Pro plugin takes the guesswork out of WordPress security to make it easy to secure & protect your WordPress website. It’s like having a full-time security expert on staff who constantly monitors and protects your WordPress site for you.
Sign up now — Get SolidWP updates and valuable content straight to your inbox
Sign up
Get started with confidence — risk free, guaranteed